[German]The extent of the observed wave of attacks on 0-day vulnerabilities in Microsoft SharePoint is slowly becoming apparent. Microsoft has now released emergency updates for SharePoint Server. However, it is now known that over 400 organizations have probably been compromised. And it is clear that attackers are also infecting SharePoint servers with ransomware. I will briefly summarize the new information in a follow-up article.
[German]The extent of the observed wave of attacks on 0-day vulnerabilities in Microsoft SharePoint is slowly becoming apparent. Microsoft has now released emergency updates for SharePoint Server. However, it is now known that over 400 organizations have probably been compromised. And it is clear that attackers are also infecting SharePoint servers with ransomware. I will briefly summarize the new information in a follow-up article.
The 0-day exploit and attacks since July 18, 2025
Since July 18, 2025, various security providers such as Sophos etc. have observed increased waves of attacks on Microsoft SharePoint servers that are accessible via the Internet. In addition to a (ToolShell) exploit that exploited the vulnerabilities CVE-2025-49704 and CVE-2025-49706 patched on July 8, 2025, there were other unpatched 0-day vulnerabilities (CVE-2025-53770 and CVE-2025-53771).
These were attacked by an exploit in the course of Friday and Saturday. I had traced the development in the blog post Sharepoint servers are attacked via 0-day vulnerability (CVE-2025-53770). In the meantime, Microsoft has released special updates for various SharePoint Server versions to close the vulnerabilities (see Patches for Sharepoint Server 2016; China behind attacks, approx. 400 organizations compromised).
Over 400 organizations compromised
The extent of the incident is slowly becoming apparent. While more than 80 victims were known until last weekend, the number soon rose to 100, including the US Nuclear Weapons Agency, according to Bloomberg. The latest number of compromises is over 400 victims, as The Register reports here. Most of the affected systems are located in the US and Germany.
Advice from ESET Research
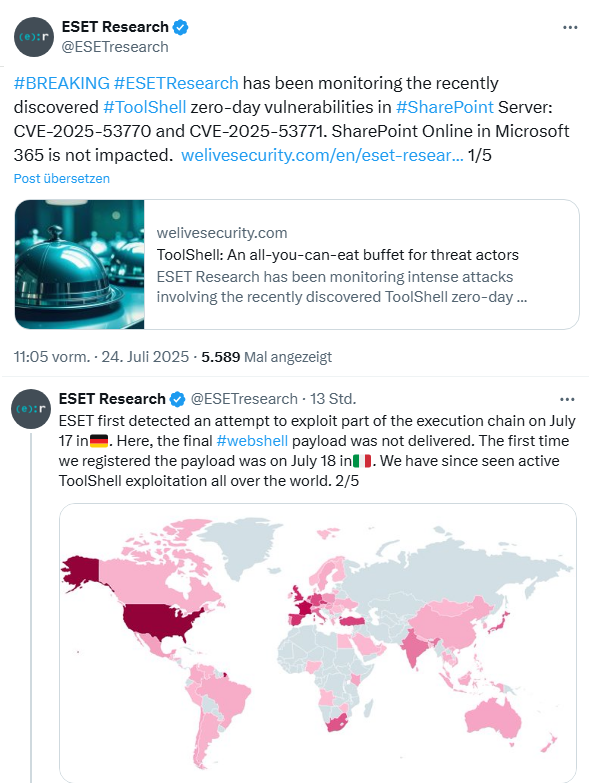
ESET Research has traced the development in a series of tweets. First attacks via an exploit that takes advantage of the chained vulnerabilities were observed on July 17, 2025. The first WebShell was delivered by attackers as a payload to systems in Italy on July 18, 2025.
ESET Research has discovered several IP addresses used in the July 17-22, 2025 attacks. However, the ToolShell exploit is being used by all kinds of threat actors, from small cybercriminals to state-sponsored groups, including Chinese APTs.
The security researchers have summarized their findings on July 24, 2025 in the blog post ToolShell: An all-you-can-eat buffet for threat actors. The article provides details on ToolShell, the indicators of compromise (IoC), a list of IP addresses from which attacks originate and tips on countermeasures. Administrators of SharePoint servers should read the countermeasures and the information on how to detect a compromise.
An exploit module for penetration testing, developed by Rapid 7, which exploits the vulnerabilities mentioned above, is described on GitHub.
Microsoft provides insights: Warlock ransomware infections
Microsoft had already published the blog post Disrupting active exploitation of on-premises SharePoint vulnerabilities on July 22, 2025 with more details on the above-mentioned vulnerabilities, notes on compromise, analysis and countermeasures.
Microsoft wrote that at the time of writing, they had already observed two Chinese actors, Linen Typhoon and Violet Typhoon, exploiting these vulnerabilities on web-accessible SharePoint servers. In addition, Microsoft security experts have observed another China-based threat actor (Storm-2603) exploiting these vulnerabilities.
On July 24, 2025, Microsoft Thread Intelligence pointed out an update to the article Disrupting active exploitation of on-premises SharePoint vulnerabilities from July 23, 2025 in the above tweet.
Continuous monitoring of Storm-2603 exploit activity, including advanced analysis, has led to the discovery of the use of Warlock ransomware on compromised systems. Microsoft then updated the Attribution, Indicators of Compromise, and Enhanced and More Specific Mitigation and Protection Recommendations sections based on this new information. Administrators of SharePoint servers should read through this article and the ESET Research article above and work through the recommendations.
Microsoft SharePoint 365, the online version of this software, does not appear to be affected by the 0-day vulnerabilities.
Similar articles:
Sharepoint servers are attacked via 0-day vulnerability (CVE-2025-53770)
Patches for Sharepoint Server 2016; China behind attacks, approx. 400 organizations compromised