[German]Addendum of February 9, 2024 – The FBI has dismantled the Warzone RAT malware group, seized its infrastructure and arrested two individuals involved in the cybercrime operation. The RAT malware allowed cybercriminals to secretly connect to victims' computers to steal data and perform other malicious activities without the victims' knowledge.
[German]Addendum of February 9, 2024 – The FBI has dismantled the Warzone RAT malware group, seized its infrastructure and arrested two individuals involved in the cybercrime operation. The RAT malware allowed cybercriminals to secretly connect to victims' computers to steal data and perform other malicious activities without the victims' knowledge.
I first became aware of the operation described her in the following tweet last Friday.
"Today, the FBI and our international law enforcement partners dismantled a sophisticated malware service that cybercriminals purchased and used to infect the computer systems of unsuspecting victims here in Massachusetts and around the world," said Jodi Cohen, Special Agent in Charge of the FBI's Boston Division.
Infrastructure seized
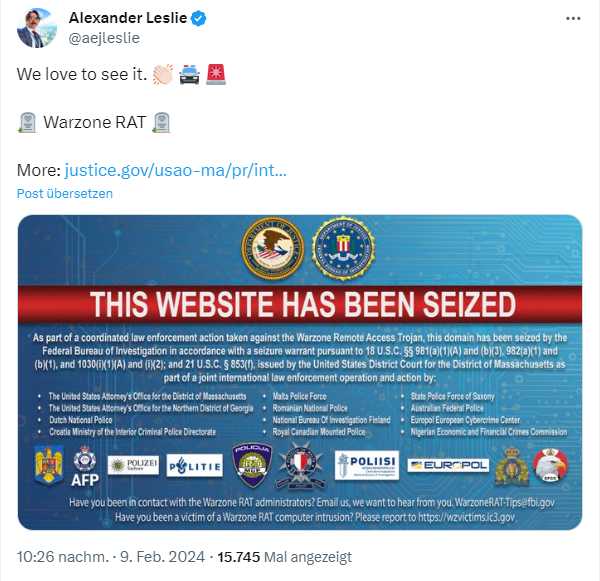
The successful operation was announced by the US Attorney's Office on Friday, February 9, 2024. US federal authorities in Boston have seized internet domains used to sell computer malware as part of an international law enforcement operation (with various police authorities and Europol). The malware, called Warzone Rat, allowed cybercriminals to secretly access victims' computers and steal data.
Federal authorities in Boston seized www.warzone.ws and three associated domains offering for sale the Warzone RAT malware – a sophisticated remote access Trojan (RAT) that allows cybercriminals to secretly connect to victims' computers for malicious purposes.
According to court documents authorizing the seizures, Warzone RAT allowed the cybercriminals to search victims' file systems, take screenshots, record keystrokes, steal victims' usernames and passwords, and observe victims through their webcams – all without their knowledge or permission.
Arrest of two suspects
Federal authorities in Atlanta and Boston have also issued indictments against individuals in Malta and Nigeria, respectively, for their alleged involvement in selling the malware and assisting cybercriminals to use the malware for malicious purposes.
One is Daniel Meli, 27, of Zabbar, Malta, who was arrested on February 7, 2024 and appeared for a preliminary hearing before the Magistrate Magistrate in Valletta, Malta.
Meli was indicted on December 12, 2023, by a federal grand jury in the Northern District of Georgia on charges of unauthorized damage to protected computers, unlawful sale and promotion of an electronic eavesdropping device, and engaging in a conspiracy to commit multiple computer intrusion offenses. According to the indictments, Meli offered malware products and services for sale to cybercriminals on online computer hacking forums since at least 2012.
Specifically, Meli allegedly assisted cybercriminals who wanted to use RATs for malicious purposes and offered educational materials for sale, including an e-book. Meli also allegedly sold the Warzone RAT and, before that, the malware known as the Pegasus RAT, which he distributed through an online criminal organization called Skynet Corporation. He also offered online customer support to purchasers of both RATs. The Northern District of Georgia is seeking Meli's extradition to the United States.
Separately, Prince Onyeoziri Odinakachi, 31, of Nigeria, was arrested Feb. 7 by the Port Harcourt Zonal Command of the Nigerian Economic and Financial Crimes Commission. Odinakachi was indicted by a federal grand jury in the District of Massachusetts on Jan. 30 on charges of conspiracy to commit multiple counts of computer intrusion, including obtaining authorized access to protected computers to obtain information and causing unauthorized damage to protected computers. According to the indictments, between June 2019 and no earlier than March 2023, Odinakachi provided online customer support to individuals who had purchased and used the Warzone RAT malware.
According to court documents, not only were cases discovered in which the Warzone RAT malware was used to attack victim computers in Massachusetts, but the Warzone RAT malware was also secretly acquired and analyzed, confirming its multiple malicious capabilities. Law enforcement is urging victims of a Warzone RAT attack to report it at wzvictims.ic3.gov.