[German]The vulnerability in Progress Software's Managed File Transfer (MFT) solution MOVEit, which was disclosed in May 2023, has also affected CCleaner customers of the vendor Priform (bought by AVAST and owned by Gen Digital). Piriform has just admitted to a data leak due to the MOVEit vulnerability.
[German]The vulnerability in Progress Software's Managed File Transfer (MFT) solution MOVEit, which was disclosed in May 2023, has also affected CCleaner customers of the vendor Priform (bought by AVAST and owned by Gen Digital). Piriform has just admitted to a data leak due to the MOVEit vulnerability.
Piriform CCleaner-Kundendaten erbeutet
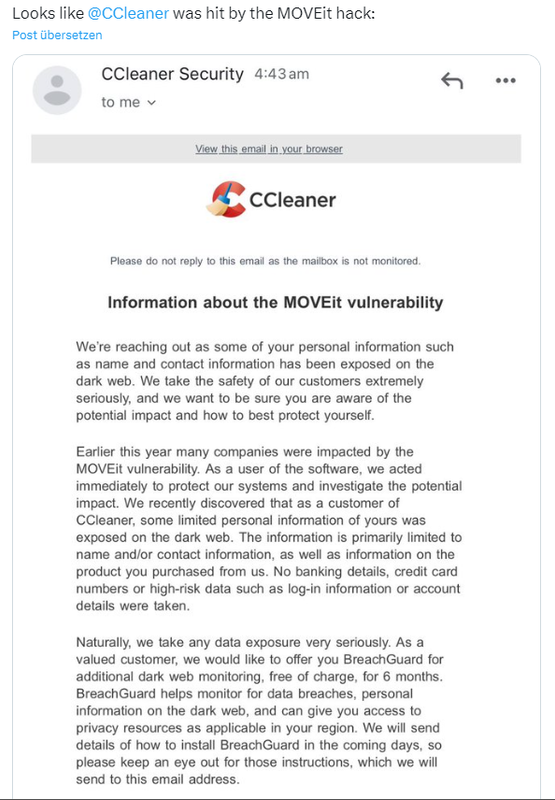
Pirifom, the provider of the "cleaning" software CCleaner, has gone public with a statement disclosing that customer data was leaked via the MOVEit vulnerability. Troy Hunt referred to this statement in the following tweet.
There is an admission that customer data of CCleaner users, such as name, contact information and information about the purchased product, was siphoned off via the MOVEit vulnerability. Piriform stresses that no banking or account login information was leaked. From CCleaner, affected customers are being offered a six-month free subscription to the Breachguard security tool. This is to enable monitoring for suspicious activity related to the stolen data.
What is MOVEit?
MOVEit is a Managed File Transfer (MFT) software that enables transfer of files between different computers. The software is developed by Ipswitch, a subsidiary of the US company Progress Software Corporation. MOVEit is often used in companies to exchange files between customers or business partners via the Internet. Uploads are supported via the SFTP, SCP and HTTP protocols to transfer the files securely.
The vulnerability CVE-2023-34362
MOVEit vulnerability CVE-2023-34362 became known at the end of May 2023 (see Warning: MOVEit vulnerability is abused in attacks, data extradicted), and it turned out that this vulnerability was specifically exploited by the Lace Tempest/Clop ransomware gang (suspected as early as 2021) (see Lace Tempest/Clop ransomware gang exploits MOVEit vulnerability CVE-2023-34362).
Since then it became known, that several hundreds of thousands of victims were extorted by Clop, because they stole sensitive (user) data from the victims. Clop threatened to publish and posted the data of many victims on their websites.
Similar articles:
Warning: MOVEit vulnerability is abused in attacks, data extradicted
Lace Tempest/Clop ransomware gang exploits MOVEit vulnerability CVE-2023-34362
MOVEit Transfer: New vulnerability; patch urgently!
MOVEit Transfer: New security advisory and update (July 6, 2023)
Data leak at German Postbank and Deutsche Bank (blame MOVEit?)
MoveIT vendor Progress Software reports serious vulnerabilities in WS_FTP Server