![]() [German]There is a vulnerability in Microsoft's Remote Desktop Protocol (RDP) that can be exploited to break out of guest VMs running on Hyper-V in Windows 10/Azure.
[German]There is a vulnerability in Microsoft's Remote Desktop Protocol (RDP) that can be exploited to break out of guest VMs running on Hyper-V in Windows 10/Azure.
Advertising
As early as February 2019, Check Point's Eyal Itkin published the technical details of the bug as part of a larger study covering several RDP vulnerabilities (Bleeping Computer had reported here).
RDP server accepts client's clipboard
The focus of the study was on a reverse RDP attack. The server of a remote connection takes control of the client. This was possible because two machines connected via RDP share the clipboard. This allows everything copied on the remote server to be pasted on the local client.
Microsoft delays the patch
The error allows a path traversal approach leading to remote execution. The vulnerability was reported to Microsoft almost a year ago. Initially, Microsoft confirmed the vulnerability, but refused to fix it. Reason: The vulnerability is not serious enough to require an immediate response.
Bleeping Computer reports here, that this decision catched Microsoft on the wrong foot. A connection between virtualization and remote desktop technology is not obvious. But Hyper-V has a connection.
Hyper-V also affected
When Advanced Session Mode is enabled, the same settings window becomes available for both a Hyper-V virtual machine and a remote connection through Microsoft's RDP client (mstsc.exe).
Advertising
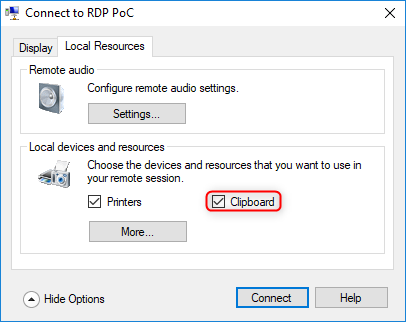 (Source: Microsoft)
(Source: Microsoft)
The settings window is also used to synchronize the clipboard and is turned on by default.
Escape from the Hyper-V Guest
Itkin therefore used the same script he had written for attacks on the RDP vulnerabilities. The researcher managed an escape from the Hyper-V guest to the host.
(Source: YouTube)
The PoC video above shows how easy an attack is. By inserting a file on the host of the Hyper-V machine, the attacker can add a malicious file to the host's startup folder to ensure execution at the next reboot.
After Itkin told Microsoft of its new findings about the vulnerability (CVE-2019-0887), the fix began with July 2019 updates. If the update cannot be installed immediately, clipboard activity monitoring should be disabled. See at Bleeping Computer for details. Security researchers from CheckPoint has also published an article Reverse RDP Attack Also Enables Guest-to-Host Escape in Microsoft Hyper-V about that topic.







