 [German]Security researchers Michael Horowitz warns iOS users, that VPNs on this platform is broken. It looks, that it works fine. But the iOS device gets a new public IP address and new DNS servers. A detailed inspection of data leaving the iOS device by Horowitz shows that the VPN tunnel leaks. This became firstly know by ProtonVPN, according to Horowitz, in March 2020 and iOS v13 (I found this reddit.com post from 2018, claiming a similar behavior).
[German]Security researchers Michael Horowitz warns iOS users, that VPNs on this platform is broken. It looks, that it works fine. But the iOS device gets a new public IP address and new DNS servers. A detailed inspection of data leaving the iOS device by Horowitz shows that the VPN tunnel leaks. This became firstly know by ProtonVPN, according to Horowitz, in March 2020 and iOS v13 (I found this reddit.com post from 2018, claiming a similar behavior).
I became aware by the following tweet and the article VPNs on iOS are a scam, who has updated his article (first published in May 2022) a couple of days ago.
Horowitz tested first the ProtonVPN app running on an iPad with iOS version 15.4.1. Monitoring the router log after I started the VPN connection showed a VPN tunnel and IP addresses was obtained from a public server. Then he checked the Active Sessions for the iPad with PepLinks, and got a first indication of trouble.
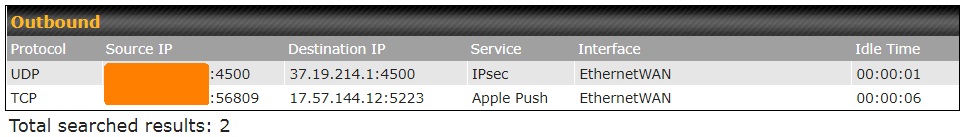
VPN session data, source: Michael Horowitz
The device was connected via an IPsec VPN tunnel with the UDP IP 37.19.214.1. But there was a 2nd TCP connection established by Apple Push, using port 5223 at IP address 17.57.144.12. Horowitz learned, that all IP addresses that start with 17 belong to Apple. Horowitz wrote:
iOS 15.4.1 still does not terminate existing connections/sessions when it creates a VPN tunnel. This presents assorted dangers. Connections outside the VPN communicate your real public IP address and there is no guarantee that they are encrypted. They are also vulnerable to ISP spying. And, a VPN provides what should be a trustworthy DNS service. Outside the VPN, anything goes.
Horowitz described his findings in more detail within his article VPNs on iOS are a scam. And he also provided some "workarounds", but his conclusion was: Don't trust any VPN on iOS, make the VPN connection using VPN client software in a router, rather than on an iOS device.




