![]() [German]Security experts at Sophos have analyzed two RobinHood ransomware attacks and found that they use an outdated gigabyte driver to paralyze installed anti-virus software. The attack then launches for encryption.
[German]Security experts at Sophos have analyzed two RobinHood ransomware attacks and found that they use an outdated gigabyte driver to paralyze installed anti-virus software. The attack then launches for encryption.
The following tweet from SophosLabs refers to the original article, and Bleeping Computer has picked it up here.
NEW RESEARCH: Two different ransomware attacks borrow vulnerable driver to remove security software from the targeted computers just prior to performing the destructive file encryption portion of the attack.
Full story: https://t.co/6nvrryoGEG pic.twitter.com/tBrVXYBv6O
— SophosLabs (@SophosLabs) February 6, 2020
Old Gigabyte driver as vulnerability
A signed but now obsolete driver (part of a software package) from Taiwanese motherboard manufacturer Gigabyte contains a CVE-2018-19320 vulnerability that has been known since 2018.
The GDrv low-level driver in GIGABYTE APP Center v1.05.21 and earlier, AORUS GRAPHICS ENGINE before 1.57, XTREME GAMING ENGINE before 1.26, and OC GURU II v2.08 exposes ring0 memcpy-like functionality that could allow a local attacker to take complete control of the affected system.
The software package with the driver is outdated. But neither Microsoft nor Verisign, whose code-signing mechanism was used to digitally sign the driver, revoked the signature certificate, so the Authenticode signature is still valid.
Attack via the driver
In the observed cases, the cyber criminals behind the RobinHood ransomware used the Gigabyte driver as a lever to load a second, unsigned driver into Windows. This second driver then attempts to kill processes and files from endpoint security products (antivirus software). This allows the tamper protection of these packages to be bypassed and the ransomware is free to encrypt the files. The RobinHood ransomware message is then displayed.
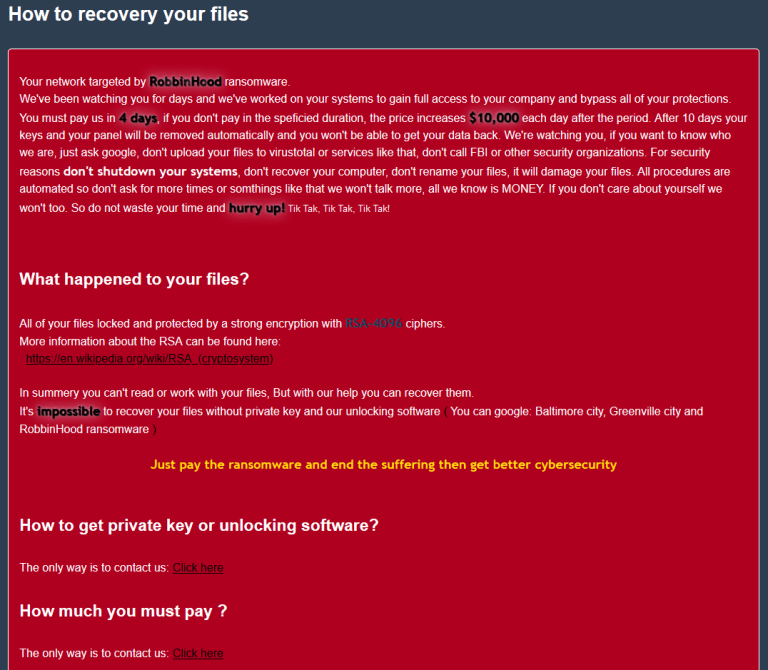
(RobinHood Ransomware notification, Source: Sophos)
Sophos security researchers write that this is the first time ransomware has been observed to deliver a third-party driver co-signed by Microsoft (but vulnerable) to patch the Windows kernel in memory, load its own unsigned malicious driver and remove security applications from the kernel. In both cases analyzed, the RobbinHood ransomware was found.
Windows virus/ransomware protection bypassed
Security researchers have recently seen how the RobbinHood ransomware family was able to encrypt files without the interference of endpoint protection software. The ransomware installer successfully infiltrates Windows 7, Windows 8 and Windows 10 kernel memory via the driver, and then a file called STEEL.EXE is run on the system.
This extracts a number of additional files to the C:\WINDOWS\TEMP folder. Then the unzipped files are started, which then install a driver with a vulnerability and kill the virus scanner processes. The details are given in this Sophos article. So if you are using old gigabyte hardware you should check if the driver is still installed on Windows.



