 [German]Brief warning to administrators of Citrix NetScaler ADC and Citrix Gateway. The vendor has issued a security advisory warning of a critical remote code execution vulnerability in the products. The vendor has released updates for the affected products, which administrators should apply immediately to the installations they support.
[German]Brief warning to administrators of Citrix NetScaler ADC and Citrix Gateway. The vendor has issued a security advisory warning of a critical remote code execution vulnerability in the products. The vendor has released updates for the affected products, which administrators should apply immediately to the installations they support.
A German blog reader mentioned within a comment (thanks), but I also recognized it at Bleeping Computer and from Carl Staalhood at Twitter.
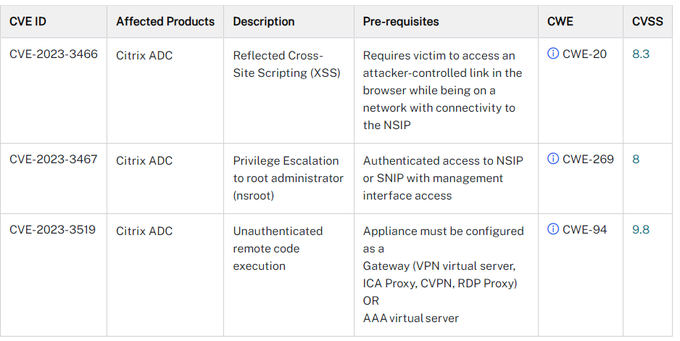
In NetScaler ADC (formerly Citrix ADC) and NetScaler Gateway (formerly Citrix Gateway), three vulnerabilities (CVE-2023-3519, CVE-2023-3466, CVE-2023-3467) have been disclosed (see screenshot above), with CVE values of 8.3, 8 and 9.8. Citrix has issued this security alert about these security flaws. The following supported versions of NetScaler ADC and NetScaler Gateway are affected by the vulnerabilities:
- NetScaler ADC and NetScaler Gateway 13.1 before 13.1-49.13
- NetScaler ADC and NetScaler Gateway 13.0 before 13.0-91.13
- NetScaler ADC 13.1-FIPS before 13.1-37.159
- NetScaler ADC 12.1-FIPS before 12.1-55.297
- NetScaler ADC 12.1-NDcPP before 12.1-55.297
The NetScaler ADC and NetScaler Gateway version 12.1 is now End Of Life (EOL) and vulnerable to these vulnerabilities. The only thing left to do is to upgrade the affected applications to a supported version.
Customers who self-manage the NetScaler ADC and NetScaler Gateway products in question should install the following updates immediately:
- NetScaler ADC and NetScaler Gateway 13.1-49.13 and later versions
- NetScaler ADC and NetScaler Gateway 13.0-91.13 and later versions of 13.0
- NetScaler ADC 13.1-FIPS 13.1-37.159 and later versions of 13.1-FIPS
- NetScaler ADC 12.1-FIPS 12.1-55.297 and later versions of 12.1-FIPS
Citrix writes that exploitation of the CVE-2023-3519 vulnerability has been observed on unsecured appliances. Bleeping Computer has some more information about this.



