[German]Europol and other law enforcement authorities like German BKA, the FBI and other international police agencies have seized the RagnarLocker ransomware gang's website, which was used to negotiate ransom payments with victims. It is hoped that this will cut off the ransomware group from its funding opportunity. Currently, there are no official announcements yet – they are expected to be released later today.
[German]Europol and other law enforcement authorities like German BKA, the FBI and other international police agencies have seized the RagnarLocker ransomware gang's website, which was used to negotiate ransom payments with victims. It is hoped that this will cut off the ransomware group from its funding opportunity. Currently, there are no official announcements yet – they are expected to be released later today.
Advertising
Website seized
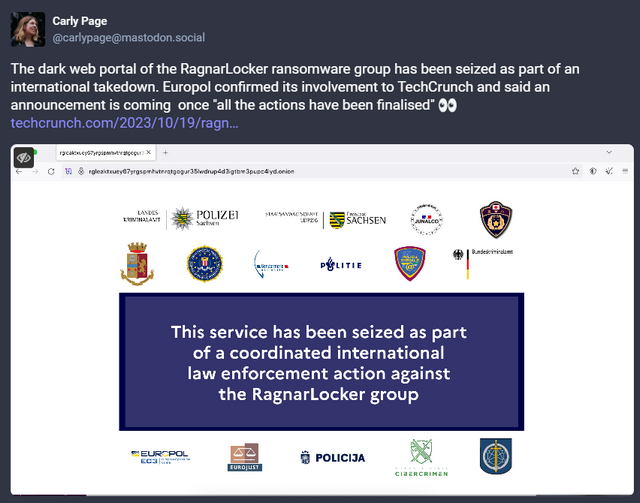
I came across the facts of the matter via the following post on Mastodon, among others. It says that the dark web portal of the ransomware group RagnarLocker was seized as part of an international raid.
The Mastodon post links to an articles from Techcrunch, where it says that Europol confirmed its involvement in the seizure operation to TechCrunch. An official announcement will be made once "all measures have been completed," it said.
The RagnarLocker ransomware group's website on the dark web now states that "this service was seized as part of a coordinated international law enforcement operation against the RagnarLocker group". According to the seizure notice, the operation involved law enforcement agencies from the United States, the European Union and Japan.
Currently, the extent of the operation is not yet known. It is also unclear whether the RagnarLocker ransomware group's infrastructure was also seized, whether any arrests were made, or whether any stolen funds were recovered.
Advertising
Europol spokeswoman Claire Georges confirmed to TechCrunch that the agency is involved in "ongoing operations against this ransomware group." The spokeswoman said Europol plans to announce the takedown on Friday "when all measures have been completed." An unnamed spokesperson for the Italian state police also confirmed that details of the operation would be made public on Friday. An unnamed FBI spokesman declined to comment.
Who is RagnarLocker?
Bleeping Computer colleagues have gathered some information about RagnarLocker here. RagnarLocker is one of the longest-running ransomware groups that started its activity in late 2019. The group targets businesses and tries to penetrate their corporate networks, then laterally spreads to other devices. During this phase, data and are transferred to the group's CC servers. Then, the files of the infected machines are encrypted.
The encrypted files and stolen data were then used by the group as leverage to extort victims and force them to pay ransom. The ransom was supposed to buy the ability to decrypt the files. In addition, this ransom payment was supposed to prevent the publication of data.
The Register writes here, that a known tactic of RagnarLocker was to prevent victims from contacting law enforcement in their own country. This fact makes the recent raid special, according to Jake Moore, Global Cybersecurity Advisor at ESET.
"Any raid by Europol is significant and impressive, but this one seems to have a special cachet because of its Russian origin and reflects the power of trying to suppress law enforcement help," Moore told The Register. He adds, "In the past, RagnarLocker has warned its victims not to contact the police or FBI about the ransomware or they would face having their data made public. Therefore, this action will be an additional blow to the ransomware group, which obviously has a beef with the authorities."