[German]Many users manage their passwords in password managers. Security researchers took a closer look at 11 popular extensions (1Password, LastPass, iCloud, and others). These were identified as vulnerable, putting login details, 2FA codes, and credit card data at risk.
[German]Many users manage their passwords in password managers. Security researchers took a closer look at 11 popular extensions (1Password, LastPass, iCloud, and others). These were identified as vulnerable, putting login details, 2FA codes, and credit card data at risk.
The report was already made public last week, as the findings had been presented at Defcon – but I'm posting the topic as an addendum to the blog. I became aware of the issue through the following tweet and this article from The Hacker News.
Password managers usually also provide a browser extension to transfer a password from the password storage in the browser to the corresponding input fields of an online account.
Marek Tóth asked himself whether so-called clickjacking would still be an exploitable vulnerability in 2025. Clickjacking is a technique in which an attacker overlays the display of a legitimate website with a copy and then prompts the user to perform seemingly harmless mouse clicks and/or keyboard entries. These actions are then recorded by the attacker.
The conclusion was that if a password manager entered the login details into a clickjacking page, they could easily be stolen by attackers. Marek Toth took a closer look at 11 password managers that come with a browser extension.
In doing so, he discovered a new clickjacking technique in which a malicious script manipulates UI elements that browser extensions insert into the DOM. The UI elements are made invisible using JavaScript, so the user cannot detect a manipulated website.
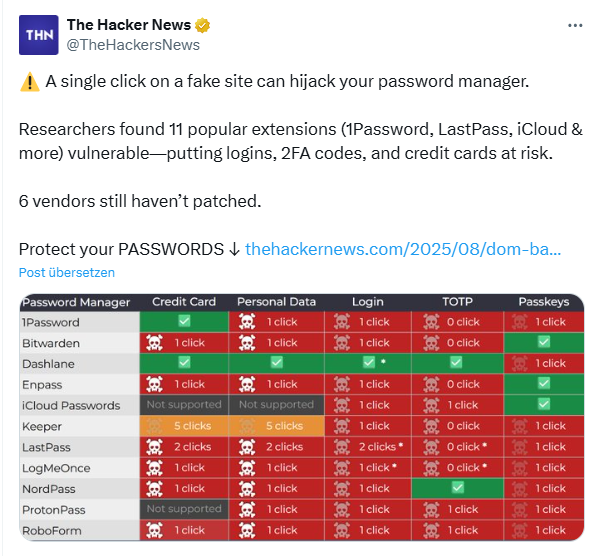
In the investigation of the 11 selected password managers used as browser extensions, it was found that all were vulnerable to "DOM-based extension clickjacking." Millions of users could be at risk (Tóth estimates ~40 million active installations). Here are his findings:
- A single click anywhere on the attacker's website could reveal credit card details, including security codes (6 out of 9 products tested were vulnerable) or stored personal data (8 out of 10 products tested were vulnerable).
- All password managers filled in login details not only for the main domain of the visited website, but also for all subdomains. An attacker could easily find XSS or other vulnerabilities and steal the user's stored login details (10 out of 11) with a single click, including TOTP (9 out of 11). In some scenarios, passkey authentication could also be exploited (8 out of 11).
- All vulnerabilities were reported to the developers in April 2025, with the note that public disclosure would take place in August 2025.
- Some providers have not yet fixed the described vulnerability: Bitwarden, 1Password, iCloud Passwords, Enpass, LastPass, LogMeOnce. Users of these password managers may still be at risk (~32.7 million active installations).
For users of Chromium-based browsers, the security researcher recommends configuring access to websites to "on-click" in the extension settings. This configuration allows users to manually control the autocomplete function. Further details can be found in the article DOM-based Extension Clickjacking: Your Password Manager Data at Risk by Marek Tóth. On August 22, 2025, he wrote in an addendum that the following products were still problematic:
- Bitwarden: 2025.8.1 (in progress), <=2025.8.0 (vulnerable)
- Enpass: 6.11.6 (fixed) – released: 13.8.2025, <=6.11.5 (vulnerable)
- KeePassXC-Browser <=1.9.9.2 (latest) is vulnerable
The Hacker News published the details in this article.