[German]On the evening of September 19, 2025 (Friday), there was a ransomware attack on the service provider Collins Aerospace, which operates, among other things, check-in systems for airports. As a result, numerous flights were canceled over the weekend (in Europe – and in other parts of the world), and the IT disruptions at the service provider continue to this day. Here is a brief review of what went wrong and what is still wrong. And there has been an arrest in connection with this incident. And there is a clue as to the type of ransomware used.
[German]On the evening of September 19, 2025 (Friday), there was a ransomware attack on the service provider Collins Aerospace, which operates, among other things, check-in systems for airports. As a result, numerous flights were canceled over the weekend (in Europe – and in other parts of the world), and the IT disruptions at the service provider continue to this day. Here is a brief review of what went wrong and what is still wrong. And there has been an arrest in connection with this incident. And there is a clue as to the type of ransomware used.
A brief review of the weekend
Early on Saturday morning, September 20, 2025, reports circulated in the media that flights were being canceled at numerous European airports "due to computer problems at check-in"—because check-in had to be done manually with paper and pencil.
As a result, numerous flights were canceled at airports in Berlin, Brussels, and Heathrow (London), and passengers were stuck at departure terminals.
The above Mastodon post refers to a BBC article on London Heathrow. I myself reported on this in more detail in a German and an English blog post (see Cyberattack on airport service provider; delays at European Airports (September 20, 2025)). Initially, it was reported that there was a technical malfunction in the check-in system, but later further information was made public.
It quickly became known that a cyberattack on airport service provider Collins Aerospace was the common cause. It is now reported that there was a ransomware attack. Normally, this would not have had a major impact on air travel check-in operations if the airlines had not completely outsourced their check-in processes to Collins Aerospace. Collins Aerospace offered check-in services for various airlines.
This meant that all airports that relied on the Collins Aerospace check-in system were affected. In addition to Berlin Brandenburg International (BER), these included the airports in Brussels and London (Heathrow). But there are a number of other smaller airports that were not named. A post on Mastodon mentions several other airports; in Germany, Münster was affected in addition to Berlin (BER), and according to the post, Cologne/Bonn was also affected.
A look at the details of what happened
I found what has since become known behind the scenes more exciting. Namely, the first indications of outdated software and fatal dependencies.
Who is Collins Aerospace?
In my blog post linked above, I already mentioned that Collins Aerospace was founded in 2018. It is a US aerospace and defense technology company and a subsidiary of RTX Corp., formerly Raytheon Technologies. Raytheon is also involved in cybersecurity.
The attack took place on "ARINC." ARINC is an abbreviation for Aeronautical Radio Incorporated, a company founded in 1929 and based in Minneapolis, USA. Kevin Beaumont outlined the history of Collins Aerospace in this post.
To sum it up: At the end of the day, ancient companies and systems were bought up and are now operating under the name Collins Aerospace. In my blog post, I wrote the other day, "Collins offers technology that allows passengers to self check in at a kiosk, print boarding passes and baggage tags, and check in their own luggage."
Breaking this down, the following picture emerges: Self-service check-in stations – essentially terminals (thin clients) – are set up at the airport and connected to the vMUSE system. Passengers can use these stations to check in for various airlines before departure and receive their boarding passes. In a post, Beaumont writes: "ARINC SelfServ vMUSE devices are used at airports worldwide for self-service check-in. They are connected to navAviNet, also known as the ARINC Ground Network, which is managed by Collins Aerospace, a company owned by RTX."
Passenger data, baggage data, biometric information, etc. are recorded on the systems, fed into the MUSE™ system (with a database), and made available to airlines. In a follow-up post, Beaumont adds: "The affected systems are located in the ARINC Multi-User System Environment (MUSE™), also known as ARINC vMUSE™ from Rockwell Collins. It's like a chain of corporate acquisitions!"
A look at Collins Aerospace's IT systems
It is exciting to learn, based on the information outlined above, how Collins Aerospace and its divisions are specifically positioned in terms of IT security, and what Kevin Beaumont discovered during brief checks of the company's IT systems.
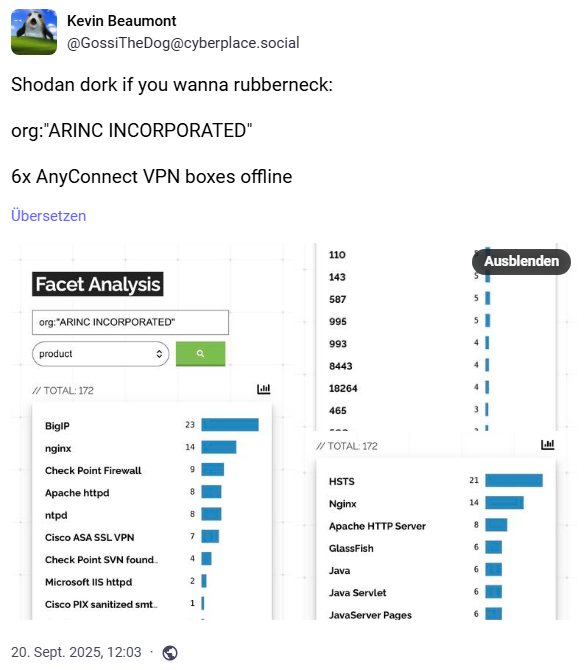
According to the above post, six Cisco AnyConnect VPN boxes are offline on the shodan.io platform. Well, cutting off VPN access is a good measure to take when you are under attack. This is because many ransomware groups use VPN access for their attacks. In June 2025, Cisco issued this security advisory about a problem with VPN access. If something was misconfigured, the operator would have had a problem – but that's just speculation.
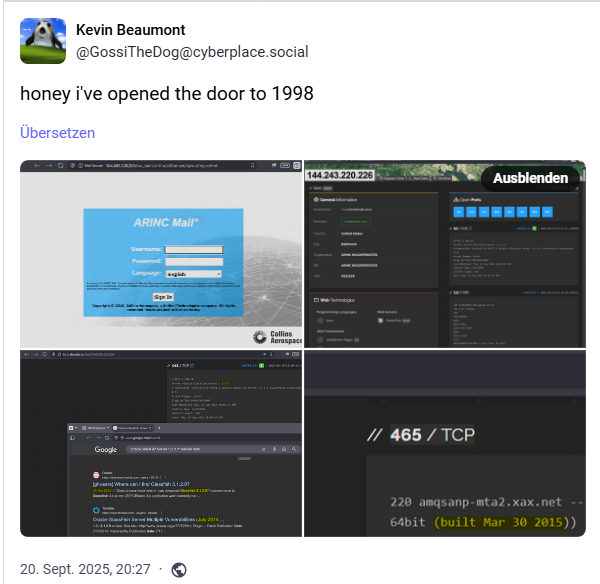
Beaumont then looked at the webmail pages of AIRINC (the operator of the check-in system at Collins Aerospace) and posted the following post.
Well, what can I say: The login page for their webmail system uses HTTP, which means that none of the login details entered are encrypted. But email is like a postcard anyway—anyone can see it, so what's the big deal?
What's a bit annoying is that the whole thing runs on JAVA with an Oracle GlassFish Server 3.1.2.9 (the current version is 7.0.25 from May 28, 2025). The screenshots above show that the system was last modified on June 23, 2016.
Beaumont also shows a screenshot of a web search where someone asks in 2014 where they can still find this old 3.1.2.9. And there is a hit from 2014 that confirms several vulnerabilities in the software. Another screenshot from Beaumont shows a build date of March 30, 2015 for the messaging server.
None of this is a "smoking gun" in the current cyber incident, as it is only the email system. However, the above outline paints a certain picture of how the conglomerate might be positioned in terms of IT security. While writing this blog post, I was informed that this old Oracle GlassFish Server 3.1.2.9 version will still be in use in small numbers in the aviation and defense industries in the US, France, etc. in 2025.
Reports about a ransomware attack
There are now reports on the internet that Collins Aerospace's ARINC vMUSE™ system has been infected with ransomware. airliners.de writes in this article: "The EU cybersecurity agency Enisa officially confirmed the incident as a ransomware attack on Monday."
Enisa confirmed this to Reuters without providing details or naming the group responsible. However, the ransomware group responsible appears to be known. The check-in and baggage handling systems of IT service provider Collins Aerospace at the above-mentioned airports are affected.
Another post by Kevin Beaumont is intriguing: "After ARINC restored domain controllers from backup, the threat actor got back in and started trashing more stuff. The whole thing is a mess; they probably want to pause, take a breath, and think about flushing out the attacker before rebuilding things."
To me, this implies that they are operating on a Windows infrastructure but do not know the attackers' point of entry. An attempt was made to restore a backup of the ARINC domain controller. However, the attackers still had access to the IT network, returned, and then began destroying more data.
According to my information, the current status is that even after four days, the systems are not fully online. And whether the attackers were able to extract data from the ARINC vMUSE™ system database is also currently unclear. But such a database containing millions of passenger records, including biometric characteristics, is likely to be a particularly attractive target.
There is another brief analysis that I found after the German edition of this blog post was published. If accurate, cybercriminals were already working on this issue at the end of 2024. CYFIRMA Research classifies Alixsec, Scattered Spider, and the ransomware group Rhysida as plausible actors.
But it seems, that Rhydia, or LokiLocker (which was mentioned in a comment in my German blog, isn't true. I just came across the post below on Mastodon where someone asks Kevin Beaumont a question about the ransomware used – and the post cited my German edition of this article.
Kevin Beaumont writes that a variant of the Hardbit ransomware was used. Details about Hartbit can be found here.
Arrest in the United Kingdom on September 24, 2025
There has been an arrest in connection with the ransomware attack on the service provider Collins Aerospace. This was reported by the BBC, citing the National Crime Agency (NCA) – the NCA statement is available here. A man in his forties was arrested in West Sussex "as part of an investigation into a cyber incident affecting Collins Aerospace," according to the official statement.
Final thoughts
Looking at the fragments I have put together above, I am not sure what to make of it all. Whether passenger handling is part of critical infrastructure and whether rebranded companies are entrusted with central functions is something that should really be addressed by the supervisory authorities for airports and airlines.
However, the incident shows once again how shaky the infrastructure for digitalization is in many industries. And politicians want to push ahead with this, true to the slogan "digitalization first, concerns second." I don't know whether to laugh or cry. But the incident fits into a pattern that has been repeating itself everywhere for years.