![]() [German]Another short collection for administrators who use the Citrix ADC (Application Delivery Controller, formerly Netscaler). The CVE-2019-19781 vulnerability has been exploited. In addition, other vulnerabilities and backdoors have been discovered. As there are no firmware updates available yet (coming next week), those affected will have to go back in and take measures to harden against the vulnerabilities and perform additional testing to ensure that the instances are not infected.
[German]Another short collection for administrators who use the Citrix ADC (Application Delivery Controller, formerly Netscaler). The CVE-2019-19781 vulnerability has been exploited. In addition, other vulnerabilities and backdoors have been discovered. As there are no firmware updates available yet (coming next week), those affected will have to go back in and take measures to harden against the vulnerabilities and perform additional testing to ensure that the instances are not infected.
Advertising
German BSI warns again about CVE-2019-19781
I have warned about the CVE-2019-19781 vulnerability several times here in this blog (see my linked posts at the end of this article). In the article Vulnerability in Citrix Apps put companies at risk there is even a hint for a scanner for the vulnerability. So we may assume, that every admin has finally taken action.
CVE-2019-19781: Dem BSI liegen Meldungen vor, nach denen #Citrix-Systeme erfolgreich angegriffen werden. Wir rufen Anwender erneut dringend auf, die Workarounds von Citrix umgehend umzusetzen! #CitrixADC #CitrixGateway #Netscaler Mehr Infos hier: https://t.co/kHwPolBAgD
— BSI (@BSI_Bund) January 16, 2020
Apparently this is not the case, as German BSI feels compelled to issue a new warning in accordance with the above tweet. The German Federal Office for Information Security (BSI) has received numerous reports that Citrix systems have been successfully attacked. The BSI again urgently calls on administrators to immediately execute the mitigations provided by the manufacturer Citrix and not to wait for the security updates. Users who have not yet implemented the workaround measures should also check their Citrix systems directly connected to the Internet for a probable compromise.
Tip: Blog reader Christian Demmerer had pointed out in this German comment that the countermeasures recommended by Citrix to mitigate the vulnerability do not work with some older firmware versions. There is a bug and Christian describes a solution (update the old firmware).
New checks required!
German blog reader Puchte pointed out within this comment that an additional vulnerability in 2 HTTP headers has been discovered in Citrix NetScaler. Since first Proof of Concept (PoC) exploits were published, attacks on the Citrix ADC have been detected.
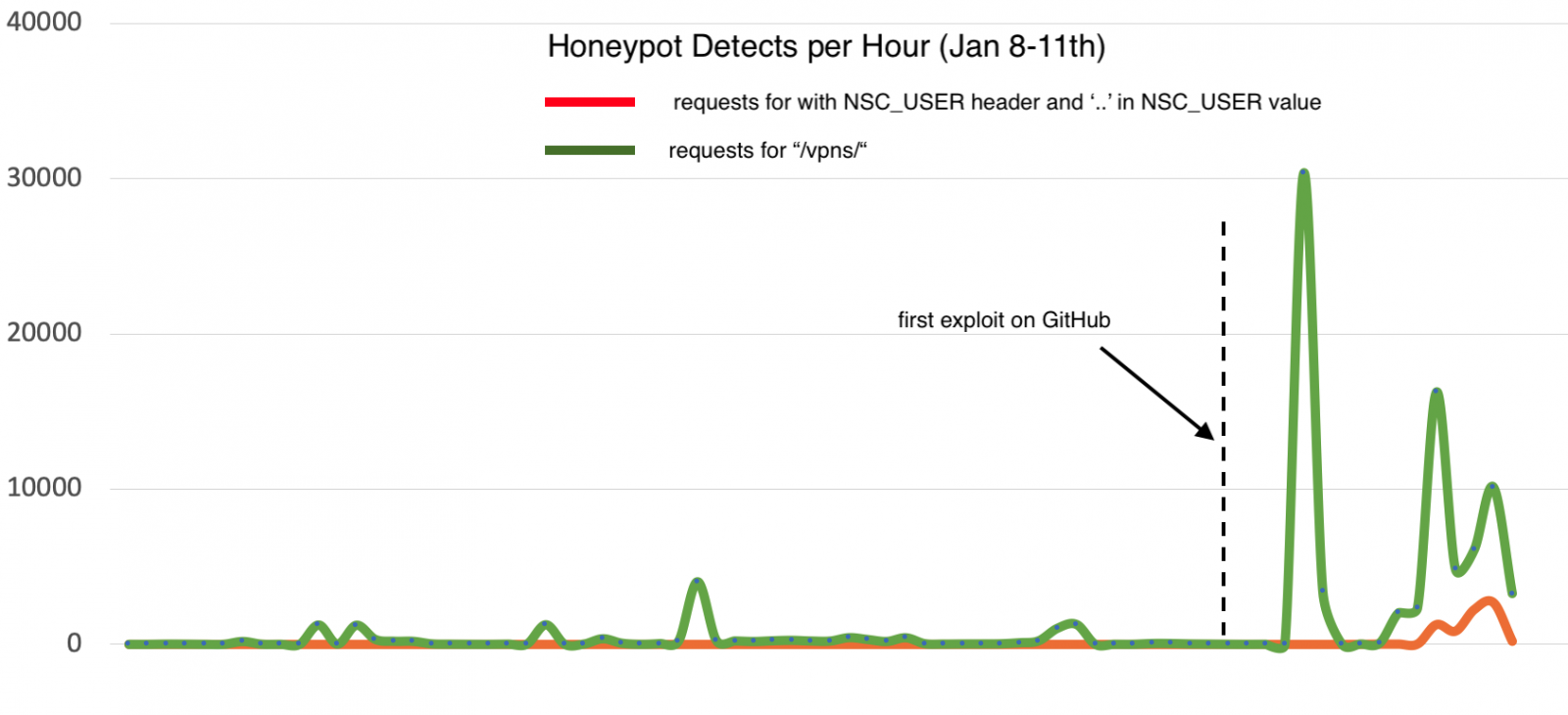
(Citrix ADC Honeypot Detects per Hour, Source: SANS)
Advertising
The above graph shows the increase in attack attempts recorded by a honeypot. During an analysis it was noticed that two known exploits leave files in the following directories:
/var/tmp/netscaler/portal/templates
/netscaler/portal/templates
But there is probably a bot that tries to delete the XML files. The SANS Institute describes the details here. In short: If you administrate Citrix ADC/Netscaler and have not used the workarounds suggested by Citrix yet, please take care of it.
In addition, all administrators of Citrix ADC/Netscaler should check if they are not already compromised and find the files described here. To detect vulnerable systems, the following command must be entered in the shell of the Citrix ADC/Netscaler:
curl https://host/vpn/../vpns/cfg/smb.conf --path-as-is
A response code of 200 means that the Citrix ADC/Netscaler is vulnerable. A 403 response code indicates that the workaround to mitigate the bug exists. A 404 response probably means that it is not a Citrix ADC or other vulnerable system. But read the notes in the following section
404 Exploit Not Found: FireEye found a Backdoor
During the night I came across a tweet from Christopher Glyer (Chief Security Architec at security provider FireEye).
We found an unexpected development with the Citrix Netscaler vulnerability. A seemingly "white knight" who left a backdoor to deploy additional malware while keeping out other criminals.
https://t.co/2kgcMGSosT— Christopher Glyer (@cglyer) January 17, 2020
Does the above test return the code 404 Exploit Not Found? Then it could be that the Citrix ADC/Netscaler has already been visited by a bot. After FireEye security experts analyzed dozens of successful attack attempts on Citrix ADCs that failed to implement Citrix mitigation measures to mitigate CVE-2019-19781, several groups of exploits came to light. One 'attacker' fell out of line because it used a previously unseen payload in the attack. He developed the code family NOTROBIN for this.
An attacker scans the Internet for vulnerable Citrix ADC/Netscaler instances. As soon as he gains access to a vulnerable NetScaler device, this actor cleans up known malware and uses NOTROBIN to block subsequent attack attempts!
At first you might think: Oh, a white hat hacker doing good. But it's not all as it seems, because the NOTROBIN payload sets up a backdoor. Anyone who knows a secret passphrase can access the Citrix ADC/Netscaler. FireEye believes that this actor could secretly collect access to Citrix ADC/Netscaler devices for a later campaign. Details on the attack and instructions on how to determine if the backdoor is present can be found in this FireEye blog post.
Similar articles
Vulnerability in Citrix Apps put companies at risk
PoC for Citrix ADC/Netscaler vulnerability CVE-2019-19781







