[German]Anyone who believed that Microsoft's Recall was at the forefront of surveillance needs to think again. Security researchers have discovered the FreeVPN.One extension for the Google Chrome browser. This extension took screenshots of all visited pages and collected additional data. The extension has now been removed from the Google Chrome Store.
[German]Anyone who believed that Microsoft's Recall was at the forefront of surveillance needs to think again. Security researchers have discovered the FreeVPN.One extension for the Google Chrome browser. This extension took screenshots of all visited pages and collected additional data. The extension has now been removed from the Google Chrome Store.
I came across the topic this week on Tuta via the following tweet, which is discussed in more detail in the article Chrome VPN Extension With 100k Installs Screenshots All Sites Users Visit.
It's freeeee, your VPN – take it …
VPN.one offers a Chrome extension FreeVPN.One with big promises: The free FreeVPN.One prevents your network operator from spying on your internet traffic and at the same time ensures the fastest possible speeds available to you. The privacy statements don't look bad either. But it's noticeable that the site doesn't even have an imprint with the company address. I assume that the operator is based in Hong Kong, but I may be wrong. Data protection or privacy statements are therefore "smoke and mirrors" – one of the reasons why I refuse to publish tests or sponsored articles about VPNs here in my blog.
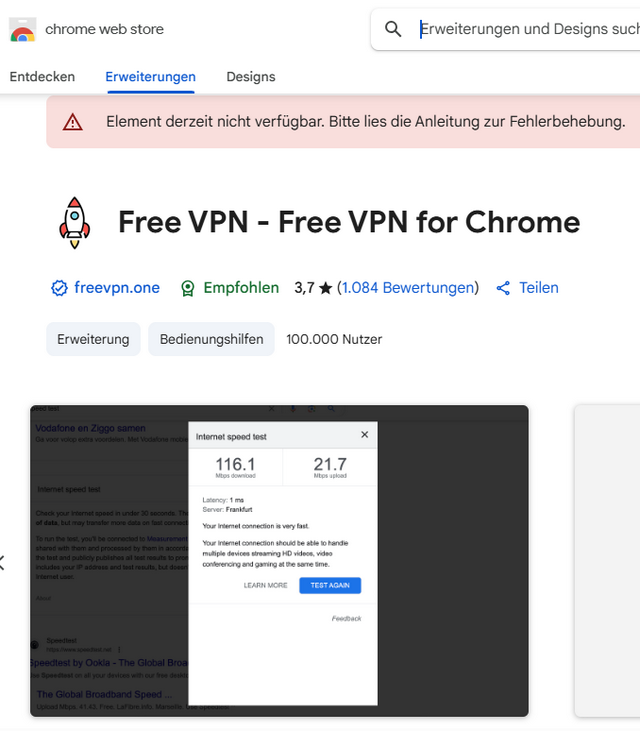
The Chrome extension is currently no longer available in the Google Chrome Store (why, one wonders), but it has been downloaded 100,000 times.
Hey dude, nothing is free…
Security researchers at Koi Security revealed the true value of the above promises made about the extension in the Google Chrome Store in their August 19, 2025 article SpyVPN: The Google-Featured VPN That Secretly Captures Your Screen. They wrote: With its verification badge in the store, its prominent placement, and over 100,000 installations, FreeVPN.One seemed like a safe choice. But once installed in the Google browser, this extension does not ensure privacy while surfing, but instead constantly monitors the user.
Everything the user subsequently does in the browser is recorded with screenshots and sent to the service operators – recall squared. Just think about all the daily activities you do on the internet, from accessing online accounts, online banking, surfing websites, emails, working with company data, etc.
At this point, the deception becomes clear: the service operator and developer of the extension promises data protection and, in return, forwards everything the user does to their own servers. And users cheer with five-star reviews about how great it all is.
Koi's technical analysis reveals that seconds after a page is loaded, a background trigger takes a screenshot. This is sent along with the page URL, tab ID, and a unique user ID to the following address: aitd[.]one/brange.php. The extension uses a sophisticated two-stage architecture to capture the screenshots.
The page to which the data is uploaded is an AI thread detector designed to immediately detect malicious pages. One (that is thinking 'positive') could say that they are "trying to protect the users." On the page, visitors are "educated" with lofty words about phishing and such things. But reality is cruel: Screenshots are taken in the background without user action or notification by the extension, and without the user noticing or consenting. And the data are sent to the developer.
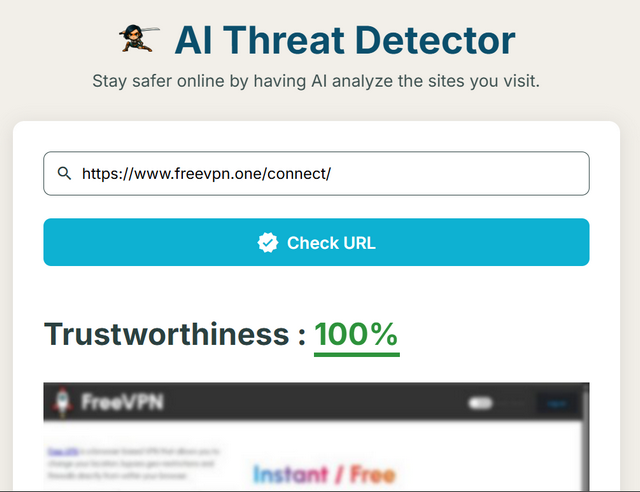
When I visited the site while writing this article, after a while the above pop-up appeared in my open browser tab. It advertised FreeVPN from the above provider – you catch more flies with honey than with vinegar…
This behavior is new … and planned!
For years, according to Koi, FreeVPN.One was simply a VPN extension in the Chrome Web Store that did exactly what it promised. Nothing in the behavior of the VPN tool indicated what was to come.
The update to v3.0.3 in April 2025 opened the door in the form of a change to the permission to <all_urls>. This meant that the extension could now access every website visited – far more than a VPN should need. On May 31, 2025, the domain aitd[.]one was registered.
In June 2025, the update to v3.1.1 was released, and the developer began testing the limits. There was a rebranding to include "AI Threat Detection." In addition, advanced content scripts were added for every website visited, and corresponding script permissions were requested. To users, it looked like a security upgrade. In reality, according to Koi, the developer was experimenting to see how far he could go without arousing suspicion.
With version 3.1.3 released on July 17, 2025, the developer then put all his eggs in one basket, and the spying began with the secret taking of screenshots on every website visited. The location was tracked and the device data was collected and sent to the new domain aitd[.]one.
Then the developer must have realized that his tricks were detectable. With version v3.1.4 from July 25, 2025, they began to cover their tracks. The developers implemented AES-256 encryption and RSA key wrapping and switched to a new subdomain scan[.]aitd[.]one. The behavior remained the same, but the mess was harder to detect.
What started as a trustworthy VPN was now a surveillance tool for all of the users' online activities. The developers received "Verified" status from Google at the same time and were even featured in the Chrome Web Store.
Think about that for a moment: the Google Chrome Store team claims to perform security checks on new versions of extensions using automated scans, manual reviews, and monitoring for malicious code or behavioral changes. In reality, this is just "whitewash," because these security measures have failed.
This case shows that even with these protective measures, dangerous extensions can slip through, pointing to serious security gaps in the major browser marketplaces. So my advice is: stay away from browser extensions unless you have programmed them yourself or they come from the browser developers themselves.
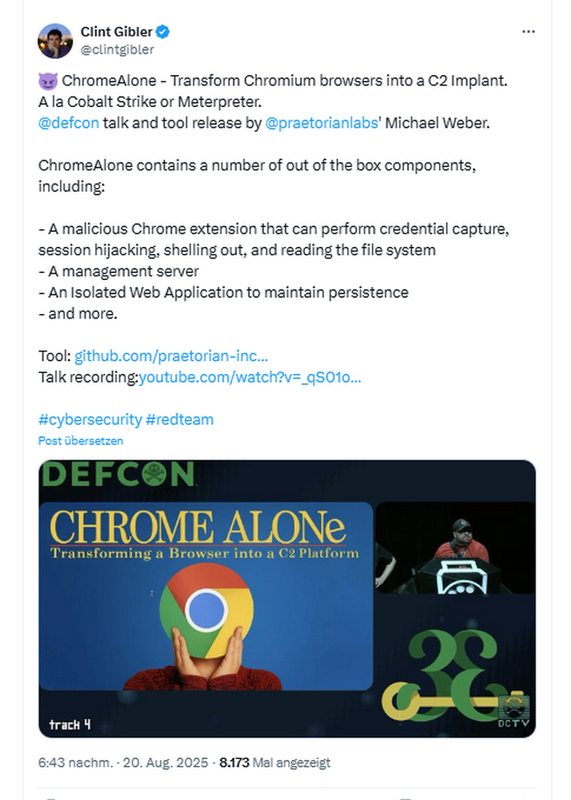
BTW: Clint Gibler introduced in the tweet below ChromeAlone. It can be used to turn Chromium browsers into C2 implants. The tool demonstrates the full range of malicious functions that are possible. Details can be found on GitHub, and a video of a DefCon session is available here.