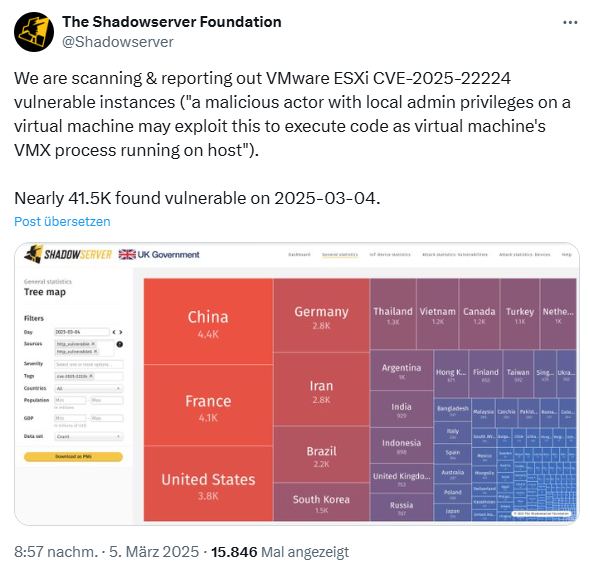
[German]This week, VMware by Broadcom has released security updates for various products, including VMware ESXi servers, to close security gaps. One vulnerability has already been exploited as a 0-day. Now The Shadowserver Foundation warns that over 37,000 VMware ESXi servers are vulnerable via CVE-2025-22224. Germany is also represented with several thousand installations.
[German]This week, VMware by Broadcom has released security updates for various products, including VMware ESXi servers, to close security gaps. One vulnerability has already been exploited as a 0-day. Now The Shadowserver Foundation warns that over 37,000 VMware ESXi servers are vulnerable via CVE-2025-22224. Germany is also represented with several thousand installations.
VMware security advisory and updates
VMware by Broadcom published a security advisory on March 4, 2025 to warn of three zero-day vulnerabilities CVE-2025-22224, CVE-2025-22225 and CVE-2025-22226). One of these vulnerabilities may have already been exploited in the wild and patching is strongly advised.
According to the advisory VMSA-2025-0004, the vulnerabilities affect VMware ESXi, Workstation and Fusion. The vulnerability CVE-2025-22224 in VMware ESXi (and Workstation) is a Time-of-Check Time-of-Use (TOCTOU) bug that leads to an out-of-bounds write. VMware has rated the severity of this issue as critical, with a maximum CVSSv3 base score of 9.3. I reported on the issue in the blog post0-day vulnerabilities in VMWare ESXi, Workstation and Fusion.
37,000 ESXi servers vulnerable via CVE-2025-22224
Now The Shadowserver Foundation warns that over 37,000 VMware ESXi servers are vulnerable to CVE-2025-22224. I became aware of this via the following post.
According to The Shadowserver Foundation's website, a search for the USA found around 3,800 unpatched VMware ESXi servers as of March 4, 2025.
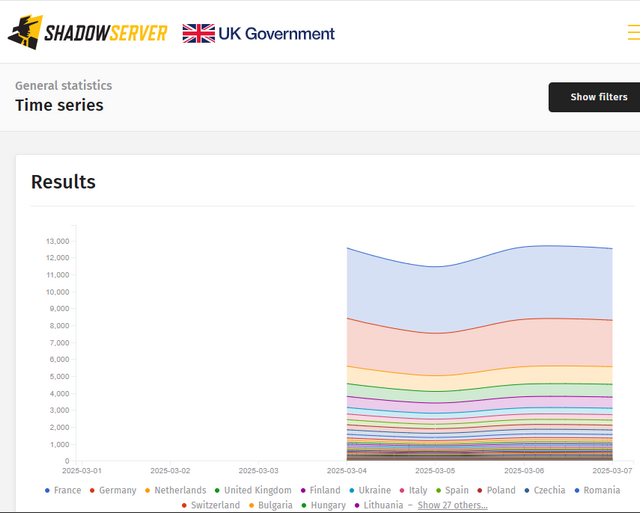
I took a look at the following days – the number drops and then rises again until March 7, 2025. The curve of the patch status over time shown in the screenshot above for Europe also shows this dip.
This is something that cannot really be explained logically. How can the number of vulnerable servers decrease briefly, only to increase again a day later? One explanation that comes to mind would be that the administrators took their VMware ESXi servers offline for a day after the warning from Broadcom.