[German]Microsoft warns of the financially motivated group Storm-0501, which continuously targets cloud instances (Azure) with attacks. If successful, data is extracted, the originals are encrypted, and backups are destroyed. A ransom is then demanded.
[German]Microsoft warns of the financially motivated group Storm-0501, which continuously targets cloud instances (Azure) with attacks. If successful, data is extracted, the originals are encrypted, and backups are destroyed. A ransom is then demanded.
Cloud threat: Warning about Storm 0501
In an article titled Storm-0501's evolving techniques lead to cloud-based ransomware dated August 27, 2025, Microsoft warns about the financially motivated threat actor Storm-0501.
Microsoft Threat Intelligence has observed that the financially motivated attacker Storm-0501 is continuously evolving its campaigns. In 2021, Storm-0501 used the "Sabbath" ransomware in an attack on school districts in the United States. In November 2023, Storm-0501 attacked the healthcare sector and changed the distributed ransomware several times over the years (in 2024, the ransomware "Embargo" was used).
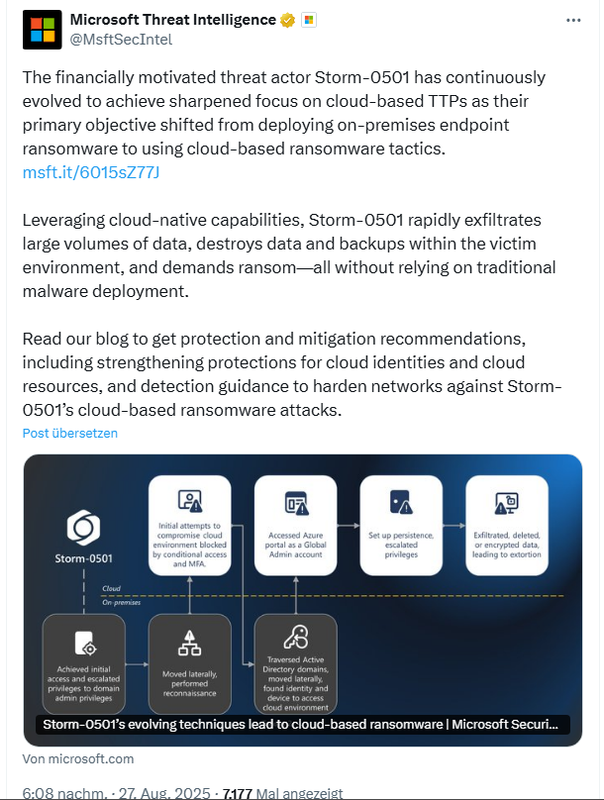
According to Microsoft, the attacker is currently focusing more on cloud-based tactics, techniques, and procedures (TTPs). Redmond writes that the attacker is known for targeting hybrid cloud environments. However, its primary goal has now shifted from deploying local endpoint ransomware to using cloud-based ransomware tactics.
New: cloud-based ransomware
Compared to traditional ransomware groups, which compromise local systems with malware in order to encrypt important files on end devices within the compromised network and then negotiate for a decryption code, there are changes in the cloud. Storm-0501 also uses cloud-native functions for its cloud-based ransomware to quickly exfiltrate large amounts of data, destroy data and backups within the victim's environment, and demand ransom. Thanks to cloud-native functions, attackers no longer have to rely on traditional malware.
In September 2024, it became known how Storm-0501 expanded its local ransomware operations to hybrid cloud environments. The attacker gained access by compromising Active Directory environments. It then moved to Microsoft Entra ID, where it escalated permissions for hybrid and cloud identities to gain global administrator rights. The impact of these attacks took two forms:
- Either backdoors were implanted in Entra ID tenant configurations using maliciously added federated domains to allow login as virtually any user,
- or local ransomware was used to encrypt endpoints and servers, ultimately demanding ransom for the decryption keys.
It doesn't appear in the Microsoft post, but the whole thing reminds me of the exploitation of the CVE-2025-53786 vulnerability, which I mentioned in early August 2025 in the post Microsoft Exchange Server Hybrid at risk by CVE-2025-53786.
Sequence of events in a recent Storm-0501 campaign
In its latest blog post, Microsoft describes the sequence of events in a specific attack on an organization. In this case, Storm-0501 compromised a large company consisting of several subsidiaries. Each of these subsidiaries operates its own Active Directory domain. However, these domains are linked to each other by domain trusts. This enables cross-domain authentication and access to resources.
A complex cloud environment
In its post, Microsoft outlined the victim's environment. Active Directory domains were synchronized with the victim using Entra Connect Sync servers with multiple Entra ID tenants. In some cases, a single domain was synchronized with more than one tenant, further complicating identity management and monitoring.
Various subsidiaries used separate Microsoft Azure tenants with different Microsoft Defender protections. Only one tenant used Microsoft Defender for Endpoint and had integrated devices from multiple Active Directory domains into the license of this single tenant. According to Microsoft, this fragmented deployment led to "visibility gaps" throughout the environment.
Vulnerabilities cleverly exploited
In its lengthy article, Microsoft traces how the attackers cleverly exploited this environment and its vulnerabilities. In the local part of the attack, the attackers checked the endpoints for Defender and then compromised an Entra Connect Sync server that did not use the endpoint security product. Microsoft assumes that this server served as the hub. From there, the attacker set up a tunnel to move laterally within the network.
For this lateral movement, the group used Evil-WinRM, a post-exploitation tool that abuses PowerShell via Windows Remote Management (WinRM) for remote code execution. They also used a DCSync attack, a technique for reading login credentials that allows an attacker to impersonate a domain controller by abusing the Directory Replication Service Remote Protocol and, in this role, retrieve sensitive Active Directory data, such as password hashes for all users in the domain.
Using these stolen credentials, the intruders attempted to log in to several accounts as privileged users. However, they were blocked because the accounts had multi-factor authentication (MFA) enabled.
The group managed to compromise a second Entra Connect server connected to another Entra ID tenant and another Active Directory domain via Active Directory. From there, they launched another DCSync attack. This time, Storm-0501 was able to identify a non-human synchronized identity that had been assigned a global administrator role in Microsoft Entra ID on this tenant. And MFA was not enabled for this identity.
First, the user's local password, which was synchronized (via Entra Connect Sync) with this user's cloud ID, was reset. The attackers then registered a new MFA method under their control and used this account to move laterally between different devices on the network until they finally found a hybrid server that allowed them to log in to the Azure portal with the global administrator account.
Once the attacker managed to access the conditional access policies and log into the Azure portal with a global administrator account, Storm-0501 essentially had complete control over the cloud domain, Microsoft writes. They registered an Entra ID tenant that they controlled as a trusted federated domain. This was the backdoor for Storm-0501, enabling permanent access. This allowed Storm-0501 to create SAML (Security Assertion Markup Language) tokens that were valid for the victim's tenant. From then on, they could impersonate users of the victim's tenant and assume the Microsoft Entra roles of the impersonated user.
Using the compromised global Microsoft Entra administrator account, Storm-0501 gained the Azure role "User Access Administrator," and with it access to all of the company's Azure subscriptions and the data stored in them. The attackers deleted a bunch of data. Data that couldn't be deleted or was supposed to stay undeleted was then encrypted with their own keys using cloud functions. The attackers then blackmailed the victim into paying a ransom. They used a compromised Teams account to make contact and negotiate.
Microsoft provides advice on protection
In the article, Microsoft then provides information on several measures to protect against such Storm-0501 attacks in the section "Mitigation and protection guidance."