 [German]Fortinet FortiWeb administrators need to take action because there is a vulnerability warning. Users of the Directus website builder also need to take action due to a vulnerability. Here is an overview of various security vulnerabilities in products, as well as other cyber incidents. For example, tokens were stolen from Salesloft via an attack on a "Drift AI chat agent."
[German]Fortinet FortiWeb administrators need to take action because there is a vulnerability warning. Users of the Directus website builder also need to take action due to a vulnerability. Here is an overview of various security vulnerabilities in products, as well as other cyber incidents. For example, tokens were stolen from Salesloft via an attack on a "Drift AI chat agent."
Fortinet FortiWeb vulnerability CVE-2025-52970
Fortinet FortiWeb contains an authentication bypass vulnerability (CVE-2025-52970) due to insufficient validation. Improper parameter handling in Fortinet FortiWeb versions 7.6.3 and below, versions 7.4.7 and below, versions 7.2.10 and below, and 7.0.10 and below could allow an unauthenticated attacker with non-public information about the device and the target user to gain administrator privileges on the device via a specially crafted request.
The vulnerability received a CVSS 3.x score of 8.1 (High); an analysis can be found here. Fortinet had already published security alert FG-IR-25-448 on August 12, 2025, and provided patches. Hunter.io points out in this tweet dated August 26, 2025, that 56,300 instances were found by its crawlers.
Vulnerability CVE-2025-55746 in Directus
Directus offers a real-time API and an app dashboard for managing SQL databases. As a backend, it enables a database to be transformed into a headless CMS (content management system, see also this page). It also offers admin panels or apps with a custom user interface, instant APIs, authentication, and more.
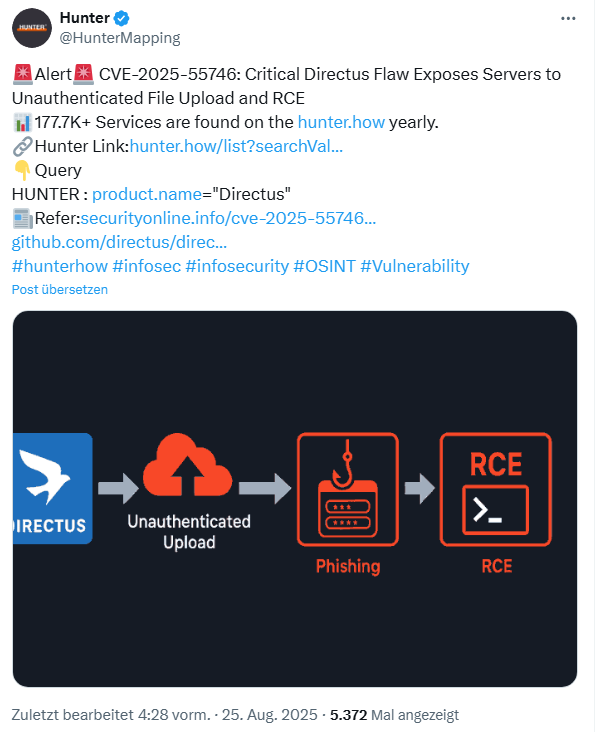
The Directus project has disclosed a critical security vulnerability identified as CVE-2025-55746 (CVSS 9.3) that could allow unauthenticated attackers to upload or modify files on vulnerable servers.
Hunter.io points out in the above tweet that 173,000 instances were found on the internet. Directus has fixed the vulnerability in version 11.9.3, but earlier versions remain vulnerable.
DOGE copies database to insecure cloud
The DOGE unit led by Elon Musk months ago has been wielding an axe in US government agencies in an effort to eliminate what it considers redundant.
Now, a whistleblower claims that DOGE employees uploaded a database containing all social security numbers issued to US citizens to an unsecured cloud instance. Chuck Borges, Chief Data Officer (CDO) of the SSA (Social Security Administration), made this public in a letter. Arstechnica has compiled the information here. If the allegation is true, it is further proof of what can happen when a government collects data on its citizens (which is necessary, as tax and social security numbers are used for identification purposes) and then things go off the rails politically. In the US, the social security number is highly valued because it identifies a person across many agencies and processes.
Hack at Salesloft, tokens stolen
Hackers managed to break into Salesloft's Drift Salesforce integration between August 8, and 18, 2025. They used this access to steal data such as AWS keys and Snowflake tokens.
What makes this particularly interesting is that Salesloft used SalesDrift, a third-party platform that connects the Drift AI chat agent to a Salesforce instance. This allows conversations, leads, and support cases to be synchronized in their CRM. It seems that this combination has now been targeted. Tokens were stolen from Salesloft via an attack on the "Drift AI chat agent." The next "victims" of this token theft are likely to be revealed soon.
In this article, Mandiant points to a widespread data theft campaign targeting Salesforce instances via Salesloft Drift. Our colleagues at Bleeping Computer have compiled the details in this article.






Please distinguish between Fortigate and Fortinet.
My bad, had changed it within the German blog, but forgot it here, will have a 2nd look soon, thanks.