![]() [German]Cyber criminals are trying to rebuild a router-based VPN botnet (VPNFilter) after the first variant was shut down by U.S. authorities. The attack is attributed to Russia's state-run APT28 group, which plans to attack Ukraine's IT infrastructure after the UEFA Champions League final on 26 May 2018.
[German]Cyber criminals are trying to rebuild a router-based VPN botnet (VPNFilter) after the first variant was shut down by U.S. authorities. The attack is attributed to Russia's state-run APT28 group, which plans to attack Ukraine's IT infrastructure after the UEFA Champions League final on 26 May 2018.
VPNFilter: What's the matter?
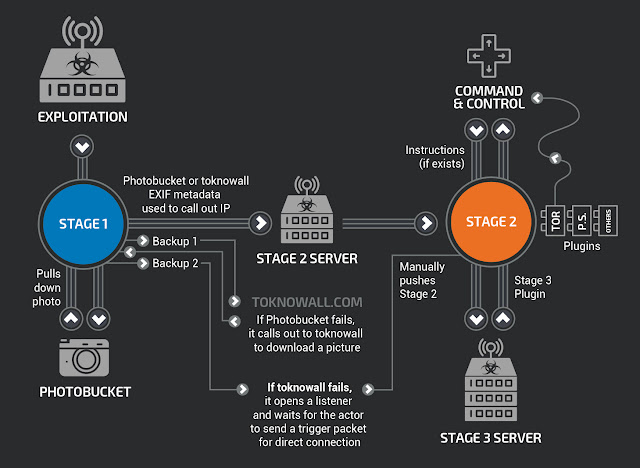
Security company Talos recently published information about a huge botnet called VPNFilter. This infects IoT devices (routers and NAS devices), 500 million devices were infected.
(Source: Talos)
This story has broadly covered within US media, after US authorities around the FBI have broken up the huge VPNfilter botnet. FBI was able, to bring the C&C servers under control. This step was necessary because important parts of the US infrastructure were hijacked by the botnet.
Afterwards, the FBI and the US Department of Justice called on users to restart their routers and NAS devices. The goal was, to remove the most part of the infection and get an overview, how many infected devices tries to reconnect to the C&C servers. I mentioned within my German blog post Sicherheitsinfos zum 31. Mai 2018, that a simple reboot doesn't cure the vulnerability of the infected device. User interaction is required (see my text below).
Which devices are affected?
However, there are no details as to which devices are affected. Talos has published the following list of devices, that are vulnerable (mostly due to missing firmware updates):
Linksys
- E1200
- E2500
- WRVS4400N
Mikrotik
- 1016
- 1036
- 1072
Netgear
- DGN2200
- R6400
- R7000
- R8000
- WNR1000
- WNR2000
Qnap
- TS251
- TS439 Pro
- sowie andere Qnap NAS-Geräte mit QTS-Software
TP-Link
- R600VPN
According to Talos, many infected devices are in Ukraine – Germany is in second place and the background for the request to restart is that the malware is partially deleted from the device. The remaining malware component recognizes this and tries to reload malware from the C&C servers. However, since these C&C servers are under the control of the FBI, they want to get an idea of how many devices are trying to reload malware.
Comeback of the VPNFilter Botnet
The cyber criminals behind the VPNFilter botnet are currently trying a comeback. Security researchers from JASK (Poland) and GreyNoise Intelligence reported on Friday that the same cyber criminals who built the first variant of the VPNFilter botnet are trying to build a new VPNFilter botnet. This is the result of observations made during the monitoring of the infrastructure.
At the moment, however, only routers in the Ukraine are targeted. All scans of the botnet look for microtic routers with open port 2000, which are used in Ukrainian networks. The security researchers believe this confirms the assumption that the state hackers of the Russian APT28 group are behind the attack. The approaches used in the exploits are only used by state actors.
About VPNFilter Malware
The VPNFilter malware that infects ITO devices is considered one of the most advanced types of IoT malware and probably contains three types of payloads.
- In a first step, the firmware of the IoT devices is attacked and a loader installed. This survives a restart of the device in question. By the way: This is only the second malware that has succeeded.
- In the second stage component resembles a Remote Access Trojan (RAT), which is then reloaded from C&C servers.
- The actual payloads of the third stage come as plug-ins for this RAT component. This allows the additional functionality to be added to the infected devices.
Security researchers who have analyzed VPNFilter malware say that this malware can delete local firmware, check local traffic, communicate through Tor, and search for ICS device traffic on the local network. Modbus is a communication protocol that is used in measurement and control components in industrial plants (I remember it from my industrial activity as an engineer over 25 years ago). Bleeping Computer has more details here.
What can/shall I do?
If you an administrator of routers or NAS devices, take care to update the firmware of these devices frequently. his is because devices with unpatched firmware are the cause of the infection. The Mikrotek routers targeted during the second wave of attacks have an old security vulnerability. Mikrotik closed the gap already in March 2017 (see Mikrotik-Advisory).
Wed Mar 28, 2018 3:44 pm
I has come to our attention that a rogue botnet is currently scanning random public IP addresses to find open Winbox (8291) and WWW (80) ports, to exploit a vulnerability in the RouterOS www server that was patched more than a year ago (in RouterOS v6.38.5, march 2017).
Since all RouterOS devices offer free upgrades with just two clicks, we urge you to upgrade your devices with the "Check for updates" button, if you haven't done so within the last year.Your devices are safe if the port 80 is firewalled, or if you have upgraded to v6.38.5 or newer. If you are using our home access point devices with default configuration, they are firewalled from the factory, and you should also be safe, but please upgrade never the less.
The vulnerability in question was fixed in March 2017:
Current release chain:What's new in 6.38.5 (2017-Mar-09 11:32):
!) www – fixed http server vulnerability;And also Bugfix release chain:
What's new in 6.37.5 (2017-Mar-09 11:54):
!) www – fixed http server vulnerability;Currently this botnet only spreads and scans. It doesn't do anything else, but we still suggest to change your password and upgrade your firewall, just in case. Recommendations about securing your router: https://wiki.mikrotik.com/wiki/Manual:S … our_Router
At Syslink this community post and this article contains hints, how to change the default administrator password.
At QNAP there is this Security Advisory for the NAS drives, which lists the affected firmware versions (QNAP NAS running QTS 4.2.6 build 20170628, 4.3.3 build 20170703, and earlier versions or using the default password for the administrator account). Workaround: Install the update QTS version 4.2.6 build 0729, 4.3.3 build 0727 or higher, run the QNAP malware removal tool and change the default password for the administrator. The following links refer to the pages of the device manufacturers, where further information is available.
Links:
VPNFilter malware (Mikrotik-Advisory)
VPNFilter Malware Update (Linksys Comunity)
VPNFilter Malware Security (T-Link)
Security Advisory for VPNFilter Malware
Mein Beitrag bei administrator.de
Similar articles:
Sicherheitsinfos zum 31. Mai 2018 (German)
Patch your MikroTik routers, there are attacks in the wild
QNAP fixes critical NAS bug that may causes data loss
Netgear router easily hackable – update your firmware



