 [German]At the end of September 2023, the cloud provider Shadow was hacked via one of their hosters. The platform is used by online gamers, and three blog readers emailed me about the incident (thanks for that). The hackers are now trying to sell captured data from gamers.
[German]At the end of September 2023, the cloud provider Shadow was hacked via one of their hosters. The platform is used by online gamers, and three blog readers emailed me about the incident (thanks for that). The hackers are now trying to sell captured data from gamers.
Who is Shadow?
Shadow is a cloud gaming service that offers its customers the opportunity to play sophisticated AAA games on a virtual computer. The whole thing can then be streamed to local devices (PCs, laptops, smartphones, tablets, smart TVs). The provider makes high-end Windows PCs available in the cloud for this purpose.
The security incident
There are several blog readers who informed me about the incident by mail yesterday and the day before. One reader had already received a provider notification mail as of October 11, 2023, writing that he was a customer of cloud gaming provider shadow.tech. The provider had sent him a mail about a security/data protection incident, the original of which I have.
Another reader contacted us yesterday and wrote that he had tested the cloud provider's offer some time ago and therefore still has an account. There had probably been an incident there in which customer data had been tapped. Again, it is interesting how this happened. All readers were informed about the incident by Shadow via email (see screenshot).
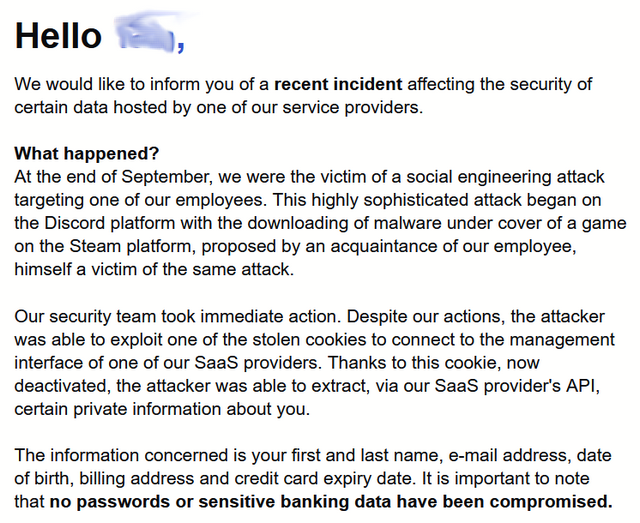
The incident took place back in late September 2023 and stems from a social engineering attack on a Shadow employee. According to Shadow, this sophisticated attack began on the Discord platform with the downloading of malware. It was suggested by an acquaintance of the employee to download a game on the Steam platform. However, this game was contaminated with malware and the acquaintance was himself a victim of the same attack.
The Shadow employee must have had administrative privileges. And the infected machine was also used to access the platform – two cardinal errors. According to their statement, the Shadow security team did act immediately. Despite the measures, the attacker managed to exploit one of the stolen cookies to connect to the administrative interface of one of the SaaS providers used by Shadow. Thanks to this cookie (which is now disabled), the attacker was able to retrieve certain private information about Shadow customers via the SaaS provider's API.
The stolen data includes the first and last name, the e-mail address, the date of birth, the billing address and the expiration date of the credit card used. According to the provider, no passwords or sensitive banking data were tapped.
Upon learning of the incident, Shadow immediately took steps to secure its systems (but this was too late). Precautions were taken to prevent future incidents. It also strengthened security protocols that Shadow plans to apply to all of its SaaS providers. Finally, it plans to upgrade its internal systems to render the compromised workstations harmless, suggesting that the machines used for streaming are also likely to be compromised.
The provider warns that, following this incident, those affected must be very vigilant about the emails they receive, as they could be phishing attempts. In general, the provider advises protecting all accounts by setting up multi-factor authentication ("MFA").
Data offered in hacker forum
Bleeping Computer colleagues report here yesterday that the threat actor claimed in an underground forum that he broke into the French provider Shadow at the end of September and managed to steal the data of 533,624 users. He plans to sell the stolen database on a well-known hacker forum.
"At the end of September, I gained access to the database of the French company Shadow. It contains only customers, not all Shadow users," the post for sale states, according to Bleeping Computer. It continues, "After an attempt at amicable settlement, which they deliberately ignored, I decided to put the database up for sale."



