 [German]A reader has pointed out to me that there is a behavior that should make it possible to bypass authentication with the user account on the client. Specifically, a third party can log in to the account again without entering a password, after a user logs out. It's a problem of single sign on. I'll put the reader's information up for discussion.
[German]A reader has pointed out to me that there is a behavior that should make it possible to bypass authentication with the user account on the client. Specifically, a third party can log in to the account again without entering a password, after a user logs out. It's a problem of single sign on. I'll put the reader's information up for discussion.
Reader report on the problem
Blog reader Markus contacted me via email this week because he's encountered an issue with the new Microsoft Teams 2.0 client that he believes is problematic. As he wrote:
Today I came across a topic that blew my mind. The new Teams client has had a behavior since at least December 2023 that is highly problematic in my eyes.
Markus has discovered that the login and logout processes are probably saved in the client. However, this has an unpleasant effect, as he writes. If a user logs in to the new Teams client and then logs out again, this access should actually be blocked for third parties. Markus wrote to me that a third party can then log back into the account on the login page (in the welcome screen) without being prompted for a password.
A few details
According to Markus, the problem was that the new Teams caches all accounts ever used in the login screen. He wanted to clear this list. If a user has logged in and out of an account, the mask looks like this:
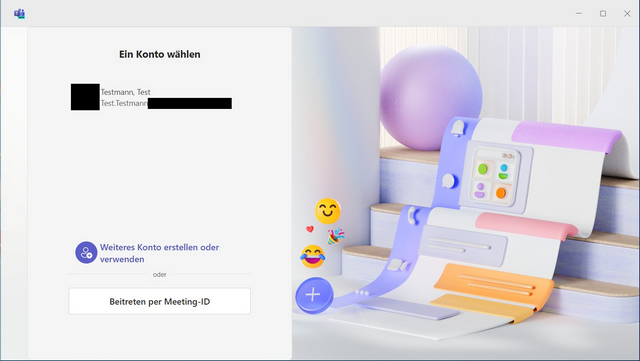
Markus wrote, this is also familiar from the old Teams client. What was new for the reader was that clicking on the suggestion (he probably means the "test user") immediately takes him to Teams – he no longer need to enter your login details. Markus wrote: "When you first logged in, you deliberately selected "No, only log in to this app". The online account is therefore not linked in the Windows settings.
Let's take a closer look
Markus originally "just" wanted to clear this list of users. Based on the above discovery, he then went on a search. You can reset the login data of the new Microsoft Teams 2 client in the Windows settings. Markus sent me the following screenshot.

The reader then reset the Microsoft Teams app and hoped that this would also clean up the data in the user profile. He then restarted the Microsoft Teams 2 client. He landed back on the login page with the suggestion for his test user and clicked on the entry expectantly. And he was promptly logged into the test user's account without being asked for a password. Insight: Resetting the app does not help.
How to delete the data
Markus asked how he could delete the login data of Teams users. A query on a search engine such as Google yielded only a few hits and answers in the Microsoft Answers forum. But after a lengthy search, he came across the Microsoft Answers forum entry New Teams – How do you remove users from the "Pick an account" / Login screen? which promises a remedy. A user asks the same question there because he made a corresponding observation and reported it in the forum on December 1, 2023.
While testing "New Teams" I have noticed that the "Pick an account" / Login screen shows the previous users that have logged in, even if they have clicked "sign out".
When clicking on those users, it also logs them in without asking for a password.
After reading other posts here, I have tried deleting the cache here: %LocalAppData%\Packages\MSTeams_8wekyb3d8bbwe
And also deleting the data in this folder: %LocalAppData%\Packages\Microsoft.AAD.BrokerPlugin_cw5n1h2txyewy
Doing this has stopped the accounts from being logged in without a password, but the accounts still appear on the "Pick an account" / Login screen.They do not show in classic teams or any other application and there are no additional accounts in the "Access Work and School" windows setting page.
I have also tried to fully remove and reinstall Teams but the accounts are still visible.
Sounds like a stubborn box, what the software developers have implemented. Markus then found a solution to this problem. In addition to the Teams reset, you also have to delete these folders:
C:\Users\<User>\AppData\Local\Packages\Microsoft.AAD.BrokerPlugin_cw5n1h2txyewy C:\Users\<User>\AppData\Local\Microsoft\TokenBroker C:\Users\<User>\AppData\Local\Microsoft\OneAuth
The IdentityCachefolder was not present in the reader's test scenario, but was found in the original problem case that prompted the investigation in the first place. Finally, Markus came to the conclusion that if you then restart Teams (and preferably also the PC beforehand), you are greeted again by the virgin login screen without predefined options and, above all, you can no longer access the account without a password.
Teams 2.0 bug with OneAuth?
The reader then searched for the keyword OneAuth and came across a 4-year-old Reddit thread with the title How in the crap are my Microsoft Account credentials being cached? It's funny, back then someone was already complaining about Microsoft account credentials being cached.
Markus concludes that this "OneAuth issue has been smouldering for some time". And he adds that Microsoft Teams 2.0 also has "the bug" that no login data is requested. As the reader writes:
So anyone who logs into their Teams account anywhere for even a minute under the new Teams risks someone being able to access the account later just like that. Simply "logging out" of Teams is not enough; you have to go deep down and delete several folders.
The reader outlines the scenario that there are certainly many companies that operate meeting rooms with special "meeting" Windows users. You then log in to the Teams app there and log out again later. As a result, the login data of many "Teams accounts" will accumulate on the systems over time. Microsoft doesn't really take care of this behavior.
Problem already mentioned in the blog
It slipped my mind again, Fritz already reported the authentication problem in mid-January 2024 in this comment on my German post Teams 2.0-Umstieg: Abstimmung mit den Füßen? 2/3 noch auf altem Client.
PowerShell solution for deleting the credentials
There was feedback on Facebook to my post that the problem is known and probably applies to all Office apps. Sebastian has given the following PowerShell commands to clear the Teams cache, maybe it will help.
Write-Host "Microsoft Teams wird jetzt beendet, um den Cache zu leeren." try{ Get-Process -name ms-teams | Stop-Process -Force Start-Sleep -Seconds 5 Write-Host "Microsoft Teams wurde erfolgreich beendet." } catch{ echo $_ } # Der Cache wird nun geleert try{ Get-ChildItem -Path $env:LOCALAPPDATA\"Packages\MSTeams_8wekyb3d8bbwe" | Remove-Item Get-ChildItem -Path $env:LOCALAPPDATA\"Packages\Microsoft.AAD.BrokerPlugin_cw5n1h2txyewy" | Remove-Item Get-ChildItem -Path $env:LOCALAPPDATA\"Microsoft\OneAuth" | Remove-Item Get-ChildItem -Path $env:LOCALAPPDATA\"Microsoft\TokenBroker" | Remove-Item Get-ChildItem -Path $env:LOCALAPPDATA\"Microsoft\IdentityCache" | Remove-Item } catch{ echo $_ } write-host "Der Microsoft Teams Cache wurde erfolgreich geleert."




We had noticed something similar on the old Teams client on a meeting room PC, where we had a shared AD account (basically a kiosk account) that users had logged into on the PC. Users then started Teams (old) with their online credentials. When logging out of the kiosk login account (or rebooting) the credentials they used in Teams would still be cached and the next user logging in to this kiosk account would have full access to their user Teams account. Only way to kill that was to force that "Microsoft.AAD.BrokerPlugin_cw5n1h2txyewy" directory tree to be killed on each login via script.
On the old Teams client I was able to prevent this by setting;
Key: HKLM\SOFTWARE\Policies\Microsoft\Windows\WorkplaceJoin
DWORD: BlockAADWorkplaceJoin=1"
I wonder if this works for the new Teams client as well then!
Deleting those folders does also delete all your stored credentials for 365 services.
For instance, you have connected your 365 work account in your profile.
Someone else (perhaps a relative) wants to login on Teams with his/her account.
Following this "delete folders procedure" will also delete your own 365 credentials in all Office apps.
There should be a better solution!