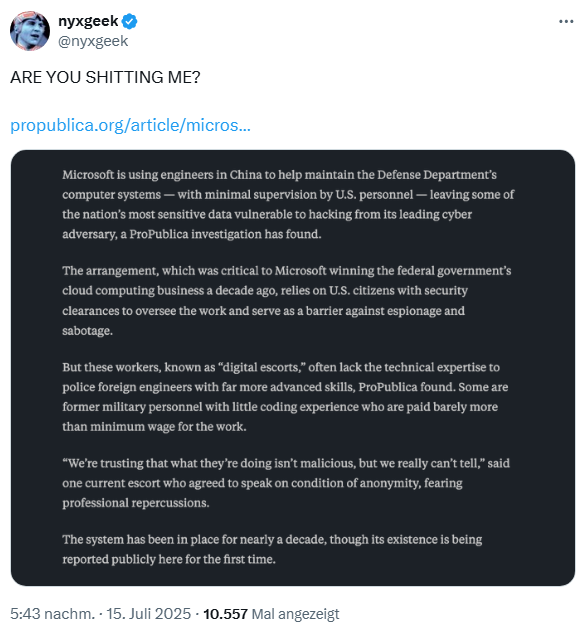
[German]It's a "bombshell" that ProPublica has just dropped. Microsoft is using engineers in China to maintain the US Department of Defense's cloud computer systems. There is only minimal monitoring by poorly qualified American personnel. Microsoft has so far ignored all warnings that this opens the door to cyber espionage or attacks.
[German]It's a "bombshell" that ProPublica has just dropped. Microsoft is using engineers in China to maintain the US Department of Defense's cloud computer systems. There is only minimal monitoring by poorly qualified American personnel. Microsoft has so far ignored all warnings that this opens the door to cyber espionage or attacks.
There is not only political enmity between the USA and China, but also economic competition, at least as far as public statements are concerned. Only Microsoft relies on "change through trade" or "manpower is cheaper in Asia than in the USA". In the age of the Internet, it is also no problem to hire a squad of administrators or software engineers in China to create and develop for Microsoft.
Staff from China hired for critical tasks
A few hours ago, I came across the following tweet about the article A Little-Known Microsoft Program Could Expose the Defense Department to Chinese Hackers by ProPublica. This article sheds a whole new light on Microsoft's relationship with China and how it deals with its (cloud) customers and their security requirements.
The medium reports that Microsoft is deploying engineers in China to maintain the computer systems of the Ministry of Defense (probably referring to the cloud that Microsoft operates for the ministry). The Department of Defense is somehow aware of this. But the agreement with the US Department of Defense, which was instrumental in Microsoft winning the US government's cloud computing business nearly a decade ago, is based on the requirement that US citizens with security clearances monitor the work of Chinese employees as "digital escorts". The digital escorts were to serve as a barrier against espionage and sabotage. It has roughly the same quality as a dog guarding the sausage on the table in the kitchen.
Supervisors has no clue
ProPublica's research has found that the US employees who are supposed to supervising and controlling the work of their Chinese counterparts often don't have a clue and don't have the expertise to judge what people are doing.
According to ProPublica, US employees often lack the technical know-how to "escort and supervise" foreign engineers from China with far more advanced skills. Some of the US employees are said to be former military personnel with little programming experience, who are paid little more than the US minimum wage for their work. It was important for the hiring that they had a security clearance from previous jobs.
"We trust that what they [Chinese employees] are doing is not malicious, but we really can't tell," ProPublica quotes a US employee who wishes to remain anonymous and works as a digital escort.
Common but "unknown" practice for around 10 years
ProPublica writes that Microsoft has probably been doing this for almost 10 years and claims to have disclosed details of the "escort model" to the US federal government. This model, in which the Chinese wait but US officials supervise, does not appear to be publicly known.
During its research, ProPublica interviewed former government employees. However, according to the article, they had never heard of this model with the "digital companions". Even the Department of Defense's IT department had trouble finding anyone who was at least aware of the arrangement. "Literally no one seems to know anything about it, so I don't know how to proceed," Deven King, spokesman for the Defense Information Systems Agency, told Medium.
National security and cybersecurity experts interviewed by ProPublica were also surprised that such an agreement was reached. This is especially true knowing that even at the time the agreement was made, US intelligence agencies and senior members of Congress and the Trump administration considered China's digital capabilities to be the greatest threat to the US.
Risks ignored by Microsoft managers
The ProPublica article is very comprehensive and sheds light on many aspects. In my opinion, the article is likely to stir up a lot of dust. On the one hand, the USA and Microsoft accuse Chinese state hackers of being responsible for attacks on US computer systems. On the other hand, Microsoft is "passing the buck" through shady contract constructions that are hardly known to the public.
The article shows the risks of the Microsoft cloud – hardly anyone in the US administration understands the concept and everyone assumes that only Microsoft employees with security clearance have access to the Department of Defense's IT systems.
Pradeep Nair, a former vice president at Microsoft, who says he was involved in the development of the concept from the beginning, was interviewed by ProPublica. According to him, the strategy behind the "digital escorts" was to enable Microsoft to "get to market faster [with its cloud offerings]". This was the only way Microsoft was able to win important cloud contracts from the US government. Security issues were systematically negated by Microsoft executives. Nair told ProPublica that the "digital escorts" undergo "role-specific training" before being deployed. In addition, a series of security precautions, including audit logs, the digital trail of system activity, would alert Microsoft or the government to potential problems.
"As these controls are very strict, the residual risk is minimal," says ex-Microsoft manager Nair. In the ProPublica article, however, former Microsoft employees also have their say, warning against the chosen strategy of digital escorts and raising massive security concerns. These concerns were ignored and some employees left Microsoft as a result.
If one were to be malicious and speculate, strange questions arise. How was it possible for the Chinese group Storm-0558 to steal an AAD key and gain full access to Microsoft's cloud, including Outlook online accounts? If you read the ProPublica article, this is further proof of the old saying "With friends like this, there's no need for enemies". "If you rely on Microsoft, you no longer need to worry about security" (everything is open anyway). No matter how much the Microsoft management tries to appease them. But I fear that the managers on the carpet floors around the world will have to go through the "learning through extreme pain" therapy a few more times before the first ones wake up and draw the consequences.
Similar articles:
China hacker (Storm-0558) accessed Outlook accounts in Microsoft's cloud
Follow-up to the Storm-0558 cloud hack: Microsoft is still in the dark
After CISA report on Storm-0558 hack, Microsoft provides customers with enhanced cloud logging
Stolen AAD key allowed (Storm-0558) wide-ranging access to Microsoft cloud services
Microsoft's Storm-0558 cloud hack: US senator among the victims
Microsoft's Storm-0558 cloud hack: MSA key comes from Windows crash dump of a PC
Microsoft extends Purview logging (after Storm-0558 hack)
Microsoft as a Security Risk? U.S. senator calls for Microsoft to be held accountable over Azure cloud hack– Part 1
Microsoft as a Security Risk? Azure vulnerability unpatched since March 2023, heavy criticism from Tenable – Part 2
Microsoft hacked by Russian Midnight Blizzard; emails exfiltrated since Nov. 2023
Hewlett Packard Enterprise (HPE) hacked by Midnight Blizzard since May 2023
Microsoft confirms: Russian spies (Midnight Blizzard) stole source code while accessing systems
Microsoft slammed for a cascade of faults that leads to Storm-0558 cloud hack