![]() [German]An unsecured Microsoft Bing server allowed third parties to retrieve search queries and user location data. Among the data disclosed was device information – but no personal data. In some cases, however, the combination of this data can identify users.
[German]An unsecured Microsoft Bing server allowed third parties to retrieve search queries and user location data. Among the data disclosed was device information – but no personal data. In some cases, however, the combination of this data can identify users.
I was informed about this data incident by the security researchers at WizCase. WizCase is a portal that promotes the 'best VPNs', but is also involved in online security and privacy issues related to cyber security. Its security researchers recently discovered a data leak in the Microsoft Bing mobile app. The app stored user-related data such as search queries, location coordinates or device details on an unsecured server. This meant that the data was accessible via the Internet for anyone who knew the address of the ElasticSearch server.
An unsecured Microsoft ElasticSearch Server
While searching for open servers or databases on the Internet, WizCase's security experts, led by Ata Hakcil, came across an unsecured ElasticSearch server where search query data was logged. The records contained user-related data such as search queries, location coordinates or device details.
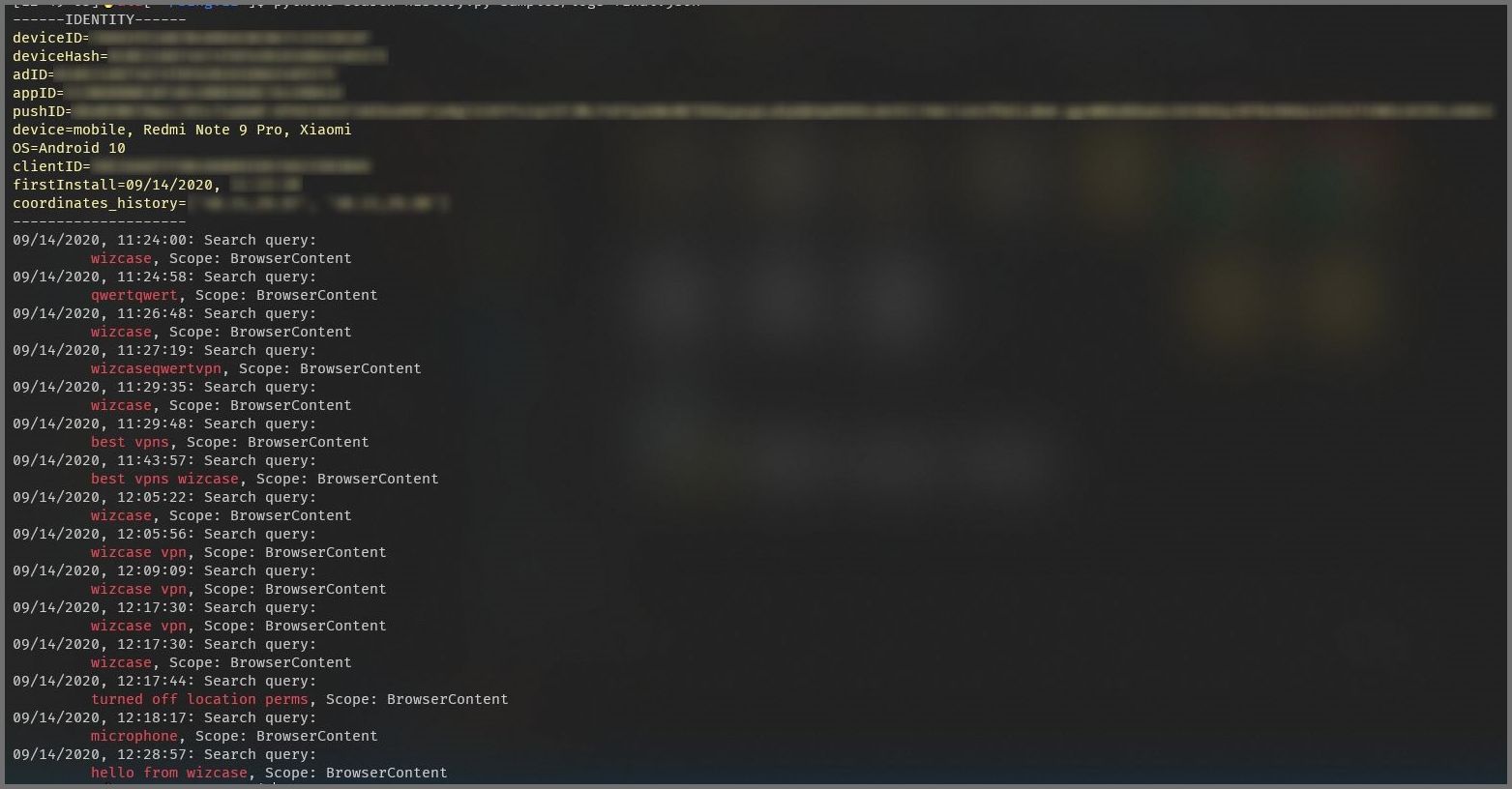
(Bing Search data, Source: WizCase)
Bing mobile app as source
The suspicion quickly arose that the data was being collected by the mobile Microsoft Bing app and transferred to the Microsoft server. The app is available for download from both Apple's iTunes Store and the Google Play Store and has been downloaded millions of times. Hakcil installed the Microsoft Bing app on a device and started a search query for WizCase. He then searched the server's log files and found his information. This included the search queries, device details and GPS coordinates. Hakcil sees this as proof that the exposed data came directly from the mobile bing app. The exposed data includes:
- Search terms in plain text (exception: search queries entered in private mode)
- Location Coordinates: If the access to the location determination is activated in the app, an exact location within a radius of 500 meters was added to the dataset.
Although the given coordinates are not exact, they still indicate a relatively small radius of the user's location. If the data is entered into Google Maps, it should be possible to trace the owner of the phone.
- The exact time when the search was performed.
- Firebase notification token
- Coupon data such as timestamps, when a coupon code was copied or automatically applied by the application and the URL it was located at
- A partial list of the URLs that users have visited from the search results
- Device model (telephone or tablet)
- Operating system
- 3 separate unique ID numbers assigned to each user found in the data
- ADID: Seems to be a unique ID for a Microsoft account.
- Device ID
- devicehash
Hakcil and his team found 6.5 TByte of data on the server, growing by up to 200 GB per day. Given the sheer volume of data, one can safely speculate that anyone who performed a Bing search with the mobile app while the server was exposed is at risk. Security researchers have seen records of people from more than 70 countries performing a search using the Bing app.
Server unprotected since September
According to WizCaseScanner, the Microsoft ElasticSearch server was password protected until the first week of September. The security team discovered the data leak on September 12, 2020, about two days after the authentication was removed. After identifying Microsoft as the owner of the server and the Bing app as the source, the team alerted Microsoft via their MSRC (Microsoft Security Response Center) on September 13, 2020. The data leak was closed on September 16, 2020 by password protecting the server again.
Meow attacks on the server …
However, the security researchers were able to determine that the Microsoft server was the target of a Meow attack between September 10 and 12, in which almost the entire database was deleted. When the security researchers discovered the server on September 12, 2020, 100 million records had been collected since the attack. On September 14, there was a second Meow attack on the server. The Meow attackers deletes unprotected data bases, their intentions are still unknown.
Some thoughts and consequences
Such open servers with their data leakage pose a general danger, as the data can be misused for phishing attacks and criminal activities. Even though the unsecured Microsoft ElasticSearch server did not collect any ostensibly personal data, the incident is serious. Users can be identified during the collected data.
On the one hand, the incident shows how glassy we have already become, that one should leave apps alone and rely on meta search engines like Startpage or Startpage. On the other hand a second aspect comes out. 14 days ago, after the Ransomware case at the University Hospital in Düsseldorf, I had a discussion on Facebook with a consultant from a system house. The consultant argued that you only have to use the 'right solutions' and he emphasized the capabilities of Microsoft ATP to detect attacks – which is undeniable.
But for me, this was the 'false belief in technology. My argument was that everything is becoming increasingly insecure and you always have to keep an eye on the weakest link in the chain, the human being and his mistakes. I suggested to think about how to limit the attack vector including access to data via internet. I had two things in mind:
- Data is given to third parties for further processing and falls victim to a cyber attack (somewhere there is a weak link in the chain that breaks).
- Or an administrator makes a mistake so that data can flow unsecured via the Internet.
In these cases the Microsoft ATP solution imho does not help. The above case confirms in my eyes exactly this gut feeling. If we want to get the issue of cyber and data security halfway under control again, we have to abandon many of today's paradigms and 'let's do something' approaches and radically rethink. The new motto is imho 'less is more' – when it comes to data, the cloud, apps and networking must solve our problems.



