[German]After Microsoft, Hewlett Packard Enterprise (HPE) has also fallen victim to the Russian hacker group Midnight Blizzard. This is according to a notification from the company to the US SECURITIES AND EXCHANGE COMMISSION (SEC). As with Microsoft, the attackers probably had access to the company's email system (Microsoft 365). The attackers were then able to look around this system at HPE for months.
[German]After Microsoft, Hewlett Packard Enterprise (HPE) has also fallen victim to the Russian hacker group Midnight Blizzard. This is according to a notification from the company to the US SECURITIES AND EXCHANGE COMMISSION (SEC). As with Microsoft, the attackers probably had access to the company's email system (Microsoft 365). The attackers were then able to look around this system at HPE for months.
Who is HPE?
Hewlett Packard Enterprise is an American information technology company that was created through the spin-off of the enterprise customer business of the Hewlett-Packard Company. Among other things, it offers servers for corporate customers.
Information on the HPE hack
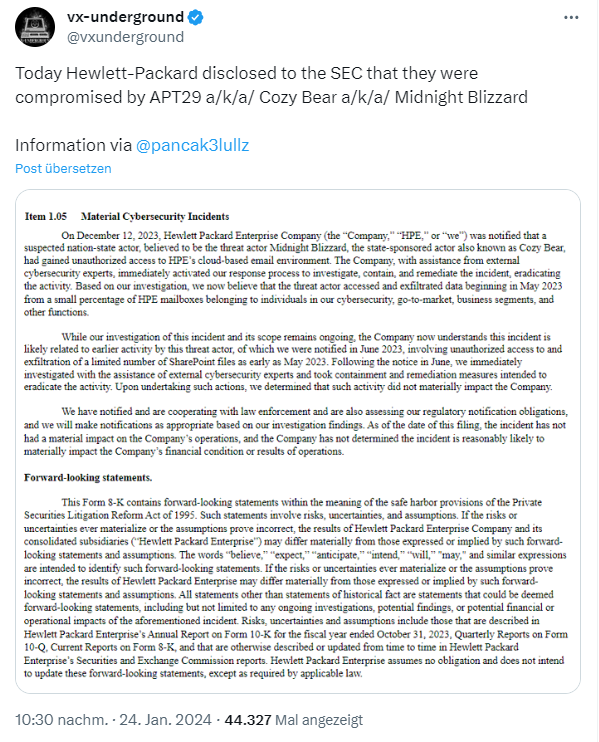
They have been the victim of a cyber attack. Thomas pointed me to the following tweet from vxunderground on the subject (thanks for that). The tweet contains a screenshot of the notification to the SEC.
Hewlett Packard Enterprise (HPE) was notified on December 12, 2023 that a suspected nation-state actor, believed to be the threat actor Midnight Blizzard (also known as Cozy Bear), had gained unauthorized access to HPE's cloud-based email environment. Bleeping Computer says, that the cloud-based email environment is Microsoft Office 365, but the SEC filing don't has this detail.
The company, with the assistance of external cybersecurity experts, immediately activated its internal incident response process to investigate, contain and remediate the incident and subsequently remediate the activity. Based on our investigation, officials now believe that the threat actor accessed and exfiltrated data in a small percentage of HPE mailboxes beginning in May 2023. Those affected include individuals from cybersecurity, go-to-market, business segments and other functions.
The investigation into this incident and its scope is still ongoing. HPE now believes that this incident is likely related to previous activities by this threat actor, which the company was informed about in June 2023. At that time, in May 2023, attackers were able to extract a limited number of files during unauthorized access to SharePoint servers.
Following the notification in June 2023, investigations were immediately conducted with the assistance of external cybersecurity experts and containment and remediation measures were taken to eliminate the activity. After these measures were taken, the specialists determined that these activities had no material impact on the company.
HPE has notified and is cooperating with law enforcement authorities. In addition, HPE officials are reviewing regulatory reporting requirements and will make appropriate notifications based on further investigation results.
Remember the Microsoft case
This immediately set alarm bells ringing, because this plot is familiar to me from the blog post Microsoft hacked by Russian Midnight Blizzard; emails exfiltrated since Nov. 2023. Microsoft became aware of this hack on January 12, 2024, and the hackers have been in the system since November 2023, it says.
vxunderground points out in a tweet that Microsoft announced on January 12, 2024 that it had been compromised by a hack by APT29 aka Midnight Blizzard since November 2023. There, the group had gained access to the emails of company management, cybersecurity personnel and the legal department. The attackers are said to have been in the system since November 2023.
On January 24, 2024, Hewlett-Packard Enterprise announced that the company had been compromised by APT29 aka Midnight Blizzard and that the group had access to emails from cybersecurity personnel, go-to-market, and other business units. The attackers had been on the system since May 2023. Could this be a coincidence?
Similar articles:
China hacker (Storm-0558) accessed Outlook accounts in Microsoft's cloud
Stolen AAD key allowed (Storm-0558) wide-ranging access to Microsoft cloud services
Microsoft hacked by Russian Midnight Blizzard; emails exfiltrated since Nov. 2023