There is an out-of-bounds vulnerability CVE-2023-34048 in VMware vCenter that leaves systems vulnerable. A security researcher scanned the Internet for accessible and unpatched instances and found numerous systems. Administrators of VMware vCenter installations should ensure systems are patched.
There is an out-of-bounds vulnerability CVE-2023-34048 in VMware vCenter that leaves systems vulnerable. A security researcher scanned the Internet for accessible and unpatched instances and found numerous systems. Administrators of VMware vCenter installations should ensure systems are patched.
VMware vCenter vulnerability CVE-2023-34048
An out-of-bounds write vulnerability CVE-2023-34048 exists in VMware vCenter Server in the implementation of the DCERPC protocol. A malicious actor with network access to vCenter Server can trigger an out-of-bounds write that could potentially lead to remote code execution. The vulnerability has a CVSS index of 9.8, so it is critical.
VMware has issued security advisory VMSA-2023-0023 on this as of Oct. 25, 2023, and has released security updates for products still in support.
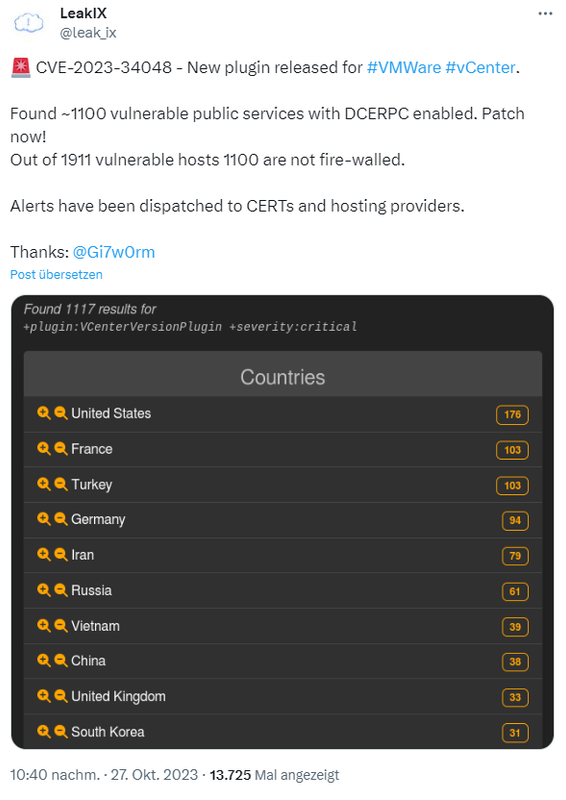
Unpatched systems found
I came across the following tweet on X. Someone found about 1,100 publicly accessible instances with DCERPC enabled as a service and not running behind any firewall. It's time for the administrators of these systems to take action, .