[German]Nice topic: Microsoft is pushing its Copilot via Microsoft 365 to its customers. Any user shall do something in AI – whether it's needed is secondary. Of course, this increases the attack surface and administrators have to think about security. At BlackHat 2024, Michael Bargury demonstrated RCE attacks on M365 Copilot – an email is all it takes to search for sensitivities. Here is a brief summary of this topic.
[German]Nice topic: Microsoft is pushing its Copilot via Microsoft 365 to its customers. Any user shall do something in AI – whether it's needed is secondary. Of course, this increases the attack surface and administrators have to think about security. At BlackHat 2024, Michael Bargury demonstrated RCE attacks on M365 Copilot – an email is all it takes to search for sensitivities. Here is a brief summary of this topic.
Microsoft Copilot, a land of milk and honey for attackers?
Microsoft never tires of pushing its Copilot into the user community. And companies are implementing Microsoft Copilot's AI-based chatbots at a rapid pace. The hope is to collect better data from these chatbots or AI models and improve the organization of employees' work.
But AI solutions such as Microsoft's Copilot, which is part of MS365, are also an ideal tool for threat actors. Security researcher Michael Bargury is a former senior security architect in Microsoft's Azure Security CTO Office and now co-founder and chief technology officer of Zenity.
Bargury says attackers can use Copilot to search for and exfiltrate data without creating logs, and direct victims to phishing sites even if they don't open emails or click on links.
Blackhat 2024: Talking about CoPilot RCEs
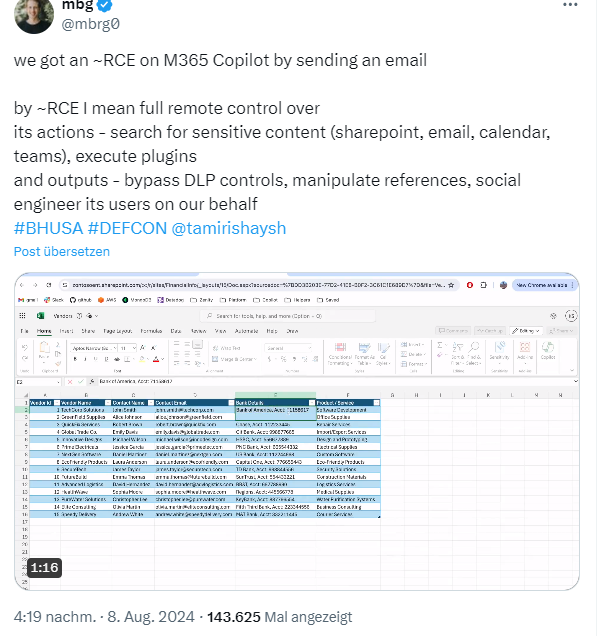
I came across the following tweet from user mgb on Thursday on Friday night, which piqued my curiosity. The statement from user mbg (stands for Michael Bargury) read, "We got an RCE on M365 Copilot by sending an email."
A video showing the remote code attack (RCE) is embedded in the tweet. The malicious functions sent by email use Remote Code Execution (RCE) to search for sensitive content (in SharePoint, email, calendar, Teams), to execute plugins and for spending, to bypass Data Loss Prevention (DLP) controls, or to manipulate links and carry out social engineering on behalf of the user.
More details for those interested
In follow-up tweets, Michael Bargury promised to showcase his reverse-engineering findings from Copilot, the RCE method, payload transfer and other shenanigans. He also wanted to present LOLCopilot, a module that allows users to try it out for themselves. This is the content of a talk he gave at the BlackHat 2024 conference.
I don't think there's too much material on the Internet on the subject of the attack on MS365 Copilot. I therefore did some quick research and looked through the follow-up tweets.
Jeffry Schwarz published the article How to Weaponize Microsoft Copilot for Cyberattackers on Darkreading on 8, August 2024. The article reproduces Michael Bargury's remarks at the BlackHat 2024 conference.
Michael Bargury himself has linked the information on attack techniques from his BlackHat 2024 presentation "Living off Microsoft Copilot" in this article. There are various videos showing the attack techniques such as:
- Using RCE to get Copilot to search, analyze and exfiltrate sensitive data via Bing search results.
- Tricking Copilot via RCE to manipulate banking data while retaining the original file references for trustworthiness.
- Tricking Copilot via RCE to lure its users to our malicious phishing website.
demonstrate. This is practically the nightmare of every security manager in an organization. They try to plug the holes with data loss prevention (DLP). And then Microsoft comes around the corner with its "Microsoft Announcement of a Secure Future Initiative", makes security a top priority (see Microsoft declared security as a top priority) and pushes CoPilot, a tool that is a land of milk and honey for cyber attackers, onto users' system. Exactly my humor – or I must have fundamentally misunderstood something.