[German]A Microsoft software developer has accidentally shared internal PlayReady source code with the public (a developer forum). The data leak of 4 GByte is sufficient to compile the required DLL from the source code. This could be a real boon for people who want to reverse engineering or crack PlayReady.
[German]A Microsoft software developer has accidentally shared internal PlayReady source code with the public (a developer forum). The data leak of 4 GByte is sufficient to compile the required DLL from the source code. This could be a real boon for people who want to reverse engineering or crack PlayReady.
Advertising
What is PlayReady?
PlayReady is a copy protection technology for media files from Microsoft that includes encryption, output protection and digital rights management (DRM). It was announced in February 2007 and the first version was released in 2008. The main differences to previous Microsoft DRM systems are:
- Some popular features that were already present in other DRM systems on the market have been added. These include the concept of domain (group of devices owned by the same user that can share the same licenses), embedded licenses (licenses embedded in the content files, avoiding a separate step for license acquisition) and envelopes (the ability to DRM any content that may not be media-related). It is also the protection scheme for IIS Smooth Streaming, Microsoft's adaptive streaming technology.
- It is platform independent: Unlike other Microsoft DRM schemes such as Janus, PlayReady can be ported to any type of portable device, even if it uses a non-Microsoft technology (operating system, codecs, media player, etc.).
PlayReady competes with other proprietary DRM systems and even more so with DRM-free software, most notably Apple's FairPlay introduced in iTunes and QuickTime.
The PlayReady source code leak
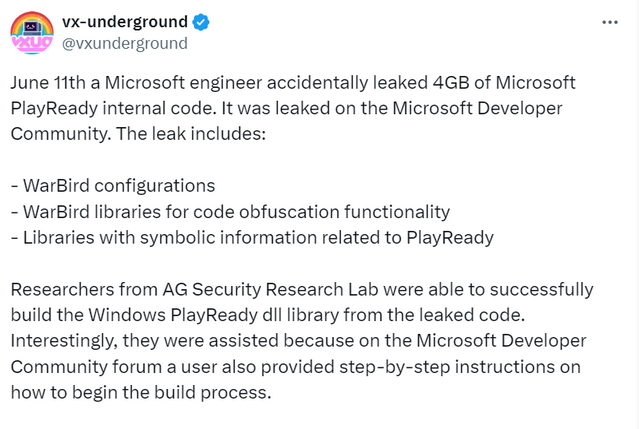
I just came across the topic on X via the following tweet. It states that a Microsoft engineer accidentally published 4 GB of internal Microsoft PlayReady code to the Microsoft Developer Community on June 11, 2024.
There is also a post on the subject on securelists.org. The Microsoft engineer has posted in a public forum information about a crash of the Apple TV service on a Surface Pro 9 device. The post included a 771 MB file attachment that included 4 GB of internal code when unzipped (more than 260 files) related to Microsoft PlayReady. The leak includes:
Advertising
- the WarBird configurations for creating the PlayReady library
- WarBird libraries for code obfuscation functions
- Libraries with symbolic information in connection with PlayReady
This is key information about PlayReady internals and implementation. Researchers from AG Security Research Lab have managed to build the Windows PlayReady dll library from the leaked code. Interestingly, they were aided in doing so because a user in the Microsoft Developer Community Forum also provided step-by-step instructions for the build process.
Interestingly, the Microsoft Symbol Server also does not block requests for PDB files that correspond to Microsoft WarBird libraries, which has inadvertently made more information public. The security researchers informed Microsoft about the leak on June 12, 2024, whereupon the forum post was removed. The tweet links to a file list and contains screenshots of the whole thing. There is already information about WarBird Obfuscation on GitHub. And an analysis can be found here.
Advertising