[German]Microsoft security experts have observed various intrusion activities aimed at stealing the credentials of several Microsoft customers. These attacks by suspected state actors (China-Russia) were probably successful and were made possible by password spray attacks or via RDP.
[German]Microsoft security experts have observed various intrusion activities aimed at stealing the credentials of several Microsoft customers. These attacks by suspected state actors (China-Russia) were probably successful and were made possible by password spray attacks or via RDP.
Warning about password spray attacks
The first case concerns suspected Chinese hacker groups who want to steal access data for user accounts. Microsoft published its findings about ongoing cyberattacks on customers by suspected state actors in various tweets at the end of October 2024.
It is said that Microsoft has become aware of intrusion activities targeting several Microsoft customers. Login credentials for these accounts are said to have been successfully stolen. This was made possible by password spray attacks, i.e. the customers did not use two-factor authentication to secure their accounts.
According to Microsoft, the password spray attacks were carried out by a botnet consisting of a network of compromised devices. This botnet is referred to by Microsoft as CovertNetwork-1658, or xlogin and Quad7 (7777).
Microsoft uses the term "CovertNetwork" to refer to a collection of IPs associated with compromised or leased devices that may be used by one or more threat actors. Microsoft believes that a China-based threat actor has established and maintains CovertNetwork-1658.
Microsoft has observed the Chinese threat actor Storm-0940 using credentials from CovertNetwork-1658. Storm-0940 has been active since 2021 and has targeted organizations in North America and Europe, including think tanks, government organizations, NGOs, law firms and the defense industry.
Details can be found in the blog post Research Threat intelligence Microsoft Defender XDR Attacker techniques, tools, and infrastructure 8 min read Chinese threat actor Storm-0940 uses credentials from password spray attacks from a covert network.
Spear phishing via RDP by Midnight Blizzard
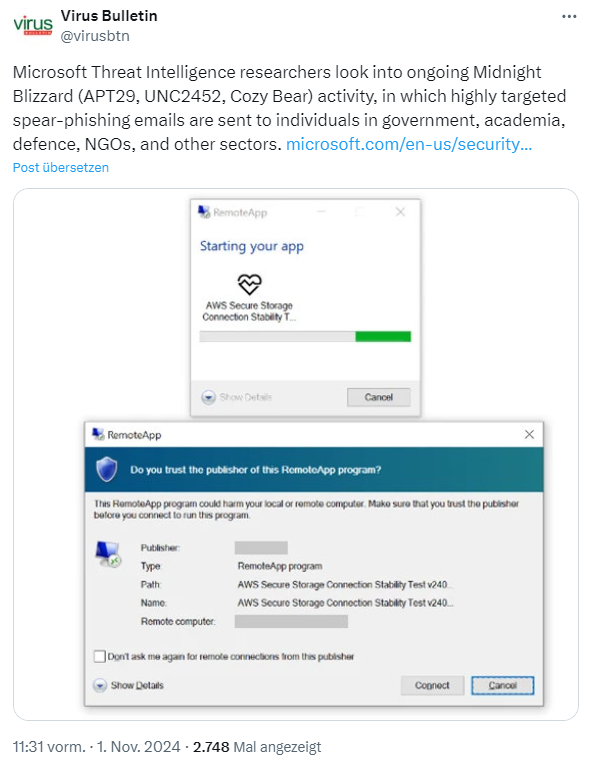
Another threat is posed by the Russian state hacker group Midnight Blizzard, which attempts to penetrate networks by spear-phishing with RDP files. Microsoft Threat Intelligence has observed since October 22, 2024 that the Russian threat actor Midnight Blizzard has been sending a series of targeted spearphishing emails to people in government agencies, universities, defense institutions, non-governmental organizations and other sectors.
Victims are sent a phishing email containing an RDP file. The spear phishing emails in this campaign were sent to thousands of targets in over 100 organizations and contained a signed Remote Desktop Protocol (RDP) configuration file that connected to an actor-controlled server.
In some of the lures, the perpetrators attempted to add credibility to their malicious messages by impersonating Microsoft employees. The threat actor also referred to other cloud providers in the phishing lures. If the victim falls for the bait, the hackers try to collect information about access points.
Microsoft published the details of the campaign and the findings at the end of October 2024 in the blog post Midnight Blizzard conducts large-scale spear-phishing campaign using RDP files.
Florian Roth published the YARA rules for detecting these phishing attacks in this tweet.
Florian Roth @cyb3ropsMicrosoft forgot to include the hashes of the RDP files and I wrote a YARA rule to detect them Hashesdb326d934e386059cc56c4e61695128e 40f957b756096fa6b80f95334ba92034 f58cf55b944f5942f1d120d95140b800 b38e7e8bba44bc5619b2689024ad9fca e1d7de6979c84a2ccaa2aba993634c48 f7e04aab0707df0dc79f6aea577d76ea 48ed82f14472518251086afc26d886ea 3d7e2ee43faf15c1776aa0277db1c2a5 280ab6fa6087c57b43cd5ac6c257082c