[German]After Microsoft's e-mail system (Exchange Online, Outlook.com) was compromised by Russian hackers from the state sponsored group Midnight Blizzard Hackers, Microsoft recently had to admit that e-mails to customers were also affected. In an attempt to inform customers, Microsoft made the next blunder. The notifications were sent to the "Global Administrators" of the tenants of the affected companies. Notifications were not retrieved or ended up in the spam folder, or were classified as SPAM because Microsoft made further cardinal errors.
[German]After Microsoft's e-mail system (Exchange Online, Outlook.com) was compromised by Russian hackers from the state sponsored group Midnight Blizzard Hackers, Microsoft recently had to admit that e-mails to customers were also affected. In an attempt to inform customers, Microsoft made the next blunder. The notifications were sent to the "Global Administrators" of the tenants of the affected companies. Notifications were not retrieved or ended up in the spam folder, or were classified as SPAM because Microsoft made further cardinal errors.
Midnight Blizzard hack also affected customers
A brief review of what it's all about: In January 2024, it became known that hackers from the state group Midnight Blizzard hackers were able to penetrate Microsoft's email system and read messages from executives or security experts. The hackers had been in the system since November 2023, as I noted in the blog post Microsoft hacked by Russian Midnight Blizzard; emails exfiltrated since Nov. 2023.
The hack was allegedly carried out via an old test account without MFA, from where the attackers were able to access Microsoft's email system. The question is how a password spray attack on an old, non-productive test tenant account was possible and no multi-factor authentication (MFA) was used there. And the question arose as to how the attackers were able to gain access to product systems, i.e. Microsoft's email system, from this test account.
In the blog post How Midnight Blizzard hackers were able to penetrate Microsoft's email system, I traced the hackers' attack path. It points to a chain of omissions on Microsoft's part. But Redmond played it down and said "danger recognized, danger averted, the hackers from Midnight Blizzard have been successfully locked out". Microsoft later had to admit that the attacks by Midnight Blizzard were continuing – but it remained unclear whether the attackers were still able to access Microsoft's systems. However, it became known that the group was able to extract source code (see Microsoft confirms: Russian spies (Midnight Blizzard) stole source code while accessing systems).
The latest information on the case in question can be found in the blog post Microsoft: News from the Midnight Blizzard hack – customers may also be affected, where Microsoft had to admit that customers were also affected by this hack. This is because the attackers were able to read emails from Microsoft employees to customers. There is a risk that the emails could contain information for the attackers that could put customers at risk. It's not a problem, Microsoft wants to inform the customers concerned.
In my last blog post, I asked whether any of our readers had received such an email. The response was zero – were there no readers among them? That is currently unclear! What is clear, however, is that Microsoft is failing to secure its cloud infrastructure and is constantly coming up with new errors and omissions. Microsoft doesn't even get customer notifications right.
Customer notifications send to nirvana
A few hours ago, Patrick S. emailed me to draw my attention to the next Microsoft thigh-slapper and suggested that it might make sense to add the relevant information to my article Microsoft: News from the Midnight Blizzard hack – customers may also be affected. Patrick pointed out that Microsoft sent the notification emails to customers that they were affected by the hack to the tenant's global admins. He said that ideally these admins would not have a mailbox.
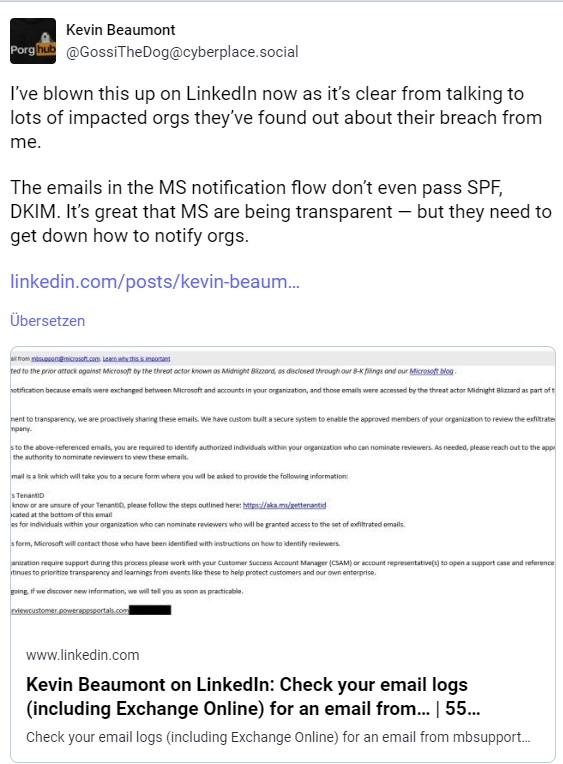
It was uncovered by security researcher Kevin Beaumont in a post on Microsoft's career network LinkedIn. There, he advises Microsoft cloud customers to check their email logs (including Exchange Online) for an email from mbsupport@microsoft.com. Microsoft had communicated a security breach by Russia (specifically Midnight Blizzard) that affected customer data in a somewhat peculiar way. They did not follow the process that is normally used for data protection incidents affecting Microsoft 365 customer data (a status message is then posted in the administrator portal).
Mail to Global Admins …
Microsoft has sent the notification by e-mail to the administrator accounts of the respective tenant (according to Patrick the Global Administrators). The emails may end up in the spam folder. Global Administrator accounts of tenants should also be Breakglass accounts without email. Also, they have not informed the organizations about the account administrators.
Breakglass accounts are emergency accounts in Azure Entra ID that are equipped with increased rights (Global Admins). Such accounts allow access to resources if there are problems with availability. Break Glass accounts must therefore be protected by strict security rules and protocols. This includes ensuring that these accounts do not have an email address.
Mail without SPF and DKIM, with self-signed certificate
On LinkedIn, the comments on Kevin Beaumont's post are full of users. One administrator wrote that several of his customers had received this email. All of these customers were concerned that it was phishing.
- According to the email headers, Microsoft did not use SPF and DKIM,
- and the URL mentioned in the email message was hosted as a simple (almost fake) Azure PowerApp with a simple DV SSL certificate.
You have to let it melt in your mouth: Although the certificate was issued by another trusted certificate authority, it did not contain any information about the organization for which the certificate was issued. All other MS domains have OV/EV certificates issued by Microsoft as a publicly trusted certification authority.
The commenting administrator says: "At first glance, this did not inspire confidence in the recipients, who asked in forums or contacted Microsoft customer support to finally confirm that the email was legitimate. In the Microsoft Answers forum, there is a post Midnight Blizzard Data Sharing Request – Email Legitimacy? dated June 25, 2024, where someone asks about the email:
Action Required – Microsoft Email Data Sharing Request
"This notification is related to the prior attack against Microsoft by the threat actor known as Midnight Blizzard, as disclosed through our 8-K filings and our Microsoft blog .
You are receiving this notification because emails were exchanged between Microsoft and accounts in your organization, and those emails were accessed by the threat actor Midnight Blizzard as part of their cyber-attack on Microsoft.
As part of our commitment to transparency, we are proactively sharing these emails. We have custom built a secure system to enable the approved members of your organization to review the exfiltrated emails between Microsoft and your company.
In order to grant access to the above-referenced emails, you are required to identify authorized individuals within your organization who can nominate reviewers. As needed, please reach out to the appropriate parties in your organization who have the authority to nominate reviewers to view these emails.
At the bottom of this email is a link which will take you to a secure form where you will be asked to provide the following information:
- Your organization's TenantID
o If you do not know or are unsure of your TenantID, please follow the steps outlined here: https://aka.ms/gettenantid- The access code located at the bottom of this email
- The email addresses for individuals within your organization who can nominate reviewers who will be granted access to the set of exfiltrated emails.
Once you complete this form, Microsoft will contact those who have been identified with instructions on how to identify reviewers.Should you or your organization require support during this process please work with your Customer Success Account Manager (CSAM) or account representative(s) to open a support case and reference Microsoft Email Data Sharing. Microsoft continues to prioritize transparency and learnings from events like these to help protect customers and our own enterprise.
Our investigation is ongoing, if we discover new information, we will tell you as soon as practicable."
Secure Link: https://purviewcustomer.powerappsportals.com/?dnaynpyvmule
As the administrator notes in his comment: "A strange way for a provider like this to communicate an important problem to potentially affected customers."
On Mastodon, Beaumont writes (see screenshot above) that many companies and those affected only became aware of the notification through his post. And in another post on Mastodon, Beaumont writes:
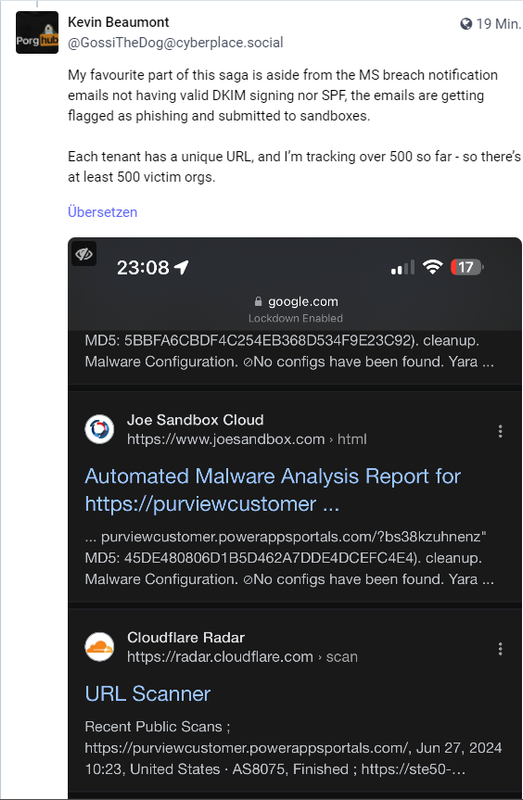
The best part of this story is that the MS notification emails do not have a valid DKIM signature or SPF, but are flagged as phishing emails and forwarded to sandboxes.
Each client has a unique URL, and I've tracked over 500 so far – so there are at least 500 organizations that have fallen victim to the Midnight Blizzard hack.
And with that, administrators of Microsoft tenants from the readership can start searching for such an email. Maybe someone will find it. I'm just end the story here with: "Another day, another fail by Microsoft".
Similar articles:
China hacker (Storm-0558) accessed Outlook accounts in Microsoft's cloud
Follow-up to the Storm-0558 cloud hack: Microsoft is still in the dark
After CISA report on Storm-0558 hack, Microsoft provides customers with enhanced cloud logging
Stolen AAD key allowed (Storm-0558) wide-ranging access to Microsoft cloud services
Microsoft's Storm-0558 cloud hack: US senator among the victims
Microsoft's Storm-0558 cloud hack: MSA key comes from Windows crash dump of a PC
Microsoft extends Purview logging (after Storm-0558 hack)
Microsoft hacked by Russian Midnight Blizzard; emails exfiltrated since Nov. 2023
How Midnight Blizzard hackers were able to penetrate Microsoft's email system
Microsoft confirms: Russian spies (Midnight Blizzard) stole source code while accessing systems
Microsoft: News from the Midnight Blizzard hack – customers may also be affected
Hewlett Packard Enterprise (HPE) hacked by Midnight Blizzard since May 2023
Microsoft as a Security Risk? U.S. senator calls for Microsoft to be held accountable over Azure cloud hack– Part 1
Microsoft as a Security Risk? Azure vulnerability unpatched since March 2023, heavy criticism from Tenable – Part 2
Whistleblower: Microsoft ignored warnings about AD bug; was exploited in 2020 SolarWinds hack
Microsoft engages in damage limitation at congressional hearing (13.6.2024): Safety takes priority over AI