 [German]Windows 11 is, according to Microsoft, already the "most secure operating system in the galaxy", but it is set to become even more secure – the Microsoft Secure Initiative sends its regards. Microsoft has therefore announced the "Quick Machine Recovery" function on it Ignite 2024 conference, held this week. A feature to get Windows up and running again more quickly after debacles such as Crowd Strike. Virus scanners will no longer run in kernel mode and applications will require administrator rights less frequently. Here is a summary of the numerous "promises".
[German]Windows 11 is, according to Microsoft, already the "most secure operating system in the galaxy", but it is set to become even more secure – the Microsoft Secure Initiative sends its regards. Microsoft has therefore announced the "Quick Machine Recovery" function on it Ignite 2024 conference, held this week. A feature to get Windows up and running again more quickly after debacles such as Crowd Strike. Virus scanners will no longer run in kernel mode and applications will require administrator rights less frequently. Here is a summary of the numerous "promises".
The Ignite 2024 conference for developers, IT experts and partners has been held this week. And Microsoft presented a veritable firework of new ideas. From simultaneous translation in Teams to the even more secure "most secure Windows ever". On November 19, 2024, Microsoft presented some features on how Windows 11 should be further developed in terms of security. The ideas were announced in the Windows blog in the article Windows security and resiliency: Protecting your business.
In case anyone hasn't noticed, since the Secure Future Initiative (SFI) was announced after the serious security incidents involving hacked clouds, Microsoft has made "security a top priority", and Windows is becoming even more secure with every new version. We're already on version 11, so everything is now bomb-proof – but "we're working on it" to make it even more secure.
Microsoft is not afraid to use an oxymoron and claim that protecting data and ensuring the integrity of customers' systems is of the utmost importance. And mention "from the chip to the cloud", that Microsoft offers multiple layers of security to protect identities and data, enabling a comprehensive ecosystem for innovation at a critical time.
Security and resilience
David Weston, Vice President Enterprise and OS Security at Microsoft, writes that the security and resilience of Windows 11 is a top priority for Microsoft. Lessons have been learned from the CrowdStrike incident (see, for example, Microsoft's analysis of the CrowdStrike incident and recommendations) from July 2024. Microsoft had already announced initial changes in September 2024 (see After CrowdStrike: Microsoft plans to remove security solutions from the Windows kernel). In the relevant blog post, Microsoft lists the following improvement goals:
- Allow users and applications to do more without administrator rights.
- Greater control over which applications and drivers are allowed to run.
- Improved identity protection to prevent phishing attacks.
As part of these improvement goals, specific functions have been outlined that are intended to achieve this in the future.
Announcement of Quick Machine Recovery
The CrowdStrike incident, in which millions of machines were no longer bootable because a protection function had paralyzed them, was a wake-up call. Hence the announcement of Quick Machine Recovery, which will be available to the Windows Insider Program community in early 2025.
This feature will allow IT administrators to perform targeted Windows Update fixes on PCs even if the machines cannot boot without needing physical access to the PC. This remote recovery is intended to free employees who are no longer able to work more quickly from non booting Windows systems.
Virus protection no longer runs in kernel mode
As part of the Microsoft Virus Initiative (MVI), we are working together with antivirus providers. Safe Deployment Practices are being introduced, which require all security product updates to be carried out in stages. Deployment rings will be used and monitoring will take place to ensure that the negative effects of updates are kept to a minimum (CrowdStrike sends its regards).
Microsoft is also developing new Windows features that allow security product developers to develop their products outside of kernel mode. This means that security products, such as antivirus solutions, can run in user mode, just like applications.
Administrator protection should help
Microsoft also states in the blog post that Windows 11 is already more secure by design than Windows 10 and wants to improve this further with additional measures. One point that is explicitly mentioned is administrator protection, which is currently in the test phase.
User access to critical system resources is blocked for standard accounts and this prevents malware or applications from changing computer configurations unnoticed. However, standard user permissions are frustrating for users as they cannot perform some common tasks such as changing time settings or installing productivity applications.
Microsoft justifies this by saying that in many cases a standard user does not have administrator authorization. I have the option of granting myself administrator rights on my systems. However, this is not possible with the Settings app – I either have to log in to the administrator account or use the classic Control Panel with its commands that have UAC support. This (together with the fact that only one administrator account is created during Windows installation) means that people all work with user accounts from the administrator group unless they are prevented from doing so by a company administrator and forced to use standard user accounts.
Microsoft writes that the default user authorization also means an additional effort for the IT department to support users in acceptable tasks, unless IT has tools such as Microsoft Intune Endpoint Privilege Management. This is, of course, a point that goes to Microsoft.
Administrator Protection (currently in preview) is a new solution from Microsoft that aims to mitigate this issue. By default, the user has the security of standard user authorizations. If necessary, they should still be able to make system changes, including the installation of apps, on their system without any problems.
With administrator protection, according to Microsoft, when a system change requires administrator rights, such as when installing some applications, the user is prompted to authorize the change as secure with Windows Hello. Windows creates a temporary, isolated admin token to complete the task. The token expires after the task is completed. Administrator protection ensures that users, not malware, retain control of system resources.
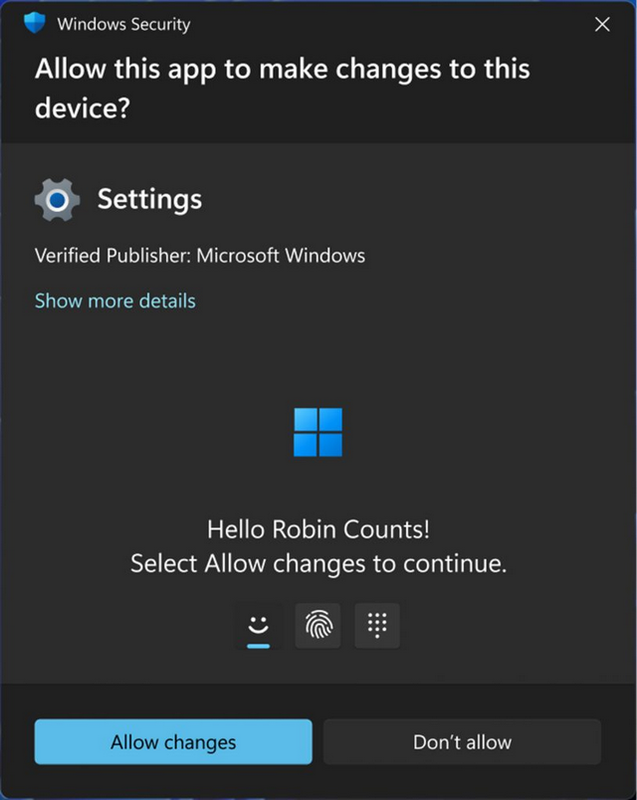
Attackers would also be disrupted, as they would no longer be able to automatically and directly access the kernel or other system functions classified as critical without special Windows Hello authorization.
Further security features
Microsoft also promises improved protection of login information. This is because the theft of access data and identities is a major concern for cyber attackers. Here, Microsoft wants to push multi-factor authentication (MFA) via Windows Hello. Windows Hello, as an integrated MFA solution in Windows, has been further hardened and expanded to include support for passkeys. Windows Hello is also used to protect Recall and Personal Data Encryption.
Another point is trustworthy apps and drivers, on which Microsoft is pinning its hopes. Many attacks only occur because users download insecure or unsigned applications and drivers. The Smart App Control and App Control for Business policies give IT the opportunity to ensure that only verified apps can be executed on the user's device.
With regard to the latter item: Untrusted apps and drivers are actually only a problem on unmanaged systems. Users do not install insecure drivers and applications on systems that are centrally administered by IT in companies. The problem only arises because Microsoft allows apps to be installed via Appx or as add-ins – or am I getting this wrong? Microsoft is sure that these measures will prevent attacks via malicious attachments or social engineering malware.
IT administrators should be able to simply select a "Signed and trusted policy" template in app control wizards to run millions of verified apps regardless of where they are deployed. Business applications not known to Microsoft can, it is promised, be easily added to the list of allowed apps by the IT administrator through policy changes or via Microsoft Intune Managed App Deployments.
Windows Protected Print is also mentioned as an innovation. This technology works seamlessly with Mopria-certified devices and does not require third-party drivers. The approach was developed to mitigate many of the previous security issues with printer drivers.
Also new is the introduction of personal data encryption for known folders in Windows 11 Enterprise. This uses Windows Hello authentication to protect files stored in the Desktop, Documents and Pictures folders. The protection is indicated by a lock symbol on the file.
If personal data encryption is activated, a device administrator cannot view the contents of the files, as the files remain encrypted until the user authenticates with Windows Hello. It will be interesting to see how the IT administration can ensure that the authorized persons in the company can access this data if the employee is "lost".
An IT administrator can use Microsoft Intune (or another management tool) to select all or a subset of these folders to apply Personal Data Encryption. It integrates with OneDrive and SharePoint on Microsoft 365 to enable easy collaboration.
Personal Data Encryption can be used independently of BitLocker or other solutions, and in combination with BitLocker it provides double encryption protection. Software developers can also use the Personal Data Encryption API to extend the protection of their application data.
Some thoughts on this
It's a developer conference and it's legitimate for Microsoft to present some new ideas. The security incidents of the last 24 months are forcing Redmond to take action. But it remains to be seen when and how the whole thing will be implemented and realized. The disaster with Recall in Windows 11 shows how things can go very wrong.
No matter how useful some of the innovations presented may seem in theory. At the end of the day, what counts is how it is implemented in practice and whether it is manageable. To me, it looks as if a few "balconies" have been screwed onto a shaky building in the hope that the whole thing will hold up better.



