 [German]It's a crude situation that I still can't quite wrap my head around. I got reports form users, that for several weeks now, third parties have been accessing Microsoft accounts, as can be seen in their activity history. The users had activated two-factor authentication for their accounts. How can this be? And even more bizarre: readers whom I asked to check their account activity history found nothing there (the same is the case for me and my Microsoft test accounts).
[German]It's a crude situation that I still can't quite wrap my head around. I got reports form users, that for several weeks now, third parties have been accessing Microsoft accounts, as can be seen in their activity history. The users had activated two-factor authentication for their accounts. How can this be? And even more bizarre: readers whom I asked to check their account activity history found nothing there (the same is the case for me and my Microsoft test accounts).
Review of a hacked Microsoft account
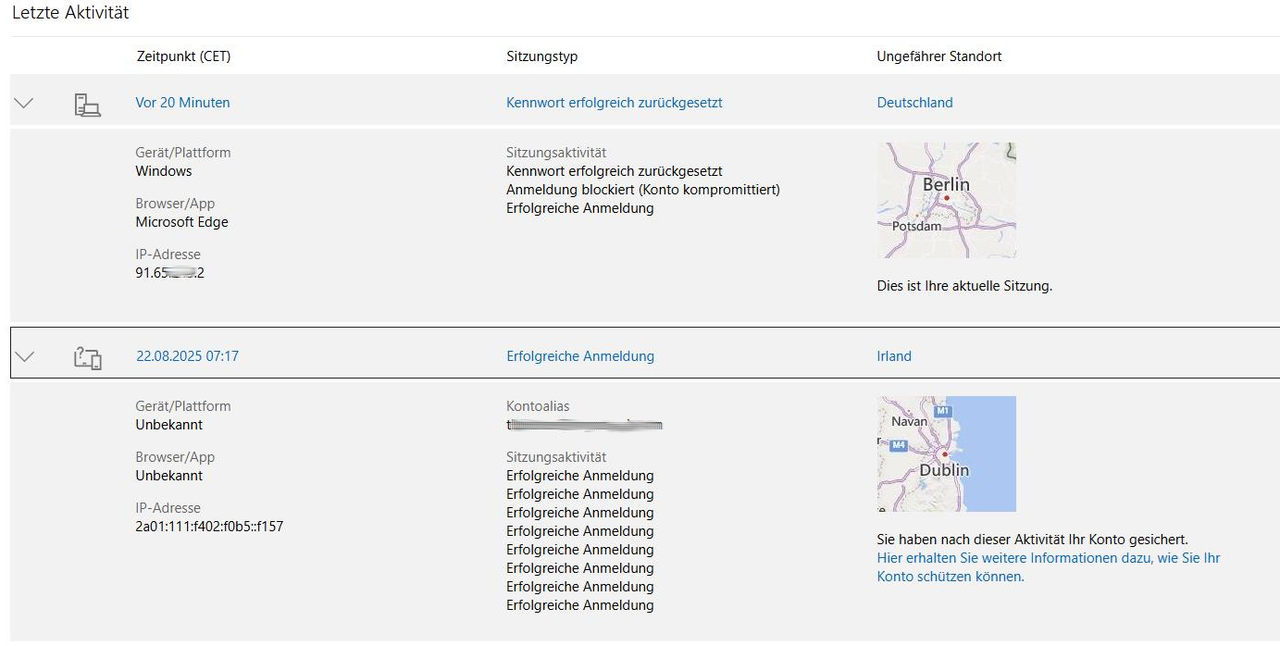
German blog reader Tom pointed out something strange about his Microsoft account. He discovered that unknown third parties had accessed two of his Microsoft accounts.
The screenshot above shows these access attempts for a Microsoft account. Both Microsoft accounts were successfully accessed from an unknown IP address in Ireland. The screenshot above shows the message "Sign-in blocked (account compromised)". At the end of the day, it turned out that his Microsoft account had been compromised and blocked due to SPAM – I reported this in part 1 (the article Has your Microsoft account been hacked? Do you see any unusual activity in your history?).
Further cases known
Shortly after I posted the German version of the blog article from part 1, linked above, several users contacted me with further information.
Case 1 on reddit.com
German blog reader Lukas posted this comment and referred to the reddit.com thread Log in from an different location that belongs to MICROSOFT-CORP-MSN-AS-BLOCK. In it, a user describes how, on July 25, he noticed a successful login to his Microsoft account. Here, too, the user had enabled 2FA and (similar to the above case) did not receive any notification from Microsoft about the unauthorized login.
In this case, nothing happened to my account, and the user only noticed this access later (August 2025) by chance. When he checked the strange IP address from which the access originated, it turned out that it belonged to MICROSOFT-CORP-MSN-AS-BLOCK and was located in Canada.
The user asked, "Do you know what this could be? Is something from Microsoft connecting to my account?" It was really stressful for the person affected; they changed their password and set up Microsoft Authenticator in addition to their other 2FA options. The thread then contained confirmations that this was not an isolated case.
Case 2 in the Microsoft Q&A forum
In the Microsoft Q&A forum, there is a thread titled Microsoft Authenticator- Successful login from unknown account dated July 27, 2025. On July 26, 2025, the owner of a Microsoft account received a number of requests from the Authenticator for access, which he rejected.
He then called up the authenticator to check the latest activities. There, the user discovered that two days earlier, a successful login to his Microsoft user account had taken place from an IP address in Des Moines, Iowa (unknown device/operating system). Again, the user had not received any notification of this login and had not noticed any suspicious activity in the account.
The user flagged the activity as suspicious and changed their password. Here, too, the person affected does not understand why they were not notified. When they searched for the IP address 2a01:111:f402:f139::f148 on the internet, it appeared to be assigned to a Microsoft data center. The user asks if anyone has any idea what might have happened and/or what they should do now to protect their account. Other affected users have posted in the thread, reporting that they also noticed third-party access to their accounts despite 2FA. All IP addresses appear to come from the Microsoft network, and users are not notified of the access.
Case 3 in the Microsoft Q&A forum
Another case is described in the Microsoft Q&A forum in the thread Someone else successfully login without going through authenticator app!!?? dated July 27, 2025. The person affected discovered that on July 26, 2025, someone from another country had successfully logged into their account without having to use the authentication app.
The screenshot shown in the thread is in Chinese and essentially means: Device unknown, browser unknown, login successful, country is the USA. The user writes that they did not even receive a message that someone had tried to log in, and there was no warning at all. The person affected (probably also in China) asks: Is this even possible? Can someone please help me? Here, too, other users confirm this observation with their own accounts.
Suspicion: Outlook app is involved
In the Microsoft Q&A forum thread Someone else successfully login without going through authenticator app!!??, a user writes that they want to respond to the issue of apparently successful IPv6 authentications for some users of Microsoft accounts from various Microsoft data centers.
The poster writes that many people seem to be seeing such activity. He has had this problem about three times, and all of these IPv6 addresses presumably belong to Microsoft, as they all resolve to MICROSOFT-CORP-MSN-AS-BLOCK.
The person affected has noticed that this usually happens when they open the Outlook or OneDrive mobile app (it is not specified whether this is on Android or iOS). The affected person linked to the forum post Why Datacenter IPs are shown when a user logs in, where this issue is discussed. The thread provides what I consider to be an unsatisfactory answer, stating that it is "activity from a smartphone app" (for OneDrive or Outlook) that is sometimes routed awkwardly and listed as "unknown access."
In the reader feedback on my German blog post Microsoft Konto gehackt? Seht ihr fremde Aktivitäten im Verlauf? , one user posted this comment. He also found an IPv6 call from Canada in his history. He remembered that at the time of this call, he had to reconfirm his outlook.com login details in Apple Mail on his iPhone.
Somehow, it all seems inconsistent—in the first case I discussed in my German post Microsoft Konto gehackt? Seht ihr fremde Aktivitäten im Verlauf?, Thomas B.'s account was blocked due to spam activity. However, according to Thomas, he does not use an iPhone or iPad (to check his email). So something unpleasant has happened.
The reader referred to the forum thread Microsoft sign in from IPv6 associated with Microsoft at Microsoft Q&A, where the same thing as outlined above is described. That would be case 4 in the above nomenclature, and the thread in question already has four pages of responses from affected users.
It is suspected that the logins are coming from Microsoft, which apparently does not require 2FA for access. Possibly for porn scans, or for CoPilot, or for maintenance purposes. This behavior has been observed since 2020, with no conclusive explanation from Microsoft.
It is also incomprehensible that some users simply cannot see certain activities in the history. It appears to me that accesses without 2FA are taking place from the Microsoft infrastructure, which may not be logged and do not require 2FA. And if something happens, the account owner has little chance of doing anything about it. If I were defeatist, I would say that Microsoft has slowly lost control of its cloud stuff. But maybe there is an explanation after all, and it will be disclosed why the first case I picked up, that of Thomas B., led to a compromised account despite 2FA.
Articles:
Has your Microsoft account been hacked? Do you see any unusual activity in your history? – Part 1
Unauthorized logins to Microsoft accounts despite 2FA – Part 2




Could the cause be a National Security Letter?
Do we know if the people experiencing this might be "People of Interest"?