[German]A suspected China-based hacking group, which Microsoft refers to as Storm-0558, has managed to gain access to email accounts of about 25 organizations. These include government agencies (US State Department), as well as corresponding private accounts of people who are probably connected to these organizations. The explosive fact is that access was gained using a Microsoft account (MSA) customer key, which was used to forge tokens. I summarize below what Microsoft and security researcher Kevin Beaumont and CISA have to say about this.
[German]A suspected China-based hacking group, which Microsoft refers to as Storm-0558, has managed to gain access to email accounts of about 25 organizations. These include government agencies (US State Department), as well as corresponding private accounts of people who are probably connected to these organizations. The explosive fact is that access was gained using a Microsoft account (MSA) customer key, which was used to forge tokens. I summarize below what Microsoft and security researcher Kevin Beaumont and CISA have to say about this.
Microsoft admits hack of Outlook Online accounts
Microsoft admitted as of July 11, 2023, in the post Microsoft mitigates China-based threat actor Storm-0558 targeting of customer email that it had mitigated an attack by a China-based threat actor (Storm-0558) on customer email. The Storm-0558 group primarily targets government agencies in Western Europe, according to Microsoft, and focuses on espionage, data theft and credential access.
Based on customer-reported information, Microsoft began an investigation into the anomalous email activity on June 16, 2023. Over the next few weeks, our investigation revealed that Storm-0558 gained access to email accounts of approximately 25 organizations, including government agencies, as well as corresponding private accounts of individuals likely associated with those organizations, beginning on May 15, 2023.
They did so by using forged authentication tokens to access users' emails with an acquired Microsoft account signature key (MSA). Telemetry shows Storm-0558 was successfully prevented from accessing customer email with forged authentication tokens, it says. No action is required from customers. As with all observed state actor activity, Microsoft contacted the affected organizations directly through their tenant administrators, it says. The post linked above and this blog post provide more details.
Microsoft's fail …
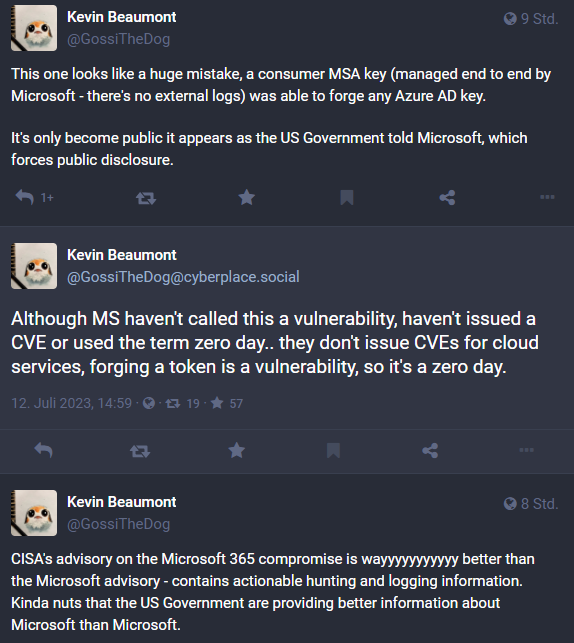
Security researcher Kevin Beaumont has posted some thoughts about the incident on Mastodon. Beaumont writes that the attackers used the Outlook Web App – which runs on the Exchange Server code base – to create authorization bypass tokens. Beaumont writes that Microsoft cleverly worded it in the blog post, saying only OWA was affected. But OWA is part of Microsoft 365 and Exchange Online.
Beaumont's assumptions are explosive: It looks to the security researcher as if Microsoft has made a gross mistake. An MSA key for Consumer (which is managed by Microsoft end-to-end – there are no external protocols) could be used to forge any Azure AD key. Beaumont suspects that this only became known because the U.S. government notified Microsoft. This then forces a public disclosure by Microsoft.
Also new to me was that Microsoft does not issue CVEs for vulnerabilities in cloud services. Microsoft did not refer to the above as a vulnerability in the notices. The "acquired Microsoft account (MSA) consumer signing key" used in the attack must have come from Microsoft's internal network, according to Beaumont. For Beaumont, forging a token is a vulnerability (a zero day).
The CISA report
Kevin Beaumont points out that the CISA report (US Cybersecurity and Infrastructure Security Agency report) is much more detailed and clear than Microsoft's submissions. In June 2023, a federal civilian executive branch (FCEB) found suspicious activity in its Microsoft 365 (M365) cloud environment. The agency (the U.S. Department of State, according to the Wallstreet Journal) reported the activity to Microsoft as well as the Cybersecurity and Infrastructure Security Agency (CISA). Microsoft's analysis determined that Advanced Persistent Threat (APT) actors accessed and exfiltrated unclassified Exchange Online Outlook data.
Specifically, the federal agency in question noticed MailItemsAccessed events with an unexpected ClientAppID and AppID in the M365 audit logs. The MailItemsAccessed event is generated when licensed users access items in Exchange Online mailboxes via any connection protocol from any client.
The authority in question considered this activity suspicious because the observed AppId does not normally access mailboxes in its environment. The agency reported the activity to Microsoft and CISA. Microsoft's analysis determined that APT actors accessed unclassified Exchange Online Outlook mailboxes and pulled data from a small number of accounts.
The APT actors used a Microsoft account (MSA) customer key to forge tokens and impersonate consumer and enterprise users. Microsoft fixed the problem by first blocking tokens issued with the acquired key. Later, they replaced the key to prevent further misuse.
ESo it was effectively a chance find because the federal agency in question was using advanced logging, specifically MailItemsAccessed events and an established baseline of normal Outlook activity (e.g., expected AppID), which allowed them to be suspicious. The MailItemsAccessed event enables detection of otherwise difficult-to-detect hostile activity.
The CISA reportstates that other logs probably would not have made the detection possible. Beaumont notes on Mastodon that the U.S. government uses advanced logging, also known as Purview Audit (Premium) logging, to detect these activities. A few years ago, there was a major public dispute between the U.S. government and Microsoft over the cost of access to Purview Audit (Premium). Here, access has proven to be a godsend. In this context, the CISA report still contains some advice on how to increase cloud security. gibt an, dass andere logs die Aufdeckung wohl nicht ermöglicht hätten. Beaumont merkt auf Mastodon an, dass die US-Regierung eine erweiterte Protokollierung, auch bekannt als Purview Audit (Premium)-Protokollierung, verwendet, um diese Aktivitäten aufzuspüren. Vor einigen Jahren haben es zwischen der US-Regierung und Microsoft einen großen öffentlichen Streit wegen der Kosten für den Zugang zu Purview Audit (Premium) gegeben. Hier hat sich der Zugang als Glücksfall erwiesen. Der CISA-Bericht enthält in diesem Kontext noch einige Hinweise zur Erhöhung der Cloud-Sicherheit.