[German]Progress Software, which has been hit hard by the MoveIT vulnerability, is facing the next trouble. There are further serious vulnerabilities in its WS_FTP Server software that could already being exploited in the wild. The products must be immediately provided with the emergency patch to secure them.
[German]Progress Software, which has been hit hard by the MoveIT vulnerability, is facing the next trouble. There are further serious vulnerabilities in its WS_FTP Server software that could already being exploited in the wild. The products must be immediately provided with the emergency patch to secure them.
Advertising
Vendor Progress Software had to report and patch several vulnerabilities in its MoveIT Transfer software in June/July 2023. The vulnerabilities were exploited by the Clop ransomware group to steal data from organizations, government agencies, companies. The victims were blackmailed with the threat that the sensitive data would be made public and were supposed to pay ransom. I assume that there are over a thousand victims and the ransomware gang extorted many millions of euros in ransom. The links at the end of the article deal with MoveIT transfer vulnerabilities.
Vulnerabilities in WS_FTP Server
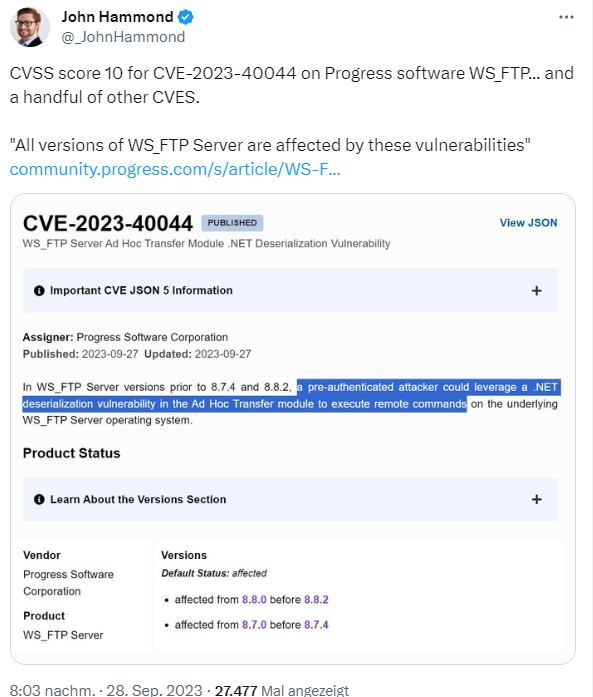
WS_FTP Server (WinSock File Transfer Protocol) is a software package for secure file transfer offered by Ipswitch, Inc (now Progress Software). Yesterday a security advisory was published by Progress Software pointing out serious security vulnerabilities in WS_FTP Server. John Hammond points out the security advisory WS_FTP Server Critical Vulnerability – (September 2023) from Progress Software in their community in the following tweet.
The WS_FTP team has been notified of recently discovered vulnerabilities in the WS_FTP Server Ad hoc Transfer Module and the WS_FTP Server Manager interface. All versions of WS_FTP Server are affected by these vulnerabilities. Critical vulnerability CVE-2023-40044 has a CVSS score of 10 (cannot go higher) and affects WS_FTP Server versions prior to 8.7.4 and 8.8.2. A pre-authenticated attacker can exploit a .NET deserialization vulnerability in the Ad Hoc Transfer Module to execute remote commands on the underlying WS_FTP Server operating system.
Critical vulnerability CVE-2023-42657 has a CVSS score of 9.9, affecting WS_FTP Server versions prior to 8.7.4 and 8.8.2. The vulnerability is related to directory bypass. An attacker could exploit this vulnerability to perform file operations (delete, rename, rmdir, mkdir) on files and folders outside the authorized WS_FTP folder path. Attackers could also break out of the context of the WS_FTP server file structure and perform the same operations (delete, rename, rmdir, mkdir) on file and folder locations on the underlying operating system.
Advertising
The Record has provided some more details about the vulnerabilities in this article. There are a number of other vulnerabilities in WS_FTP that are described in this article. Progress Software writes that the vulnerabilities have been fixed and that they are providing version-specific hotfixes to customers to fix the bugs. So far there are no known cases where the vulnerabilities are exploited.
Similar articles:
Warning: MOVEit vulnerability is abused in attacks, data extradicted
Lace Tempest/Clop ransomware gang exploits MOVEit vulnerability CVE-2023-34362
MOVEit Transfer: New vulnerability; patch urgently!
MOVEit Transfer: New security advisory and update (July 6, 2023)
Data leak at German Postbank and Deutsche Bank (blame MOVEit?)
Advertising