 [German]Microsoft has just announced that it intends to activate Defender Tamper Protection under Windows 10 May 2019 Update (Version 1903). This is available for all Windows Defender ATP customers.
[German]Microsoft has just announced that it intends to activate Defender Tamper Protection under Windows 10 May 2019 Update (Version 1903). This is available for all Windows Defender ATP customers.
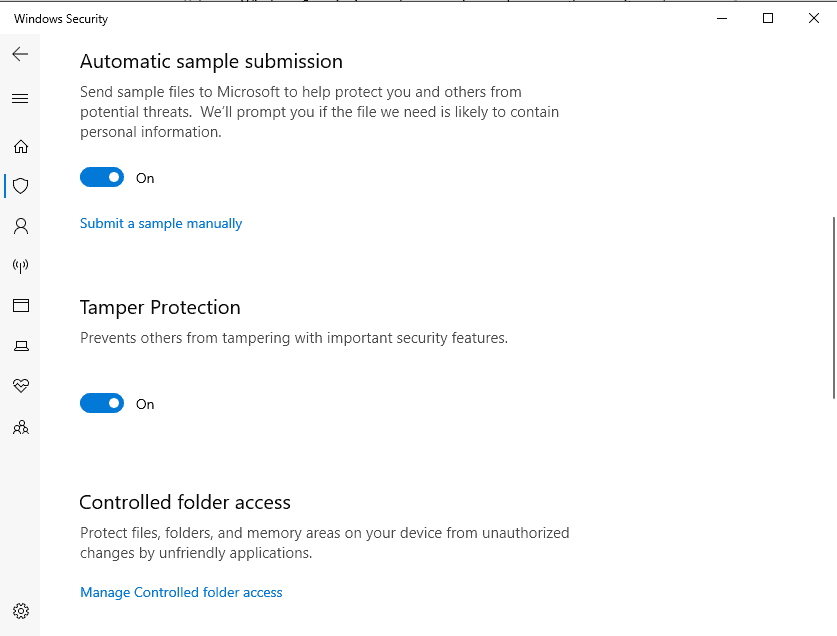
What is Defender Tamper Protection?
Microsoft wants to protect the Windows Defender included in Windows 10 against malware tampering. It should not be possible for a malicious program to switch off Windows Defender via registry entries, command prompt program commands, tools or group policies. Windows 10 May 2019 Update (Version 1903) introduced tamper protection, the so-called Windows Defender Tamper Protection (see this article on Preview Build 18305 in the Windows Blog).
(Activate Windows Defender Tamper Protection, Source: Ghacks.net)
I had reported in March 2019 in the blog post Windows 10 V1903 get Windows Defender Tamper-Protection about this feature. Microsoft published this support article in June 2019.
Previously, however, Windows Defender Tamper Protection was disabled by default. This functionality prevents administrators from using the DisableAntiSpyware Group Policy key to disable the Windows Defender Antivirus service. I pointed this out in the blog post Windows 10 V1903 get Windows Defender Tamper-Protection.
Tamper Protection should be enabled by default
Microsoft has probably now told Bleeping Computer that they want to enable Tamper Protection by default in Windows 10. In this article, colleague Lawrence Abrams writes:
Microsoft has announced today that the Windows 10 Tamper Protection security feature is now officially generally available for the Enterprise and consumers. Along with this announcement, Microsoft will be enabling this security feature on all Windows 10 devices by default.
According to this statement the manipulation protection should be activated for all Windows 10 users (but I am not sure whether this also affects Windows 10 V1809). It should take a few days until this activation is rolled out.
Microsoft has published this Techcommunity articles with details. According to my reading, Tamper Protection is only activated by default for Windows Defender ATP (i.e. the paid solution for companies).
Deactivate Defender in Intune or via GUI
If you want to disable this tamper protection, you can do so on consumer systems via the Windows Security Center in the Defender settings. In June 2019, Microsoft published this support article on the subject, which describes the necessary steps. Let's see, if there is acollateral damage with third-party antivirus solutions that disable Defender.
In the corporate environment, however, administrators can't use group policies such as the DisableAntiSpyware policy. Administrators can, of course, use the Windows Security Center to disable tamper protection in Defender. However, Microsoft points out in the article that central management of Tamper Protection for all Windows 10 devices is possible via Microsoft's Intune.



