 [German]A small addendum from yesterday – the US FBI, together with other law enforcement agencies, has paralyzed the operations of the ALPHV/Blackcat ransomware group, according to the US Department of Justice. There had already been speculation for days that something was up. The FBI has also created a decryption tool, which is now being made available to victims to restore encrypted files.
[German]A small addendum from yesterday – the US FBI, together with other law enforcement agencies, has paralyzed the operations of the ALPHV/Blackcat ransomware group, according to the US Department of Justice. There had already been speculation for days that something was up. The FBI has also created a decryption tool, which is now being made available to victims to restore encrypted files.
Advertising
The ALPHV/Blackcat ransomware group
ALPHV/Blackcat is a ransomware group that has been active since the end of 2021. The group has written its malware in Rust and is therefore able to attack both Windows and Linux systems. The ALPHV group markets its ransomware-as-a-service in cybercrime forums and operates an affiliate program.
In addition to encrypting the files on the infected systems, data is also extracted beforehand. The group is known to pass on stolen data if its ransom demands are not met and operates several dark web blogs for this purpose. There are several posts here on the blog about the ransomware group's activities (see links at the end of the article). The attack on the Motel One hotel chain is the work of ALPHV/Blackcat. A few days ago, I reported (BlackCat verschlüsselt US-Unternehmen Henry Schein zum dritten Mal) that Blackcat boasted that it had attacked the US company Henry Schein for the third time within weeks and encrypted its systems.
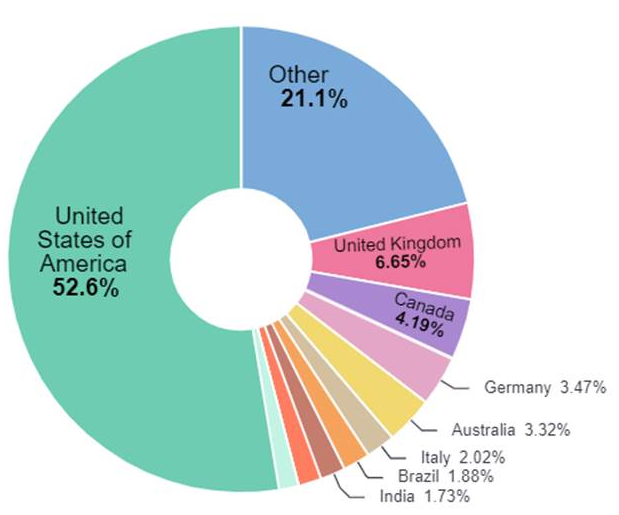
ALPHV/Blackcat ransomware victims by country; source: Check Point
Security vendor Check Point states that the group has successfully attacked and extorted around 700 publicly known victims worldwide in the last two years. I received the above chart from Check Point, which shows the victims by country – over half of the victims are in the USA. But Germany is also represented in the list with 3.74% of cases.
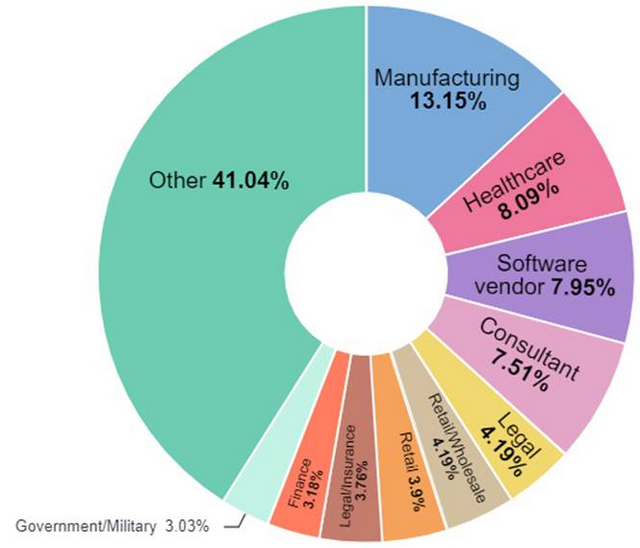
ALPHV/Blackcat ransomware victims by industry; source: Check Point
Advertising
The chart above, which I also received from Check Point, shows the breakdown of victims by industry. The most commonly extorted industries were manufacturing and healthcare. Members of the group also heavily targeted the sensitive supply chain of companies such as software vendors and consulting firms. More than half of the victims were U.S. companies, and just recently the group claimed to have infiltrated several entities such as Florida State University, Fidelity National Financial, the MGM Grand chain and others. Check Point ranks ALPHV/Blackcat as one of the top 3 most sophisticated and prolific Eastern European ransomware groups.
Blackcat (old) sites down for days
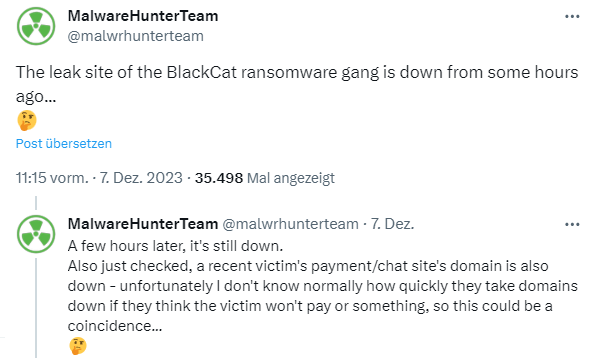
It was only a matter of time before the ransomware group's operations would be disrupted by Western law enforcement. On December 8, 2023, I had already seen this article from my colleagues at Bleeping Computer. The message was that the BlackCat ransomware group's leak page had been down since December 7, 2023.
The article was based on the above tweets from the MalwareHunter team, who had noticed that the leak pages in question had been offline for hours. The site where victims could pay their ransom was also offline. The speculation was that law enforcement had seized the ransomware gang's infrastructure (this tweet confirms this).
I didn't pick up on this at the time because I assumed an official FBI announcement would come out a day or two later – which it didn't. The administrator of ALPHV told Bleeping Computer that they would be back online in a few hours. The operator did not give a reason for the outage.
Law enforcement officials confirmed Operation
It took until December 19, 2023 for the US Department of Justice to confirm in an announcement that the widespread ALPHV/Blackcat ransomware variant had been paralyzed. Law enforcement officials have spent 18 months investigating ALPHV/Blackcat, which has become the second most prevalent ransomware-as-a-service variant in the world. The group has extorted hundreds of millions of US dollars in ransom from more than 1,000 victims. Due to the global scale of these crimes, several foreign law enforcement agencies are conducting parallel investigations.
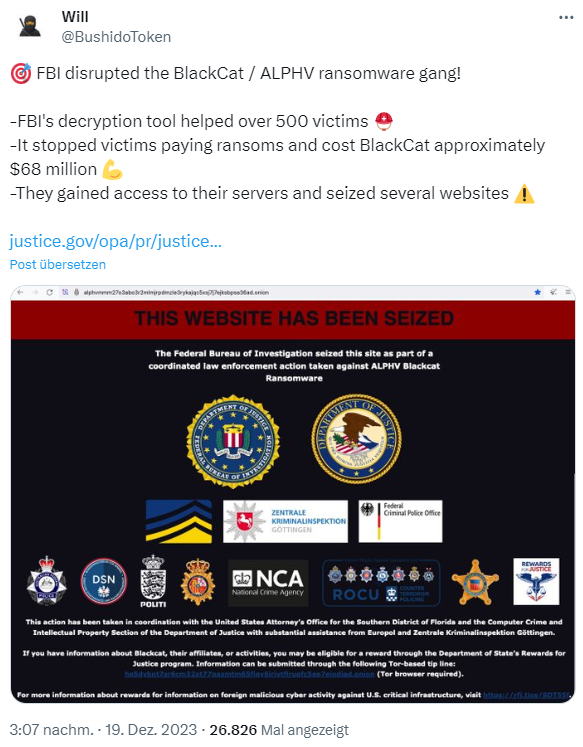
In December 2023, a search warrant from a court in South Florida (warrant available here) led to the FBI being able to seize several websites operated by the group. This explains why the leak page and the page for payments are down. As part of the investigation, the FBI also gained insight into the computer network of the Blackcat ransomware group and was even able to develop a decryption tool. "By taking down the BlackCat ransomware group, the Department of Justice has once again hacked the hackers," said Assistant Attorney General Lisa O. Monaco.
There appears to have been worldwide cooperation between law enforcement authorities. The Department of Justice explicitly acknowledges the important cooperation with the German Federal Criminal Police Office and the Central Criminal Investigation Department in Göttingen, as well as the Danish Special Crime Unit and Europol.
The U.S. Secret Service and the U.S. Attorney's Office for the Eastern District of Virginia provided significant assistance, it said, as did the Department of Justice's Office of International Affairs and the Cyber Operations International Liaison.In addition, the Australian Federal Police, the UK National Crime Agency and the Eastern Region Special Operations Unit, the Spanish Policia Nacional, the Swiss Cantonal Police Thurgau and the Austrian Directorate of State Security and Intelligence provided significant assistance and support.
FBI provides a decryptor
The FBI then succeeded in developing a decryption tool for various Blackcat ransomware variants. This tool enables FBI field offices in the United States, as well as law enforcement partners around the world, to offer system recovery to over 500 affected victims. To date, the FBI has worked with dozens of victims in the United States and internationally to implement this solution and save several victims from ransom demands totaling approximately $68 million, according to the release. Additional victims of the ransomware group are encouraged to come forward.
An assessment of the situation
The announcements from US law enforcement make rather bombastic reading, but there are few details. Our colleagues at Bleeping Computer report that the FBI managed to gain access to the ALPHV/BlackCat ransomware network via an individual, log in and become an affiliate. The person in question was given the credentials for the non-public backend panel of the affiliates. This panel is used to manage extortion campaigns and ransom negotiations.
The FBI managed to obtain a search warrant from a court so that the operation could be carried out. This made it possible to analyze the procedures of the ALPHV panel. For example, the victims, the ransom demanded, any reduced ransom demands, the expiration date of the ultimatum, the cryptocurrency addresses, the cryptocurrency transactions, the type of computer system compromised, the note on the ransom demand to the victim, chats with the victim and much more are displayed there.
This was the jackpot, so to speak, because the FBI was able to obtain the private decryption keys used in the attacks. This was used to create a decryption program that enabled over 400 victims to recover their files free of charge. However, it should be noted that the data has been removed from the victims' systems and is in the hands of the cybercriminals. The data could therefore be published at any time.
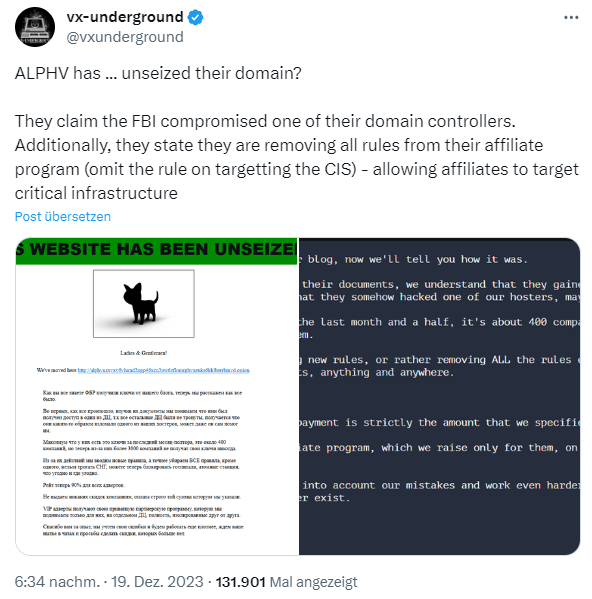
The seizure is just a staging post as the cat-and-mouse game between law enforcement and the ransomware gang gets underway. The decryptor tool can probably only decrypt the encrypted files of the last 400 victims, as can be seen from the above tweet. However, the ransomware group is said to have succeeded in bringing back the online presences after the FBI compromised one of the ransomware gang's domain controllers.
Now, the BlackCat group has removed all rules prohibiting attacks on certain objects such as critical infrastructure from its partner program (only the rule prohibiting attacks on the GRU still seems to exist). This would allow the "partners" of the ALPHV/BlackCat gang to attack critical infrastructures as well.
The status is that the FBI and other law enforcement agencies have managed to disrupt the ransomware group's operation. There will also be some victims who will get their encrypted files back using the decryption tool. However, this does not really solve the following problems. The victims' data has been extracted and could be published by ALPHV/BlackCat at any time. The security issues through which the attackers penetrated may still exist or the backdoors for access may still be in place. And the entire infrastructure of the ransomware gang does not really seem to have been dismantled, nor have any arrests been made. I read, that the group has now a new site online.
I therefore assume that the group will soon strike again. The Register reports here that the group was able to get its website back up and running and listed more victims in the hours before the law enforcement agency published the above report. And if this group does not attack the systems, other ransomware groups will continue. As long as IT infrastructures around the world are so poorly secured and software is in an absolutely disastrous state of security, not much will change – the action against ALPHV/BlackCat is a stage victory, nothing more and nothing less.
Similar articles:
When ransomware groups (AlphV) snitch on victims to the SEC
Cyberattack on Oiltanking: Black Cat ransomware group responsibe, also for Colonial Pipeline Hack
Ransomware group ALPHV (Blackcat) with new extortion techniques (searchable database)
Pipline and electricity operator Creos Luxembourg victim of BlackCat ransomware
One of Michigan's largest healthcare providers fell victim to ALPHV ransomware gang








this cat needs to be put in a burlap sack with bricks and tossed into the moskva river.