 [German]Just a reminder to administrators who are responsible for Microsoft's cloud environments (Azure, etc.) in companies. It has probably been known for a long time, but as of May 8, 2023, the provider Microsoft will switch its multi-factor authentication (MFA) for cloud services to the so-called number matching procedure in order to increase security.
[German]Just a reminder to administrators who are responsible for Microsoft's cloud environments (Azure, etc.) in companies. It has probably been known for a long time, but as of May 8, 2023, the provider Microsoft will switch its multi-factor authentication (MFA) for cloud services to the so-called number matching procedure in order to increase security.
I confess, I had personally been following the issue only peripherally. In my recently published blog post Microsoft moves tenant security standards in Azure AD to MFA by May 8, 2023 a German user had pointed out in the comment here that Microsoft would also change something in terms of number matching on May 8, 2023. Yesterday, German reader Jochen pointed this out to me again in a personal message on Facebook:
Hello Günter,
I am curious what will happen on the 8th, when Microsoft forces Number Matching at the MFA.
Was there a contribution from your side?
In this context, I only remembered the above blog post, where the commentator touched on the subject. I don't know if this is widely known and if there can be any problems at all. But I mention it as a precaution in case users suddenly hit the helpdesk.
Number Matching rollout for MFA
Microsoft published the support post How to use number matching in multifactor authentication (MFA) notifications – Authentication methods policy on April 10, 2023, which talks about number matching in Microsoft Authenticator push notifications. The goal of this approach is to improve logon security for users with MFA. The key point is highlighted as a note in this post.
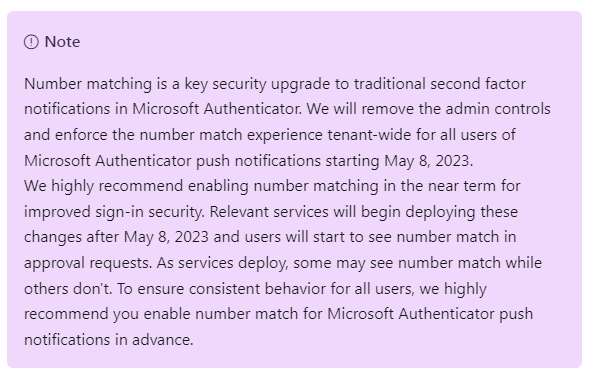
In the text box, Microsoft writes that the Number Matching technique is an important security enhancement to second-factor notifications in Microsoft Authenticator. And as of May 8, 2023, Microsoft will begin removing administrator control (over the use of Number Match) to enforce number match checking Tenant-wide for all users of Microsoft Authenticator push notifications.
The recommendation was to enable the number match checking technique in Microsoft Authenticator push notifications. Microsoft writes that appropriate services will begin deploying these changes after May 8, 2023. Users will then see the number match check dialog boxes when approving a login.
As a precaution, Redmond points out that it may well be that one service already displays Number Match queries while a second service does not (for a transition period). This can be worked around by administrators ensuring consistent behavior for all users by enabling the Number Match check option for Microsoft Authenticator push notifications in advance in the Admin Center of the relevant services.
Number Match explained
Microsoft explains the principle of number matching in the support article How to use number matching in multifactor authentication (MFA) notifications – Authentication methods policy in the section Number matching. When logging in via MFA, the user receives a push notification from Microsoft Authenticator that displays two digits (see the following figure).
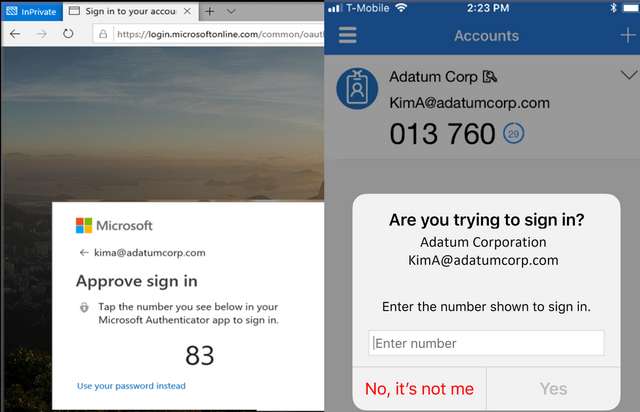 Number matching; source Microsoft
Number matching; source Microsoft
The numbers are then requested in the dialog box for logging in to the online account. Only if the displayed digits of the push notifications are entered in the field, the service accepts the login. What I currently can not assess whether this can cause problems in companies with users and what to consider.




How can I bypass this? Will downgrade of ms authenticator apk prevent this?