[German]Does anyone use Screenconnect from the provider ConnectWise? A critical vulnerability (CVSS 3.1 10.0) has been discovered in the remote desktop software, which should be closed immediately. An initial exploit for this vulnerability is already available. Here is a quick overview for administrators who are responsible for or manage the use of this software. I would say: The roof is on fire. Addendum: 2,866 vulnerable instances in the USA.
[German]Does anyone use Screenconnect from the provider ConnectWise? A critical vulnerability (CVSS 3.1 10.0) has been discovered in the remote desktop software, which should be closed immediately. An initial exploit for this vulnerability is already available. Here is a quick overview for administrators who are responsible for or manage the use of this software. I would say: The roof is on fire. Addendum: 2,866 vulnerable instances in the USA.
Advertising
ConnectWise ScreenConnect
ConnectWise Control, formerly Screenconnect, is a self-hosted remote desktop software application. It was originally developed by Elsinore Technologies in 2008 under the name ScreenConnect and is now owned by ConnectWise Inc. who claim to be the leading provider of IT software for the industry. Their products are therefore likely to be in use in companies.
Critical ConnectWise vulnerability
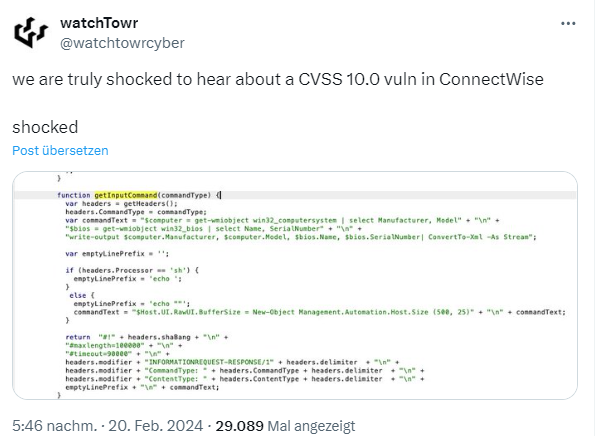
I had heard in passing that there were problems with the product. I just came across the following tweet, which addresses the vulnerability in ConnectWise with a CVSS 10.0.
As of February 19, 2024, ConnectWise has released this security advisory for ScreenConnect 23.9.8 and provided a security fix. Vulnerabilities were reported to the manufacturer as of February 13, 2024.
- CWE-288 Bypass authentication via an alternate path or channel
- CWE-22 Illegal restriction of a path name to a restricted directory ("path traversal")
The vulnerabilities rated as critical allow remote code execution without authentication. ScreenConnect 23.9.7 and earlier are affected, and customers using the solution on-premises must install an update to ScreenConnect 23.9.8. The cloud solution has been patched by the provider.
Advertising
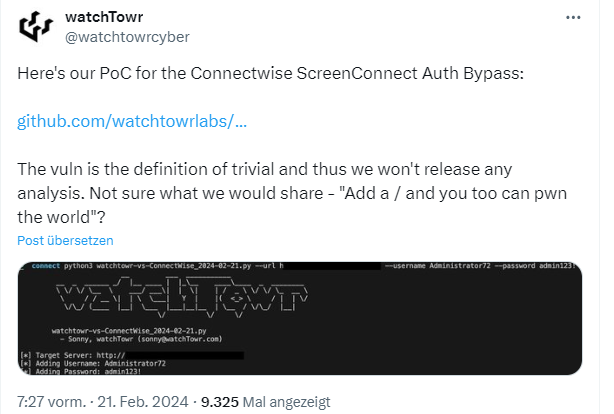
Addendum: On Github is this entry from watchTowr showing in a Proof of Concept, how trivial the vulnerability can be abused.
As of February 20, 2024, ConnectWise has expanded the security notice and writes that it has received information about compromised accounts that have been investigated and confirmed by the Incident Response Team. The following IP addresses were recently used by threat actors.
155.133.5.15
155.133.5.14
118.69.65.60
In the ConnectWise documents, one vulnerability is given a CVSS score of 8.4, while the second vulnerability has been given a CVSS score of 10.0 as the highest risk level. ConnectWise has provided this page with information about the update.
In the above tweet, security researchers from watchWor point to a proof of concept (PoC) for exploiting the vulnerability, which was published on GitHub.
Security researcher from Huntress warns in the blog post A Catastrophe For Control: Understanding the ScreenConnect Authentication Bypass (CVE-2024-1709 & CVE-2024-1708) of the vulnerability and the consequences.
In the tweet below, Shadowserver points out that it has found 3800 vulnerable ConnectWise ScreenConnect instances (authentication bypass via an alternative path or channel (CVSS 10) and path bypass (CVSS 8.4)).
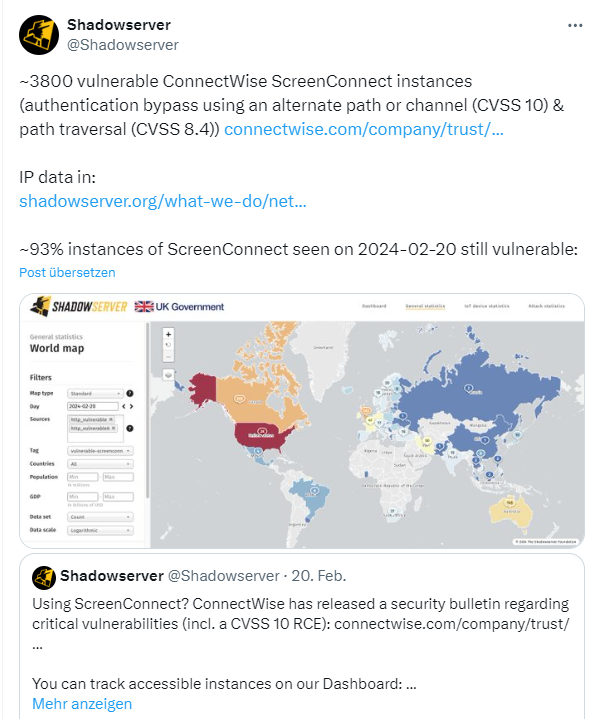
The instances can be viewed on this page. In the USA there are 2,866 instances that will soon be able to "look forward to a visit".