![]() [German]Once again it's the old story: Users drag extensions for Google's Chrome browser onto their system – and thus infect the devices with malware. More than 100,000 computers are said to have been infected by malicious chrome extensions.
[German]Once again it's the old story: Users drag extensions for Google's Chrome browser onto their system – and thus infect the devices with malware. More than 100,000 computers are said to have been infected by malicious chrome extensions.
The information can be found in the Radware blog, where last week the article Nigelthorn Malware Abuses Chrome Extensions to Cryptomine and Steal Data has been published. The zero-day malware threat was detected by the Radware malware protection service using machine learning algorithms at one of the customers on May 3, 2018.
This malware campaign spreads via links on Facebook and infects users by misusing a Google Chrome extension (the "Nigelify" application) that performs identity theft, crypto mining, click fraud and more.
Further research by Radware Threat Research Group has shown that this Nigelify group has been active since at least March 2018 and has infected more than 100,000 users in over 100 countries.
Facebook malware campaigns are not new. Examples of similar operations are facexworm and digimine, but this group seems to have gone undetected so far, thanks to the constantly changing applications and the use of an evasion mechanism to spread the malware.
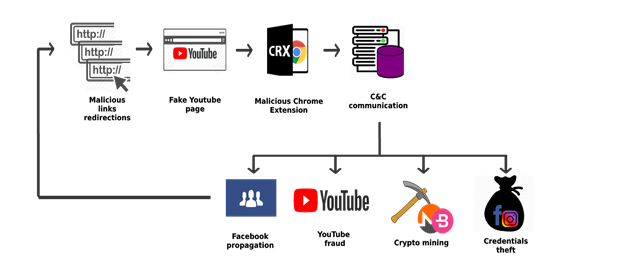
(Source: Radware)
The malware called "Nigelthorn" (named by Radware, since the original Nigelify application replaced images with "Nigel Thornberry") redirects the victim to a fake YouTube page and prompts the user to install a chrome extension to play the video.D
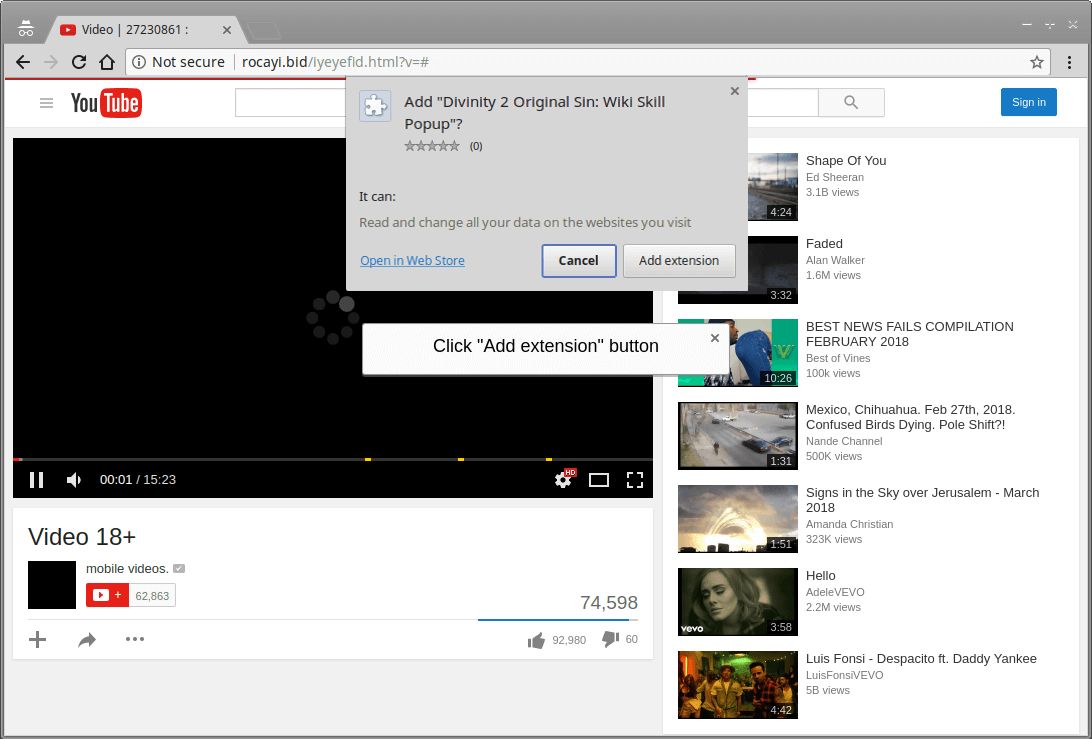
(Source: Radware)
As soon as the user clicks on "Add Extension", the malicious extension is installed and the computer is now part of the botnet. The malware requires the Google Chrome browser, and therefore runs on both Windows and Linux.
Apparently the malware makers have managed to smuggle the extension past Google's validation tools into the Chrome Store. The men behind the malware campaign made copies of legitimate extensions and injected a short, veiled malicious script to start the malware operation. The following screen lists some extensions of the malware.

(Source: Radware)
Once the extension is installed on the Chrome browser, a malicious JavaScript is executed. This downloads the original configuration from the command server and can then retrofit the malicious functions. Further details can be found within the Radware article. (via)



