 [English]Brief information for administrators of Sophos firewalls – a reader has informed me that since September 5, 2024, he has been observing increased attempts to attack his Sophos firewalls. And the VPN portal in particular is being flooded with login versions via port 443. The IP from which the attacks are being launched points to Russia. There are indications that hackers are trying to access corporate networks via cracked VPN accesses. Here is the information I have.
[English]Brief information for administrators of Sophos firewalls – a reader has informed me that since September 5, 2024, he has been observing increased attempts to attack his Sophos firewalls. And the VPN portal in particular is being flooded with login versions via port 443. The IP from which the attacks are being launched points to Russia. There are indications that hackers are trying to access corporate networks via cracked VPN accesses. Here is the information I have.
German blog reader Michael works as an administrator in a corporate environment and probably also manages various Sophos firewalls. In a private message on Facebook, he pointed out to me that he and his colleagues were observing a massive wave of login attempts to the firewalls used in the company. He wrote:
Since today we have been experiencing massive password spraying attacks on many Sophos firewalls, especially on the VPN portal, which listens to port 443. Apparently these are attacks from Russia with the IP 92.53.65.166.
The following screenshot (click to zoom) shows the attempts to log in to the VPN portal with username and password. The log shows that these attempts fail due to incorrect login data.
I checked it, the IP address 92.53.65.166 is assigned to Russia, as you can see in the following screenshot. Somehow fits in with the current threat situation.
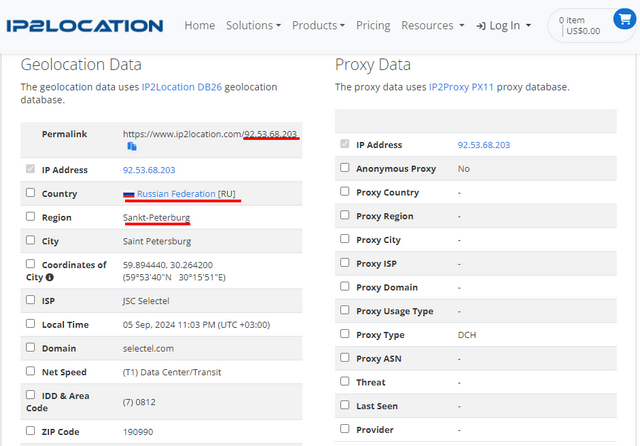
In password spraying, the attackers attempt to log in with frequently used credentials on multiple accounts. The aim of the attackers is to gain access to the Active Directory via poorly secured access using these credentials in order to infiltrate the network from there.
In this context, I recall the case at Microsoft in which the suspected Russian hacker group Midnight Blizzard was able to infiltrate the company's networks. The case came to light in January 2024. The suspected Russian hacker group Midnight Blizzard managed to crack an account on a test system through password spraying attacks. This account was used to access Microsoft's internal mail system from the test system and to read the emails of Microsoft executives and other employees since November 2023 (see Microsoft hacked by Russian Midnight Blizzard; emails exfiltrated since Nov. 2023).

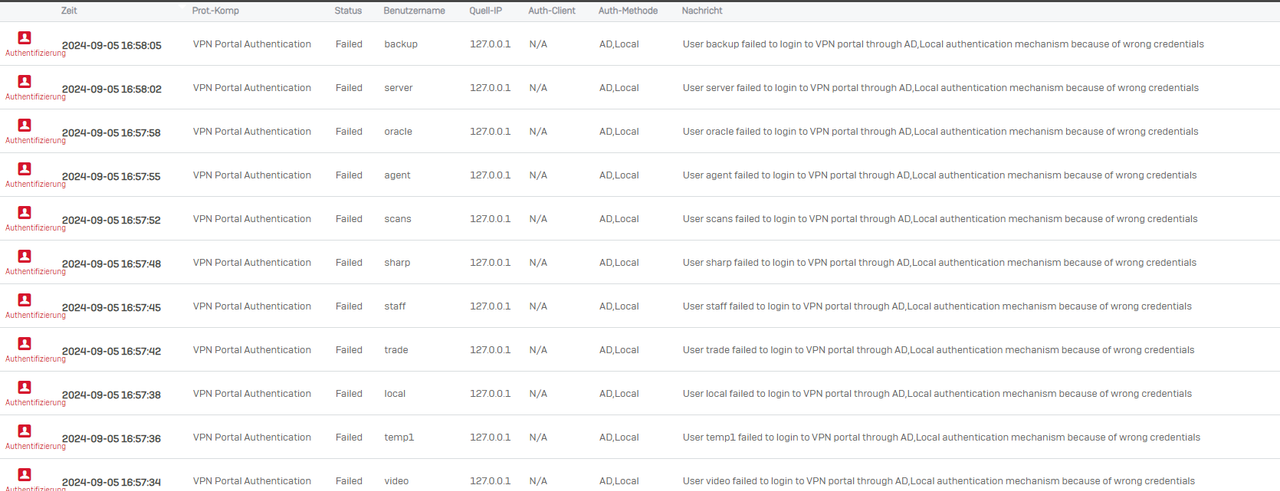



Same thing for me. One of our Sophos firewalls, started on Friday the 6th. Same IP, 92.53.65.166.
Same for us. After blocking this on 9/4, started see new round of attack 9/8 this time for more than 95+ unique IP addresses alternating. Have disabled VPN Portal.