 [German]The security experts at Tenable have discovered a vulnerability in Microsoft Azure that they classify as critical. However, Microsoft has announced that it does not intend to patch this vulnerability, which affects more than ten Azure services. This means that the vulnerability will not be closed.
[German]The security experts at Tenable have discovered a vulnerability in Microsoft Azure that they classify as critical. However, Microsoft has announced that it does not intend to patch this vulnerability, which affects more than ten Azure services. This means that the vulnerability will not be closed.
Vulnerability in Azure
Thise case reminds me of what I wrote about in the blog post Microsoft as a Security Risk? Azure vulnerability unpatched since March 2023, heavy criticism from Tenable – Part 2, severe criticism from Tenable – Part 2. At the time, Microsoft patched the vulnerability after public criticism (see Microsoft has fixed Azure vulnerability faster (in August 2023) after Tenable criticism).
Tenable's Cloud Research Team has now discovered a new vulnerability in Azure that has been classified as critical. According to a Tenable statement, the vulnerability affects the following Azure services.
- Azure Application Insights
- Azure DevOps
- Azure Machine Learning
- Azure Logic Apps
- Azure Container Registry
- Azure Load Testing
- Azure API Management
- Azure Data Factory
- Azure Action Group
- Azure AI Video Indexer
- Azure Chaos Studio
Azure Service Tags and Firewall
The vulnerability affects Azure customers whose firewall rules are based on Azure Service Tags. Azure Service Tags simplify network isolation within Azure by grouping specific IP ranges of Azure services. These tags can be used to define network security rules and apply these rules consistently to multiple Azure resources. Essentially, Azure service tags provide a convenient way to manage access controls, such as firewall rules or network security group (NSG) configurations.
However, according to Tenable, the vulnerability in Azure allows an attacker to bypass Azure Service Tags based firewall rules. To do this, the attacker must forge a request from trusted services. The security researchers write that a threat actor could abuse service tags accepted by the user firewall if no additional validation mechanisms are in place.
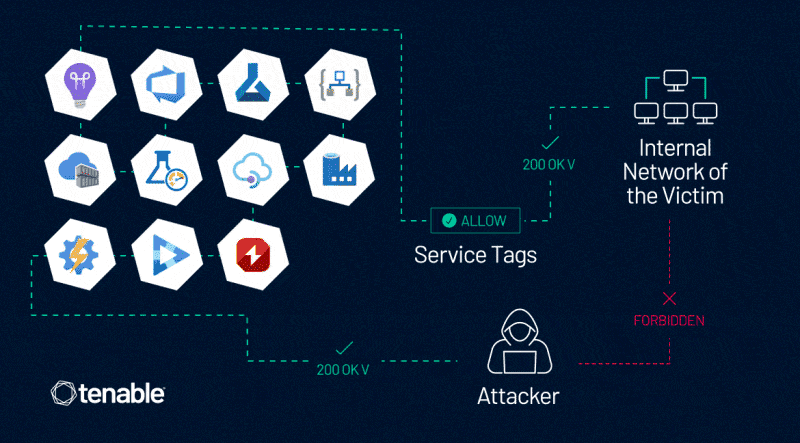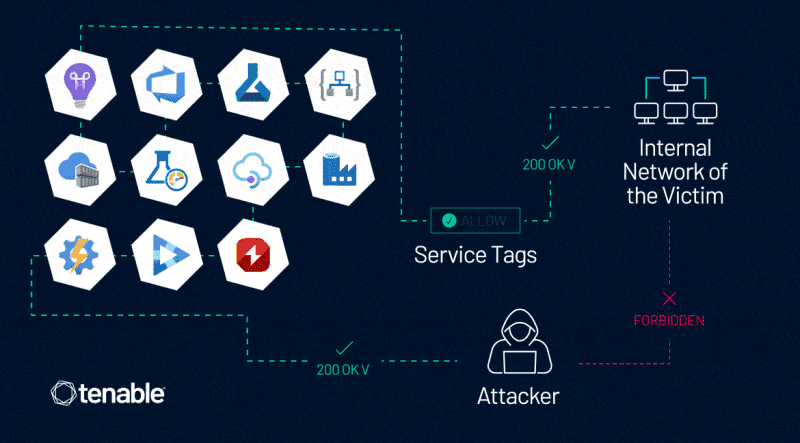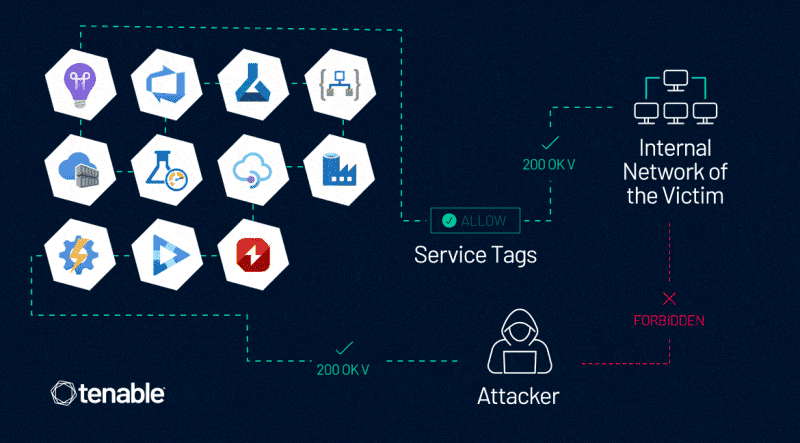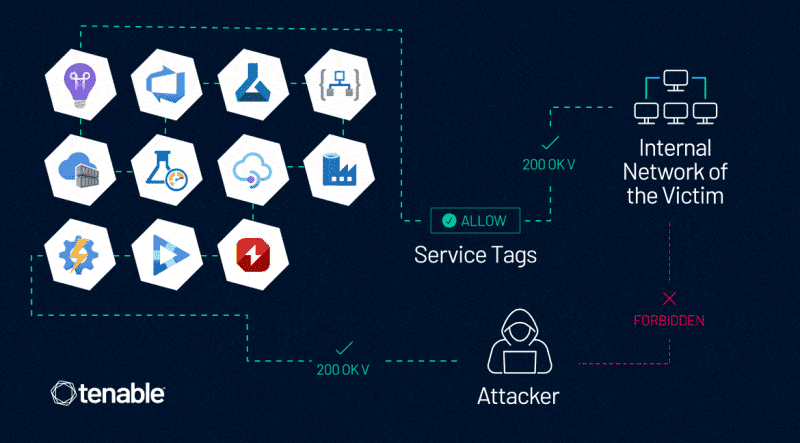
Azure Firewall bypassing, Source: Tenable
By exploiting this vulnerability, an attacker could gain access to an organization's Azure service and other internal and private Azure services. "This vulnerability allows an attacker to control server-side forged requests and impersonate trusted Azure services," explains Liv Matan, Senior Research Engineer at Tenable. Tenable has described the details of this vulnerability in the blog post These Services Shall Not Pass: Abusing Service Tags to Bypass Azure Firewall Rules (Customer Action Required) beschrieben.
Reported in January 2024
Tenable reported this discovery to Microsoft on January 24, 2024 and received confirmation from the Microsoft Security Response Center (MSRC) on January 31, 2024 that the behavior was classified as an "Elevation of Privilege" with a severity level of "Important". Tenable also collected a bug bounty for the report. By February 2, 2024, the MSRC will create a comprehensive plan to fix the vulnerability and a timeline for implementation.
Microsoft does not want to patch
But anyone who thinks a patch is coming soon is mistaken. On February 26, 2024, those responsible at the MSRC decided to fix the problem by comprehensively updating the documentation and to address other variants of the vulnerability there. I do not know what internal reasons and technical constraints led to Microsoft's decision. A coordinated disclosure was then made by Tenable on June 3, 2024.
Azure customers must react
Azure customers whose firewall rules are based on Azure Service Tags are at risk from this vulnerability. Since Microsoft will not release a patch for this vulnerability, these Azure customers must act promptly. Tenable recommends this:
- First, analyze the network rules in your Azure environment for each associated service, look for the use of service tags, and filter the affected services. For the affected services, assume that these resources are public.
- To protect these resources, add authentication and authorization levels for them.
Tenable notes that when configuring network rules for Azure services, administrators keep in mind that service tags are not a watertight means of securing traffic to a private service. If administrators ensure that strong network authentication is maintained, users can protect themselves with an additional and crucial layer of security. In this case, even an attacker exploiting the vulnerability to reach the target endpoint would have great difficulty exploiting this access.
Microsoft has compiled a centralized documentation to inform customers about the use of service tags. Tenable writes: "We strongly recommend that our customers take immediate action. Strong network authentication provides users with an additional and critical layer of security." Customers should take immediate action to ensure they are protected by strong authentication and authorization.
More information, including the team's technical findings and proof of concept, can be found in the Tenable Blog and Technical Advisory. Microsoft has published the article Improved Guidance for Azure Network Service Tags dated June 3, 2024.



