[German]If anyone is wondering why malware is repeatedly found in Android apps that are quite officially available in the Google Play Store, there is an explanation. Google's security team has now confirmed that attackers are using dynamic code loading to bypass malware detection in the Play Store.
[German]If anyone is wondering why malware is repeatedly found in Android apps that are quite officially available in the Google Play Store, there is an explanation. Google's security team has now confirmed that attackers are using dynamic code loading to bypass malware detection in the Play Store.
I've reported here on the blog from time to time that malicious Android apps have been detected in the Google Play Store and removed by Google. But there are approaches that apps can reload malicious code even though the version set in the Google Play Store is clean. I became aware of the issue via the following discussion on Twitter. Nicolas Krassas points out the problem of Dynamic Code Loading, which allows malicious Android apps to bypass malware detection in the Google Play Store.
This has now been confirmed by the Google Cybersecurity Action Team (GCAT). In this document, Google's security experts disclose a technique called versioning. This technique is used by threat actors to bypass malware detection in the Google Play Store.
The case of the iRecorder app
ESET decribed a case, where a legitimate Android app iRecorder suddenly had malicious features and spied on its users within a year. The app was available on Google Play in September 2021, though ESET researchers suspect the malicious functionality was likely not added to the app until August 2022.
The malicious code added to the clean version of iRecorder is based on the open-source AhMyth Android RAT (Remote Access Trojan) and was named AhRat by ESET. The malicious app is capable of recording audio and stealing files via the device's microphone, which suggests that it could be part of a spying campaign.
Dynamic Code Loading
Although only less than 1% of the apps posted on the Google Play Store have malicious code, attackers manage to bypass the security mechanisms again and again. One way to circumvent Google Play's security controls is versioning. To do this, a developer publishes a version of his app in the Google Play Store (also works for Apple in the Store) that is free of malicious code and passes the checks. Later, the app receives an update from a third-party server, which then adds the malicious code.
The technique is not new, but it is still effective. There is a Mitre.org alert T1407 from October 25, 2017, updated to March 20, 2023, about this approach. Several malware like the banking Trojan SharkBot used it to bypass the controls put in place by Google for the Play Store. A common form of versioning is the use of Dynamic Code Loading (DCL). DCL stands for an app that reloads code from untrusted sources.
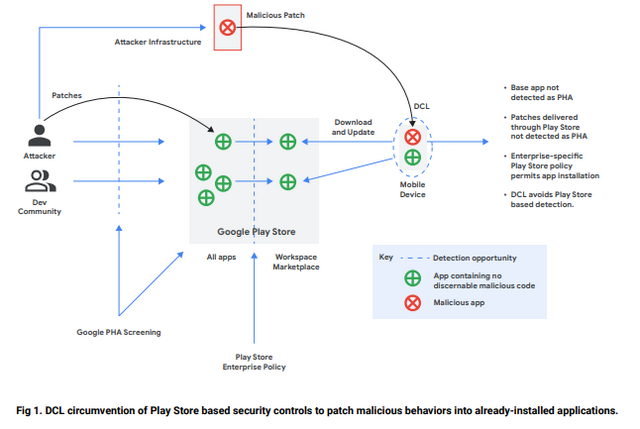 Source: Google report
Source: Google report
Another method is obfuscation of malicious code within the app. This approach was described by a security researcher in this article as of July 26, 2023. Such apps probably cannot be detected by the Play Store's protection measures.
User awareness is required
The only protection Google suggests is to only install apps from trusted sources in the Google Play Store. In other words, avoid apps from unknown developers as much as possible. My tip is to also look at the ratings of other users and the download numbers of the apps and see which developer is behind the app.
In my opinion, the above approaches are still based on the "user is inattentive and clueless and installs everything he can get" approach. In my Android books for beginners, I have been advising for years to limit the number of apps used and only use essential apps from well-known developers. Unfortunately, this is counteracted by the mania that everyone thinks they have to offer an app for every crap.