 [German]Microsoft has just issued a warning to Teams users because they have encountered phishing campaigns targeting this clientele. Behind these phishing campaigns are Russian attackers that Microsoft names Midnight Blizzard (or NOBELIUM. APT29, UNC2452 and Cozy Bear). The group's goal is to obtain credentials from victims, specifically in the government, non-governmental organization (NGO), IT services, technology, discrete manufacturing, and media sectors.
[German]Microsoft has just issued a warning to Teams users because they have encountered phishing campaigns targeting this clientele. Behind these phishing campaigns are Russian attackers that Microsoft names Midnight Blizzard (or NOBELIUM. APT29, UNC2452 and Cozy Bear). The group's goal is to obtain credentials from victims, specifically in the government, non-governmental organization (NGO), IT services, technology, discrete manufacturing, and media sectors.
In the post Midnight Blizzard conducts targeted social engineering over Microsoft Teams, Microsoft writes that its Microsoft Threat Intelligence has identified highly targeted social engineering attacks. This involves phishing lures to steal credentials being sent as Microsoft Teams chats by a threat actor. Microsoft explicitly names the group Midnight Blizzard (also referred to as NOBELIUM. APT29, UNC2452 and Cozy Bear).
Typical patterns for attacks
Die Angreifer der Gruppe setzen regelmäßig Token-Diebstahltechniken für den Erstzugang zu Zielumgebungen ein. Kombiniert wird dies mit Authentifizierungs-Spearphishing, Passwort-Spray, Brute-Force- und anderen Angriffen auf Zugangsdaten. Das Angriffsmuster ist seit mindestens Ende Mai 2023 als Teil einer breiteren Angriffskampagne zum Abgreifen von Zugangsdaten zu beobachten.The group's attackers regularly use token theft techniques for initial access to target environments. This is combined with authentication spearphishing, password spraying, brute force and other credential attacks. The attack pattern has been observed since at least late May 2023 as part of a broader attack campaign to grab credentials.
- To facilitate the attack, the actor uses Microsoft 365 tenants owned by small businesses. These were compromised in previous attacks, and are now used to host the websites for the social engineering attack.
- The actor renames the compromised tenant, adds a new onmicrosoft.com subdomain, and a new user associated with that domain. The attacker uses keywords related to security or product names to create a new subdomain and a new tenant name to lend legitimacy to the messages.
Messages are then sent from this user to the target tenant. The target user then receives, for example, a Microsoft Teams message request from an external user posing as a technical support or security team member.
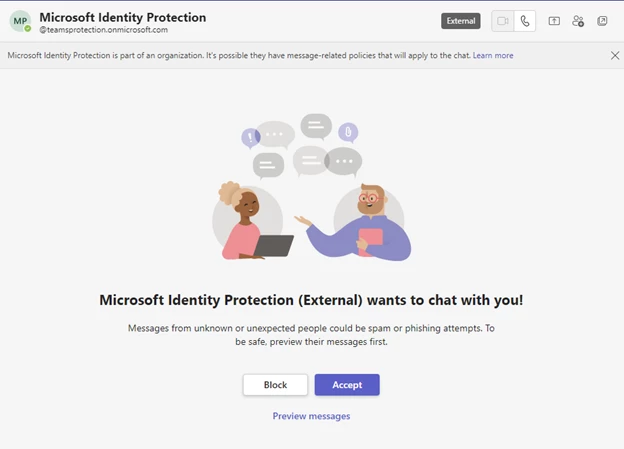
If the user accepts the message request, they will receive a Microsoft Teams message requesting them to enter a code sent by Microsoft into the Microsoft Authenticator app on their mobile device. If the user falls for this trick and confirms the code, the attacker receives an authentication token that allows access to the user's Microsoft 365 account.
Microsoft has observed that once compromised, the attacker then performs other activities. This usually amounts to stealing information from the compromised Microsoft 365 tenant. There are also likely cases where the attacker attempts to add a device to the organization as a managed device via Microsoft Entra ID (formerly Azure Active Directory). The goal is presumably to bypass conditional access policies, which typically enforce that only managed devices have access to certain resources. Details can be found in Microsoft's post. There, Microsoft also gives advice on how to arm oneself against such attacks.
Microsoft warns alsoof attacks on stadiums for sporting events, according to this post on The Hackers News. It says cyber risks to live sporting events have expanded rapidly. "Information about athletic performance, competitive advantage and personal data is a lucrative target," says a report from Cyber Signals, cited by The Hacker News. Sports teams, major league and global sports associations, and entertainment venues host a wealth of valuable information of interest to cybercriminals, it said.
Who is Midnight Blizzard?
Midnight Blizzard (other names include NOBELIUM, APT29, UNC2452, and Cozy Bear) is a Russian-based threat actor attributed to the Russian Foreign Intelligence Service (SVR). This group is known to primarily target governments, diplomatic institutions, non-governmental organizations (NGOs), and IT service providers, primarily in the United States and Europe. Their focus is on intelligence gathering through longstanding and targeted espionage of foreign interests, which can be traced back to early 2018. Their operations often compromise valid accounts, and in some highly targeted cases use advanced techniques to compromise authentication mechanisms within an organization to expand access and evade detection, Microsoft says.
Midnight Blizzard takes a consistent and, above all, persistent approach to achieving its goals, according to the observations of security researchers. The group's actors use a variety of methods for initial access, from stolen credentials to supply chain attacks, exploiting local environments to later penetrate the cloud, exploiting service provider trust chains to gain access to downstream customers, and Active Directory Federation Service (AD FS) malware known as FOGGYWEB and MAGICWEB. Midnight Blizzard (NOBELIUM) is identified by partner security vendors as.



