 [German]It looks like Microsoft also scans ZIP archives in its cloud storage for malicious content (and possibly other content) – even archives that are password-protected from viewing by the user. At least, that's what a post on Mastodon by security expert Andrew Brandt, principal security researcher at Sophos, suggests.
[German]It looks like Microsoft also scans ZIP archives in its cloud storage for malicious content (and possibly other content) – even archives that are password-protected from viewing by the user. At least, that's what a post on Mastodon by security expert Andrew Brandt, principal security researcher at Sophos, suggests.
It's known that US cloud providers scan the content stored on their online instances – I have reported on this several times in the blog (see links at the end of the article). Microsoft is no exception, the content of cloud instances like OneDrive is scanned for malicious files or "forbidden content". This can lead to very unpleasant situations, as I have shown in the article Microsoft's account suspensions and the OneDrive 'nude' photos.
So far, the argumentation in reader comments has been either "I put everything in ZIP archives and set a password before uploading it all to OneDrive" – or "this only applies to private cloud storage, not to companies". One or two observers have surely assumed that cloud providers like Microsoft also scan the contents of files on business cloud instances for malware. Of course, this does not only apply to OneDrive, but also to Google Drive or similar cloud storage.
SharePoint: Checking ZIP archives with password protection
Now, however, there is a hint that Microsoft has the ability to audit files stored in ZIP archives with password protection on SharePoint (and OneDrive as well as Teams). This was made known by Andrew Brandt, principal security researcher at Sophos, who shared his subsequent observation on Mastodon a few hours ago (neowin.net colleagues noticed it).
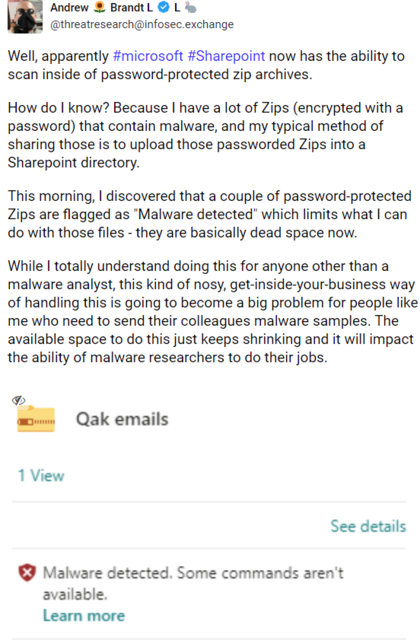
Brand writes that Microsoft probably has the ability to scan files stored on SharePoint in ZIP archives, even if they are password protected by the user.
Well, apparently #microsoft #Sharepoint now has the ability to scan inside of password-protected zip archives.
How do I know? Because I have a lot of Zips (encrypted with a password) that contain malware, and my typical method of sharing those is to upload those passworded Zips into a Sharepoint directory.
This morning, I discovered that a couple of password-protected Zips are flagged as "Malware detected" which limits what I can do with those files – they are basically dead space now.
While I totally understand doing this for anyone other than a malware analyst, this kind of nosy, get-inside-your-business way of handling this is going to become a big problem for people like me who need to send their colleagues malware samples. The available space to do this just keeps shrinking and it will impact the ability of malware researchers to do their jobs.
He became aware of this because in the morning he suddenly found a number of password-protected ZIP archives on his SharePoint drive marked with a "malware detected" flag. The security researcher writes that it's a problem for malware analysts because it's almost impossible to submit malware samples to colleagues anymore (the options keep shrinking).
This is what Microsoft writes
Microsoft has explained in its support pages what happens if infected files are uploaded to SharePoint. The support document What happens if an infected file is uploaded to SharePoint Online? states.
The Microsoft 365 virus detection engine scans files asynchronously (at some time after upload). If a file has not yet been scanned by the asynchronous virus detection process, and a user tries to download the file from the browser or from Teams, a scan on download is triggered by SharePoint before the download is allowed. All file types are not automatically scanned. Heuristics determine the files to scan. When a file is found to contain a virus, the file is flagged.
So the files are selected for scanning using heuristic methods after a user uploads them to SharePoint. If a hit is found, the virus detection engine used in Microsoft 365 flags them as "malware detected". This protection is included in all subscriptions that include SharePoint Online, OneDrive and Microsoft Teams.
However, users have the option by default to download files from SharePoint Online that are flagged as infected. Administrators, however, can change SharePoint's download behavior to prohibit the download of such files, as Microsoft explains here.
Safe Attachments für SharePoint, OneDrive and Microsoft Teams
There is also a Microsoft Support article How Safe Attachments for SharePoint, OneDrive, and Microsoft Teams works, that explains what happens when Safe Attachments is enabled for SharePoint, OneDrive, and Microsoft Teams.
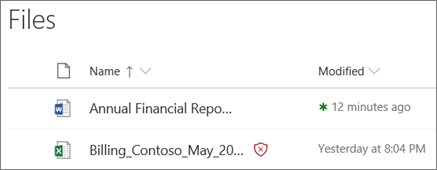
File marked as malware, source: Microsoft
A file identified as malicious is blocked through direct integration with file stores. The image above shows an example of a malicious file detected in a library. The file thus locked will still show up in the document library and in web, mobile or desktop applications. But the file cannot open, copy, move or share it. Users can still delete the locked file, however. It is not clear from the above post whether this option is set on the system the malware analyst used.
Scan password-protected ZIP archives
I think readers will now be burning to know how it is possible to scan password-protected ZIP archives. Is there a backdoor through which Microsoft can get to these files in the ZIP archive? On the question of how Microsoft can scan the contents of password-protected ZIP archives, security researcher Kevin Beaumont has commented on Mastodon..

As I understand the post, Microsoft uses password lists that are simply tried out on the ZIP archives. And the malware analyst used the password "infected" for his zip archives – a common password to exchange malware samples with collegues. Moreover, passwords would also be extracted from emails – which explains the access to the security researcher's ZIP archives (he shares the archives with colleagues and sends the passwords by mail).
Restrictions due to the cloud
The problem has been around for a while – I had picked up a tip from a US user in the English blog in the post Microsoft account lockout, an exemplary case. An affected user works as a malware analyst for a company and kept some malware samples and open source pen testing tools (some are typically part of the Kali Linux distribution) on OneDrive for his cyber training. The material was not password protected, and so his private OneDrive account was permanently locked. The man lost access to his entire online existence associated with the Microsoft account.
Discussion within my German blog
There is also a discussion on the topic in the comments here on my German blog. One user points out that problems can arise if companies stores files in the cloud, but these are then marked as malware. This will cause trouble, especially with files if they are subject to retention requirements but are suddenly inaccessible. It's a complex and difficult issue – because on the one hand, cloud providers are trying to do everything they can to find and eliminate infected material. But the cases show that the devil is in the details – and false positives (false positives) are not listed there yet. People are walking into a cloud trap here, so to speak, which is likely to hit us a few more times in the future.
The Degoo example
By the way, the issue is not limited to Microsoft alone. Google, Apple etc. also do these scans. There is a post in blog When the degoo bot closes your lifelong account … discussing a similar case. Degoo is a cloud service that advertises 'Life's best memories – AI based cloud storage that helps you rediscover your best photos.' My posts describe cases where users had bought a lifetime right to use online storage with Degoo. Meanwhile, there are more and more cases where a Degoo bot simply closes accounts for copyright infringement.

The blog post is working quite well as a honeypots; there are now 41 responses to the English blog post. For the German post there are 10 user feedbacks. By the way, the above post was initiated in 2020 by blog reader Markus, who emailed me about the suspension of his account at deego. The week I received two more mails from blog reader Markus, who tried to negotiate with deego. The following picture shows the notification for "copyright violation" including account blocking.
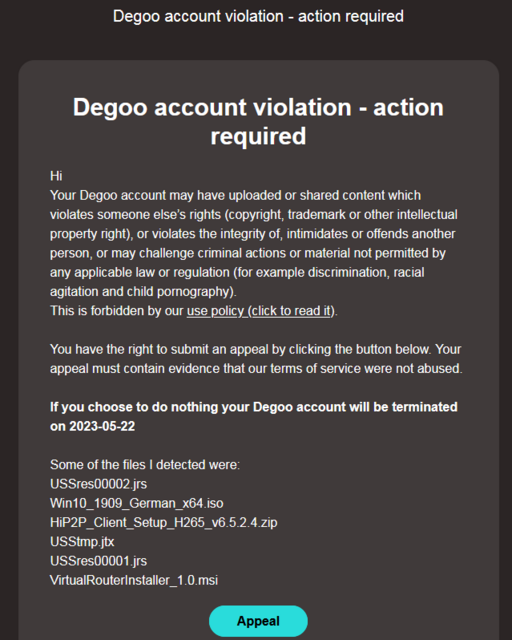
It can be seen that he had uploaded an ISO installation file of Windows 10 as well as various other setup files to the Degoo cloud storage. These were branded as copyright infringement, although this seems to be rather not the case. Markus then tried to contest the case, as suggested. To do so, he wrote to Degoo:
Hello,
the files mentioned are downloadable as setup files or the Windows ISO as download by the Microsoft MediaCreation tool which does not violate anything.
The other .jrs or .jtx seem to be located in a userprofile. I'm not aware that those files are violating copyrights.
If you can name me the backup and location I'll be happy to take a look at the issue at hand which seems to me to be some kind of false positive detection (at least that is my impression).
It is pretty harsh to threaten termination without any prior warning and the lack of information which backup is a possible problem nor the file-path to take action or the at least be able to verify if it could be a real violation.
I hope a human being takes a look at that and sees the reason in my arguments.
Markus K.
Markus assumed a false alarm and asked that someone with sense look at the case. The final answer from Degoo has just reached me from Markus:
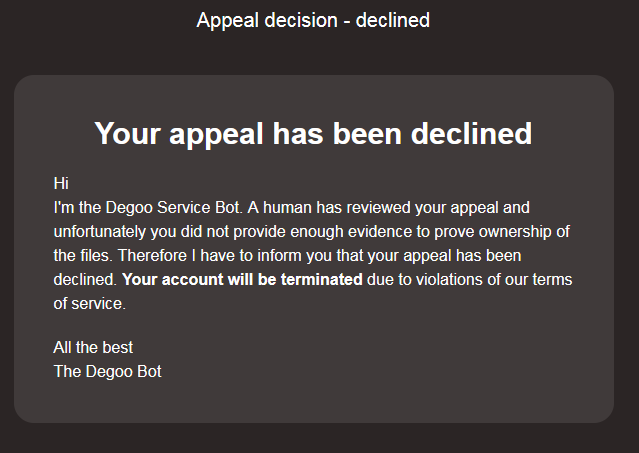
The case is rejected and the account is closed because of "violation of the terms and conditions". Markus says: "This cooperative way is to be emphasized in any case" and suspects that a bot wants to get rid of the 10TB lifetime members once a year. He had paid 100 euros for a lifetime membership. I can only conclud: Happy Cloud-Live, you want adventure, just try it out.
Similar articles:
Microsoft account lockout, an exemplary case
Microsoft's account suspensions and the OneDrive 'nude' photos
Outlook.com 'account suspensions' due to unusual sign-in activities – is Microsoft's AI running amok, or are accounts compromised?
Google account blocked and police action because of toddler photos for the doctor



