![]() [German]Check Point Threat Intelligence and research teams recently discovered a high volume Chinese threat operation, named Fireball, which has infected over 250 million computers worldwide.And it seems that 20% of enterprise networks contains this Fireball backdoor. Here is, what Check Point told me within a written briefing note.
[German]Check Point Threat Intelligence and research teams recently discovered a high volume Chinese threat operation, named Fireball, which has infected over 250 million computers worldwide.And it seems that 20% of enterprise networks contains this Fireball backdoor. Here is, what Check Point told me within a written briefing note.
Advertising
What is Fireball?
Fireball is primary adware, it takes over target browsers and turns them into zombies. But Fireball has two main functionalities:
- the ability of running any code on victim computers–downloading any file or malware,
- and hijacking and manipulating infected users' web-traffic to generate ad-revenue.
Currently, Fireball installs (according the Check Points investigations) plug-ins and additional configurations to boost its advertisements. But Check Points says, this just adware/malware can turn easily into a prominent distributor for any additional malware.
Who has developed Fireball?
The threat operation is run by Rafotech, this is a large digital marketing agency based in Beijing, China. Fireball is used to manipulate the victims' browsers and turn their default search engines and home-pages into fake search engines. This redirects the queries to either yahoo.com or Google.com.
The fake search engines include tracking pixels used to collect the users' private information. Fireball has the ability to spy on victims, perform efficient malware dropping, and execute any malicious code in the infected machines, this creates a massive security flaw in targeted machines and networks.
Check Points key findings
Security researchers from Check Point has published the following key findings about the Fireball thread operation.
Advertising
- The malware, called Fireball, acts as a browser-hijacker but and can be turned into a full-functioning malware downloader. The operation is run by Chinese digital marketing agency.
- Fireball is capable of executing any code on the victim machines, resulting in a wide range of actions from stealing credentials to dropping additional malware.
According to Check Point's analysis, over 250 million computers worldwide have been infected. Here are a few numbers:
- 25.3 million infections in India (10.1%),
- 24.1 million in Brazil (9.6%),
- 16.1 million in Mexico (6.4%),
- 13.1 million in Indonesia (5.2%)
- 5.5 million in United States (2.2%)
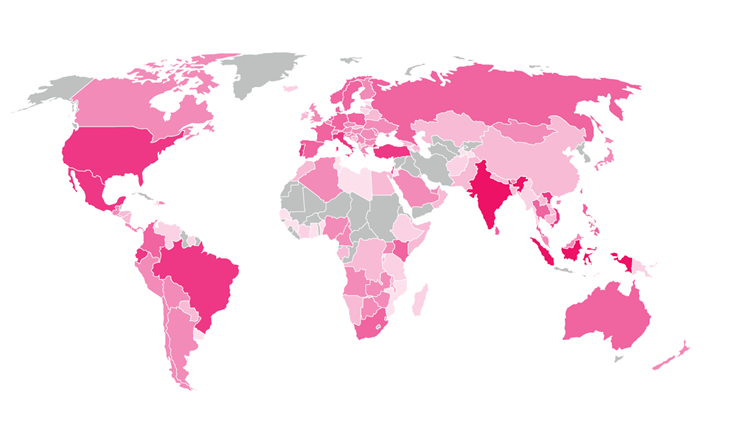
(Source: Check Point – Fireball Global Infection Rates (darker pink = more infections)
Based on Check Point's global sensors, 20% of all corporate networks are affected . Hit rates in the US (10.7%) and China (4.7%) are alarming; but Indonesia (60%), India (43%) and Brazil (38%) have much more dangerous hit rates.
Although Rafotech doesn't admit it produces browser-hijackers and fake search engines, it does (proudly) declare itself a successful marketing agency, reaching 300 million users worldwide
How Fireball is beeing spread?
Fireball is spread mostly via bundling i.e. installed on victim machines alongside a wanted program, often without the user's consent.
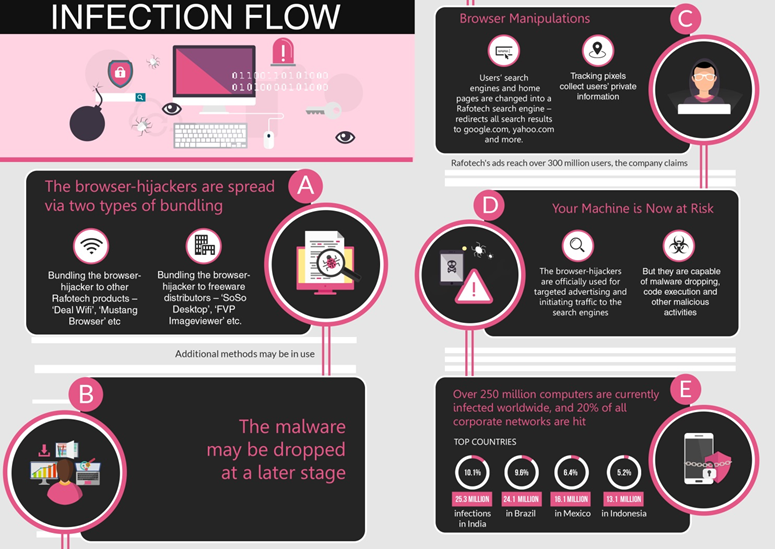
(Source: Check Point – Fireball Infection Flow)
Check Point suspects that two popular vectors are bundling the malware to other Rafotech products – Deal Wifi and Mustang Browser – as well as bundling via other freeware distributors: products such as "Soso Desktop", "FVP Imageviewer" and others.
It's important to remember that when a user installs freeware, additional malware isn't necessarily dropped at the same time. If you download a suspicious freeware and nothing happens on the spot, it doesn't necessarily mean that something isn't happening behind the scenes.
Check Point writes, that it is likely that Rafotech is using additional distribution methods, such as spreading freeware under fake names, spam, or even buying installs from threat actors. Further details may be read at Check Point's blog post FIREBALL – The Chinese Malware of 250 Million Computers Infected







