[German]It has been known for a few hours that law enforcement officers have seized some of the Lockbit ransomware gang's infrastructure servers in an internationally coordinated operation (FBI, Europool, etc.) and taken control of them. Official information on "Operation Cronos" is not yet available, and it looks as if there are still servants of the group online. Here is a first overview. Addendum 1: The press releases from law enforcement are online: Two suspects have been arrested, 200 cryptocurrency accounts have been frozen, and free decryption tools for lockbit victims are provided on No More Ransome. Addendum 2: It's not over yet.
[German]It has been known for a few hours that law enforcement officers have seized some of the Lockbit ransomware gang's infrastructure servers in an internationally coordinated operation (FBI, Europool, etc.) and taken control of them. Official information on "Operation Cronos" is not yet available, and it looks as if there are still servants of the group online. Here is a first overview. Addendum 1: The press releases from law enforcement are online: Two suspects have been arrested, 200 cryptocurrency accounts have been frozen, and free decryption tools for lockbit victims are provided on No More Ransome. Addendum 2: It's not over yet.
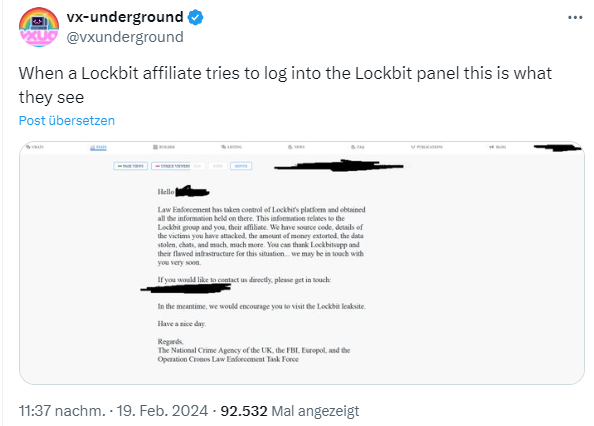
In the following Tweet, vx-underground shows the seizure message a Lockbit affiliate sees when trying to log in to the Lockbit panel. The "visitor" is informed that law enforcement has seized the platform and taken over all the information stored there.
In another tweet vx-underground writes, that administrators of the Lockbit ransomware group have confirmed that the group's websites have been seized. Some of the group's websites appear to be displaying the seizure message shown below.

The message reads: : "The site is now under the control of law enforcement. This site is now under the control of The National Crime Agency of the UK, Working in close cooperation with the FBI and the international law enforcement task force, Operation Cronos."
However, security researcher Kevin Beaumont writes in this Mastodon post that three LockBit services are still online. One service is still offering stolen data. If the law enforcement authorities have taken control of the infrastructure, these services will definitely have to be shut down. But the law enforcement action is still ongoing – there is no press release yet from the NCA, FBI and Europol as well as German agencies (due today at 12:30 Central European time, as Bleeping Computer writes here).
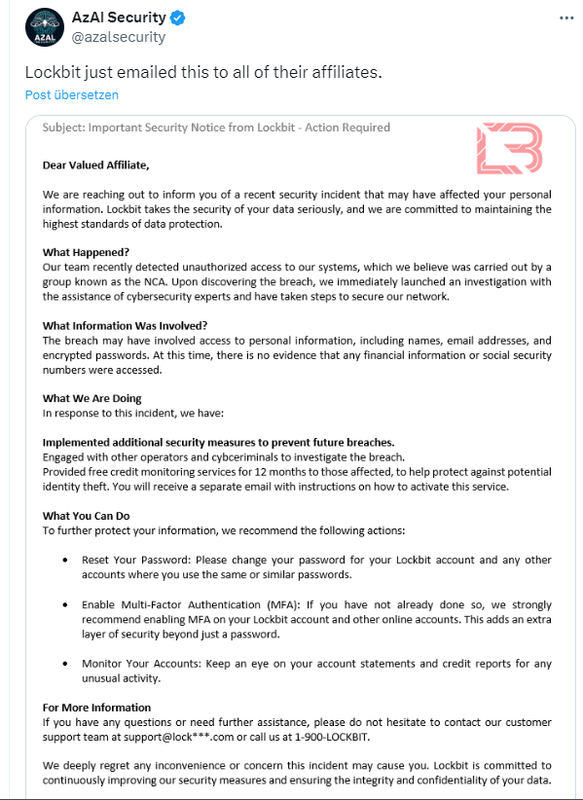
In a message to its "partners" (see tweet above), the LockBit group seems to confirm the action to its affiliates (partners). Here is the message in the original text, which reads somewhat bizarrely.
Subject: Important Security Notice from Lockbit – Action Required Dear Valued Affiliate,
We are reaching out to inform you of a recent security incident that may have affected your personal Information. Lockbit takes the security of your data seriously, and we are committed to maintaining the highest Standards of data protection.
What Happened?
Our team recently detected unauthorized access to our Systems, vvhich we believe was carried out by a group known as the NCA. Upon discovering the breach, we immediately launched an investigation with the assistance of cybersecurity experts and have taken Steps to secure our network.
What Information Was Involved?
The breach may have involved access to personal information, including names, email addresses, and encrypted passwords. At this time, there is no evidence that any financial information or social security numbers were accessed.
What We Are Doing
In response to this incident, we have:
Implemented additional security measures to prevent future breaches.
Engaged with other operators and cybceriminals to investigate the breach.
Provided free credit monitoring Services for 12 months to those affected, to help protect against potential identity theft. You will receive a separate email with instructions on how to activate this Service.What You Can Do
To further protect your information, we recommend the following actions:
- Reset Your Password: Please change your password for your Lockbit account and any other accounts where you use the same or similar passwords.
- Enable Multi-Factor Authentication (MFA): If you have not already done so, we strongly recommend enabling MFA on your Lockbit account and other online accounts. This adds an extra layer of security beyond just a password.
- Monitor Your Accounts: Keep an eye on your account Statements and credit reports for any unusual activity.
For More Information; If you have any questions or need further assistance, please do not hesitate to contact our customer support team at support(S>lock***.com or call us at 1-900-LOCKBIT.
We deeply regret any inconvenience or concern this incident may cause you. Lockbit is committed to continuously improving our security measures and ensuring the integrity and confidentiality of your data.
Sincerely,
The Lockbit Team
In essence, it confirms that third parties have accessed the LockBit infrastructure. The abbreviation NCA stands for National Crime Agency (police authorities in Great Britain), which the group assumes has taken control. Most of the message reads like real satire, as the senders of the message have copied the usual announcements made by their victims when the group has struck.
It states that they "would like to inform you of a recent security incident that may have affected your personal data. Lockbit takes the security of your data very seriously and we are committed to maintaining the highest standards of data protection." After the intrusion was discovered, the company immediately launched an investigation with the help of cybersecurity experts and took steps to secure its own network.
"Personal data may have been accessed during the breach, including names, email addresses and encrypted passwords. At this time, there is no indication that financial data or social security numbers were accessed," it says. People are definitely showing a sense of humor.
Who is LockBit?
Lockbit is a Russian-speaking group that operates ransomware-as-a-service. The group first became known in 2019 through a malware called ABCD. The Lockbit ransomware has been around since 2020 and also has an affiliate program. Security researchers now refer to Lockbit 2.0 and Lockbit 3.0 to designate the individual versions of the ransomware. The group is held responsible for numerous cyber incidents (the linked Wikipedia article names victims, and there are also numerous posts about victims of the group here on the blog). Individual members of the group have already been indicted (in absentia) by the US judiciary. A bounty of 10 million US dollars has been placed on the head of Russian hacker Mikhail Pavlovich Matveev.
Press release and decryptor published
Addendum: The press releases from the US prosecutors are now online. And Europol has published this message, Eurojust has published this statement. There is some additional information in these press releases. Two suspects were arrested in Poland and Ukraine and 200 cryptocurrency accounts were seized. The decryption tools for the group's victims are now being offered on No More Ransome.
Assessment from CheckPoint
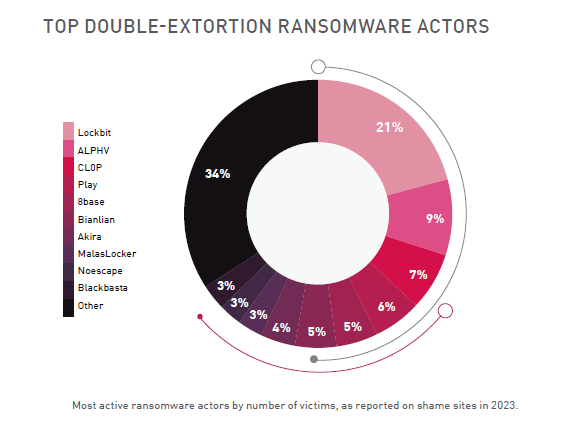
I received the following information from Check Point: In 2023, LockBit was the most dominant ransomware group in terms of the number of publicly extorted victims, publishing more than 1000 extorted organizations. The countries most affected by this group are the US, UK, France, Germany and Canada. The most affected industries are manufacturing (almost 25% of victims) and retail.
Check Point sent me the following list of Lockbit attacks on various victims, organized by country.
Published Victims in 2023
- United States of America: 396
- United Kingdom: 65
- France: 51
- Germany: 43
- Canada: 42
- Italy: 35
- Spain: 25
- India: 22
- Australia: 21
- Brazil: 21
- Thailand: 18
- Mexico: 17
- Netherlands: 16
- Japan: 15
- Malaysia: 15
- Belgium: 13
- Israel: 13
- Taiwan: 12
- China: 10
- United Arab Emirates: 10
- Austria: 9
- South Africa: 9
- Hong Kong: 8
- Egypt: 7
- Portugal: 7
- Singapore: 7
- Argentina: 6
- Colombia: 6
- Peru: 6
- Switzerland: 6
- Turkey: 6
- Vietnam: 6
- South Korea: 5
- Indonesia: 4
- Kuwait: 4
- Philippines: 4
- Romania: 4
- Sweden: 4
- Chile: 3
- Costa Rica: 3
- Luxembourg: 3
- Namibia: 3
- Norway: 3
- Qatar: 3
- Saudi Arabia: 3
- Czech Republic: 2
- Czechia (Czech Republic): 2
- Greece: 2
- Guatemala: 2
- Lebanon: 2
- Poland: 2
- Tunisia: 2
- Uruguay: 2
- Venezuela: 2
- Albania: 1
- Angola: 1
- Bulgaria: 1
- Burkina Faso: 1
- Croatia: 1
- Denmark: 1
- Ecuador: 1
- Fiji: 1
- Finland: 1
- Haiti: 1
- Iceland: 1
- Iran: 1
- Ireland: 1
- Jamaica: 1
- Jordan: 1
- Kenya: 1
- Macedonia: 1
- Monaco: 1
- Morocco: 1
- Myanmar: 1
- Nicaragua: 1
- Oman: 1
- Panama: 1
- Paraguay: 1
- Senegal: 1
- Slovakia: 1
- Trinidad and Tobago: 1
Last month, LockBit support staff were involved in a major dispute on a leading Russian underground forum and were banned from all activities there for questionable business ethics. After being banned from the two major Russian hacking forums, Check Point says this action is another significant disruption to LockBit operations.
Check Point's experts believe that the combination of these two factors will have a major impact on LockBit's operations. This is especially true in terms of reputation, and that those behind it will have considerable difficulty recruiting and retaining partners to deploy this ransomware. Usually such successful groups do not disappear, so we can expect some kind of rebranding.
LockBit's talk with vx-underground
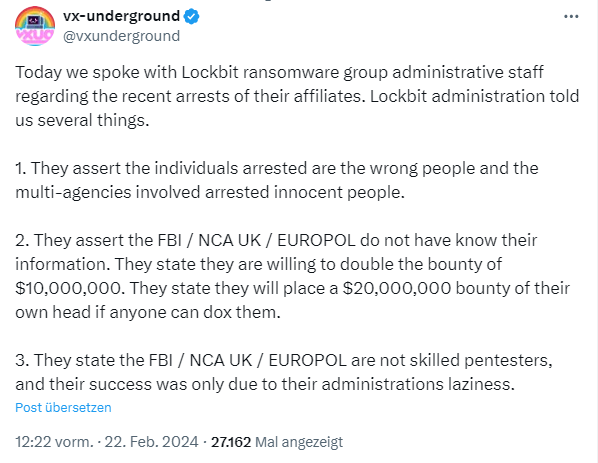
The administrators of the Lockbit ransomware group have allegedly contacted vx-underground. In the following tweet, vx-underground provides some information.
The administrators of the Lockbit ransomware group claim that the people arrested are the wrong people. However, I find the claim that the authorities involved have arrested innocent people less credible – it is possible that the people arrested are not part of the LockBit core.
At the same time, the ransomware group has offered a bounty of 20 million US dollars for the person who succeeds in exposing the heads of the group. People are very sure that they will not be discovered. Furthermore, the administrators claim that the FBI / NCA UK / EUROPOL have no capable pentesters. The success of the investigation is due to the laziness of their administrators. This was the only way the investigators managed to penetrate the infrastructure.
Similar articles:
Shimano is a victim of the Lockbit 3.0 ransomware (Nov. 2023)
Accenture victim of Lockbit ransomware
Nagoya port (Japan) victim of Lockbit 3.0
Russian-Canadian lockbit affiliate arrested in Canada
Lockbit attackers abuse Windows Defender to load Cobalt Strike