[German]A small addendum from this week. A few days ago, I came across the news on X that the US company Oracle had been hacked. Oracle as a company denies a hack. But companies listed in the Oracle data captured by the hacker confirm that data used by them was found there. The hack, it is true, could affect many Oracle customers. Here's a rundown of what's known so far.
[German]A small addendum from this week. A few days ago, I came across the news on X that the US company Oracle had been hacked. Oracle as a company denies a hack. But companies listed in the Oracle data captured by the hacker confirm that data used by them was found there. The hack, it is true, could affect many Oracle customers. Here's a rundown of what's known so far.
Rumors of Oracle hack since March 21, 2025
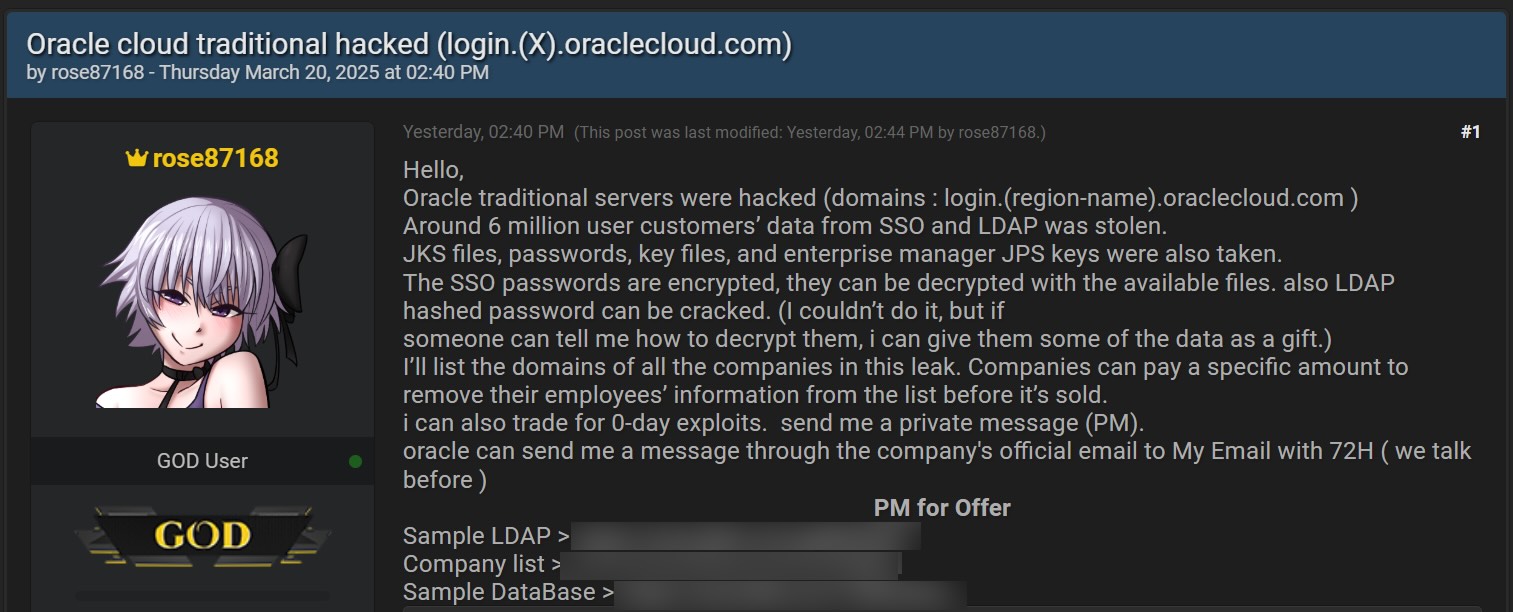
A week ago, I came across rumors of a hack of the US company Oracle on X in tweets. A threat actor with the alias rose87168 claimed to have penetrated the Oracle cloud servers and fished out data. The attacker claimed to have captured authentication data and encrypted passwords from 6 million users.
Post about the Oracle hack; source: Bleeping Computer
Furthermore, the threat actor claimed that stolen SSO and LDAP passwords could be decrypted using the information in the stolen files (see screenshot above). He offered to share some of the data with anyone who could help recover it. He had published several text files of a sample database with LDAP information. There was also a list of companies whose LDAP information was allegedly stolen from the Oracle Clouds SSO platform.
I hadn't picked up on this due to sparse information. Also because the colleagues from Bleeping Computer had discussed a statement from Oracle in the article Oracle denies breach after hacker claims theft of 6 million data records. At the time, the US manufacturer denied that a hack had taken place.
No, but oh! Oracle probably hacked after all
Oracle has now had to row back, as Oracle customers have confirmed to Bleeping Computer that they found their own data in the published examples, which originated from the Oracle Cloud SSO platform. The colleagues from Bleeping Computer picked up on this yesterday in the article Oracle customers confirm data stolen in alleged cloud breach is valid.
Allegedly, LDAP data and a list of 140,621 domains from companies and government agencies are affected by the alleged security breach. The threat actor is now trying to sell this data on underground forums.
Bleeping Computer states that several unnamed companies have stated that they have found LDAP display names, email addresses, first names and other identifying information in the records, all of which are correct and belong to the company.
Bleeping Computer also has emails from the threat actor that were exchanged with the Oracle address secalert_us@oracle.com. Furthermore, the editors also have alleged reply emails from Oracle, although it cannot be verified whether this is all true.
Further information on the hack
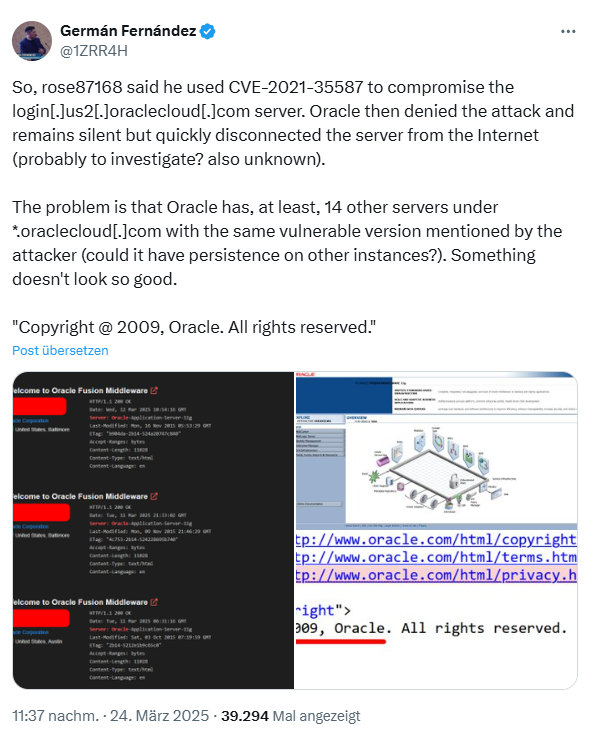
In the following tweet, a security researcher reveals some details as early as March 24, 2025. He writes that rose87168 claims to have used the vulnerability CVE-2021-35587 in the Oracle Access Manager of Oracle Fusion Middleware (in the OpenSSO Agent) to compromise the server login[.]us2[.]oraclecloud[.]com.
He says also: "Oracle then denied the attack, but quickly disconnected the server from the Internet (probably to investigate). The security researcher writes: "The problem is that Oracle has at least 14 other servers at *.oraclecloud[.]com with the same vulnerable version mentioned by the attacker." This all doesn't really look so good."
The cyber security company Cloud-Seek already published a range of information and details on March 21, 2025 in the article The Biggest Supply Chain Hack Of 2025: 6M Records Exfiltrated from Oracle Cloud affecting over 140k Tenants and updated the article on March 27, 2025). The above screenshot of the threat actor and further material from "rose87168" can be found within the Cloud-Seek article.
The compromised database is said to contain 6 million data records originating from Oracle Clouds SSO and LDAP. JKS files, encrypted SSO passwords, key files, Enterprise Manager JPS keys, etc. were found in the data records.
The list of affected clients comprises more than 140,000 entries (including Adidas, Nike, Mastercard, Visa, etc.), and the threat actor is asking the companies on the list to contact him. The aim is for the companies to pay a certain "fee" to have their data removed from the database.
Particularly explosive is the information that the Oracle Fusion Middleware servers were last updated on "Sat, 27 Sep 2014" according to fofa. Oracle Fusion Middleware had a critical vulnerability CVE-2021-35587 affecting Oracle Access Manager (OpenSSO Agent). This was included in the CISA KEV (Known Exploited Vulnerabilities) in December 2022.
The article The Biggest Supply Chain Hack Of 2025: 6M Records Exfiltrated from Oracle Cloud affecting over 140k Tenants provides further details and suggestions on what companies that have fallen victim can do. Orca-Security has also taken up the topic in this article and suggests securing the "Oracle Cloud with the Orca platform".
Note: Oracle says, if I read it correctly at Bleeping Computer, that the data did not originate from OCI (stands for Oracle Cloud Infrastructure). However, the screenshot of the hacker (see above) claims that the traditional Oracle servers were hacked via login.(region-name).oraclecloud.com. There is some uncertainty for me here, because OCI does not seem to me to be the "traditional" Oracle Cloud mentioned above. I am not in a position to judge whether the statements in this German comment at heise are valid.