 [German]Brief information for Facebook users. There are indications that a campaign is running via ads on Facebook, which pretends to be a fake Trojan in the browser and asks the user to call a "Microsoft support page". This is of course also fake and amounts to fraud. I came across such an ad the other day, and I'll post it briefly on the blog.
[German]Brief information for Facebook users. There are indications that a campaign is running via ads on Facebook, which pretends to be a fake Trojan in the browser and asks the user to call a "Microsoft support page". This is of course also fake and amounts to fraud. I came across such an ad the other day, and I'll post it briefly on the blog.
The browser reports a Trojan
I could hardly believe it – on August 29, 2024, I checked some posts from IT groups and PMs from blog readers on Facebook, but deliberately didn't click on anything. I just had a number of tabs (from Facebook and other websites) open in my browser. Suddenly, a window opened suggesting that I had a Trojan on my system.
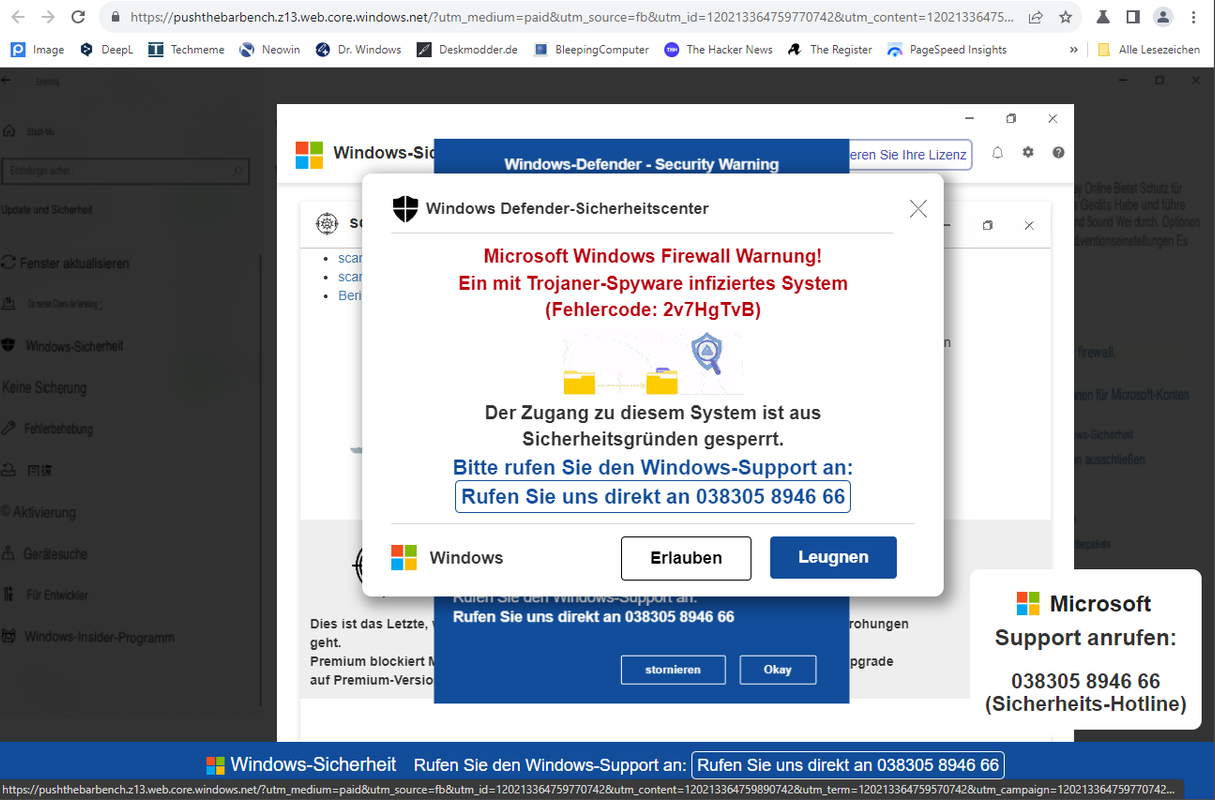
Fake Trojan alert via Facebook ads; click to zoom
Well, it's an alert in German, because I'm surfing on a German Windows. But there are identical popups with English texts (or kept in other languages).
At this point, it was clear that this was an attempt to dupe the user into calling Microsoft's fake "security hotline". What happens when you try to call is unclear to me. I could not analyze it in detail. It is also possible that the popup tries to persuade the user in desperation to click the Allow or Deny button (which was terrible translated to German) and a script with further actions is then executed.
Termination only task manager
At this point, I was initially perplexed because I couldn't see a close button ad-hoc – the tabs were hidden. It was clear that I wouldn't click on anything in the popup or button area. I then tried something else by clicking on the favorites bar, but was immediately in full screen mode – the ESC key to close this mode no longer responded as far as I remember. I then used Ctrl+Alt+Del to open the context menu of the Windows shell and selected the command to switch to the task manager.
This ended the full screen mode and the desktop appeared with the task manager window. I then tried again to switch to the browser window, but was again unable to find a tab to close this fake display. I then quickly took a screenshot for documentation purposes and then clicked on the process for the display in the task manager and had it terminated. This killed the entire Chromium clone.
Where does the pop up come from?
In the course of writing the German blog post, I tried to find out a little more. I wanted to find out what was behind the ad and where it came from. A brief attempt to find the target URL in the browser history failed – I assume that everything was done by script, which then displayed the above pop-up.
In a quick search, I found no information on the German phone number shown in the above popup. As mentioned above, I did not click on any button to trigger anything. A right-click did not work in the popup area as far as I remember (otherwise I would have looked at the source code).
In the URL from the screenshot above, however, the string ?utm_medium=paid&utm_scouce=fb&utm_id=120213364759770742 indicates that this popup was displayed via a paid ad on Facebook. And from the URL in the screenshot above, I can see that the URL refers to content at web.core.windows.net, which is where the fake warning was triggered.
Scam from web.core.windows.net already known
This URL windows.net takes you to the blog post Web.core.windows.net Phishing Web Pages – Tech Support Scam. It explains that web.core.windows.net is an Azure blob storage resource and hosting platform used by cybercriminals and online scammers to display static pages with fake virus warnings and computer errors on the user's browser screen.
IThe blog post already presents a popup as shown above, and it says that the popup as well as the URL misleads many users into believing that the fake warnings are from Windows, as the domain is appended with windows.net.
What affected users should do
If someone receives such an ad (which can happen not only on Facebook) and comes across this blog post while searching, here is some information on what to do.
- First of all, keep calm and never call the number displayed – there is a risk that the victim will be tricked into providing payment information so that the fraudsters can deduct payments.
- Under no circumstances should you download and execute anything after being asked to do so (on the page displayed or if you do make a call) in order to unlock or clean up your PC. This is nonsense and serves to install malware.
- Never click on the button, but as mentioned above, use Ctrl+Alt+Del to call up the task manager and end the task for the browser (Google Chrome, Microsoft Edge, Firefox, Safari). Then the spook is over and you can call up the browser again.
However, if you have downloaded and installed something after being prompted to do so and, if necessary, granted a "supporter" from the number called access to the system, the only thing to do is to check the system for malware or have it checked.
The article here also contains some tips on removing malware. However, I don't think it is advisable to do this yourself. The reason: Anyone who falls for the scam is generally not technically fit enough to recognize a malware infection and carry out the necessary steps (reinstalling the system, etc.) themselves. But perhaps the article here will help you to categorize the process and sort it out or resolve it.



