[German]I'll pull out a topic in a post that I came across recently. Microsoft is trying to increase the security of MS 365. To this end, "Secure by default settings" for outdated authentication protocols will be introduced in Microsoft 365 from mid-July 2025. Administrators must take this into account.
[German]I'll pull out a topic in a post that I came across recently. Microsoft is trying to increase the security of MS 365. To this end, "Secure by default settings" for outdated authentication protocols will be introduced in Microsoft 365 from mid-July 2025. Administrators must take this into account.
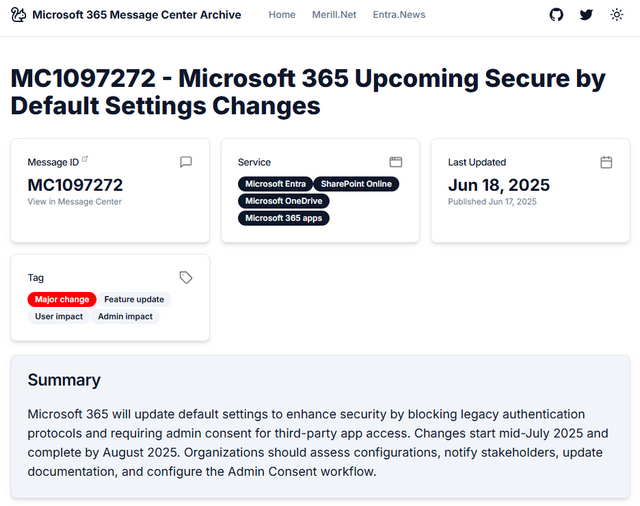
Microsoft 365 secure by default settings
Microsoft wants to increase security under Microsoft 365 and is therefore introducing so-called Secure by Default settings. In the article MC1097272 – Microsoft 365 Upcoming Secure by Default Settings Changes, Microsoft announced various changes for Microsoft 365 in the MS365 Message Center on June 18, 2025.
As part of the Microsoft Secure Future Initiative (SFI) and in line with the "Secure by Default" principle, Microsoft is announcing an update to the Microsoft 365 default settings.
In the default settings of Microsoft 365, authentication protocols that are outdated will be blocked in the future. The administrator's consent will then be required to access third-party applications.
The changes will begin in mid-July 2025 and should be completed by August 2025. Microsoft specifies the following changes in the settings:
- Block legacy browser authentication to SharePoint and OneDrive using RPS (Relying Party Suite): Legacy browser authentication to SharePoint and OneDrive with RPS (Relying Party Suite) Legacy authentication protocols such as RPS (Relying Party Suite) are vulnerable to brute force and phishing attacks due to outdated authentication. Blocking these protocols prevents applications that use outdated methods from accessing SharePoint and OneDrive via the browser. Legacy browser authentication can be blocked using PowerShell via Set-SPOTenant.
- Block FPRPC (FrontPage Remote Procedure Call) protocol for Office file opens: FrontPage Remote Procedure Call (FPRPC) is a legacy protocol used for creating remote web pages. Although it is no longer widely used, legacy protocols such as FPRPC can be more vulnerable to attacks. Blocking FPRPC will help to reduce vulnerability. This change will block FPRPC from opening files, preventing the use of this outdated protocol in Microsoft 365 clients.
- Require admin consent for third-party apps accessing files and sites: If third-party apps are allowed access to file and website content by the user, this can lead to an organization's data being leaked. Requiring administrators to consent to this access can help prevent unwanted access to data by these apps. With this change, the app consent policies managed by Microsoft will be enabled and users will no longer be able to consent to third-party apps accessing their files and websites by default. They will need to ask administrators to give consent. Administrators can also configure granular app access policies, such as restricting user access to the application for specific users or groups.
Microsoft advises organizations to review their configurations, notify stakeholders, update documentation and configure the admin consent workflow. Details can be found in the announcement MC1097272.