[German]There are several critical vulnerabilities in the CUPS printing system, which is used under Linux and Unix. Under certain circumstances, these can be used for remote code execution (RCE) attacks.
[German]There are several critical vulnerabilities in the CUPS printing system, which is used under Linux and Unix. Under certain circumstances, these can be used for remote code execution (RCE) attacks.
What is CUPS?
The abbreviation CUPS stands for Common Unix Printing System. It is an open source printing system that functions as a daemon that enables printing under the various Unix operating systehttps://de.wikipedia.org/wiki/Common_Unix_Printing_Systemms as well as under OS/2/EComStation.
It was developed by Michael Sweedt, who released the first version in 1999. In 2007, Sweedt was hired by Apple and the company also acquired the rights to CUPS. The commercial version of CUPS was then discontinued. Apple therefore also relies on CUPS in macOS, iOS and iPadOS. Since 2017, CUPS has been distributed under the Apache license and can also be used in Windows.
Vulnerabilities in CPUS
Italian-based developer Simone Margaritelli (currently working at DataFlow Forensic), who publishes under the alias evilsocket and who claims to be involved in the development of CUPS, has uncovered several vulnerabilities in CUPS.
On September 26, 2024, he published Part I of his findings on evilsoft.net in the article Attacking UNIX Systems via CUPS, Part I. A chain of vulnerabilities CVE-2024-47076 (libcupsfilters), CVE-2024-47175 (libppd), CVE-2024-47176 (cups-browsed) and CVE-2024-47177 (cups-filters) allows attackers to execute arbitrary code remotely on vulnerable computers under certain conditions.
For example, the cups-browsed daemon searches the network for shared printers. To do this, the daemon listens for responses on UDP port 631 and, by default, allows remote connections from any device to create new printer connections.
Margaritelli found a vulnerability during the analysis, so he was able to create a PostScript Printer Description (PPD) printer that is manually passed to an open service browsed by cups running on UDP port 631.
A computer automatically makes this printer available for remote printing. If an attacker succeeds in creating a malicious (PPD) printer, they can remotely execute malicious commands on the local machine.
To do this, an unauthenticated remote attacker only needs to replace the IPP URLs of existing printers (or new printers) with a malicious one without being noticed. This can be used to execute arbitrary commands on the local computer by starting a print job from that computer.
In the WLAN, a remote attacker can send a UDP packet to port 631, possibly via the Internet. No authentication takes place. A local attacker can forge the zeroconf, mDNS and DNS-SD announcements in the local network in order to reach the same code path that leads to the RCE, writes the discoverer. Simone Margaritelli has named the following vulnerabilities in his article:
- CVE-2024-47176 | cups-browsed <= 2.0.1 binds to UDP INADDR_ANY:631 and relies on an arbitrary packet from an arbitrary source to trigger a Get-Printer-Attributes IPP request to an attacker-controlled URL.
- CVE-2024-47076 | libcupsfilters <= 2.1b1 cfGetPrinterAttributes5 does not validate or sanitize IPP attributes returned by an IPP server, resulting in attacker-controlled data being served to the rest of the CUPS system.
- CVE-2024-47175 | libppd <= 2.1b1 ppdCreatePPDFromIPP2 vdoes not validate or sanitize the IPP attributes when they are written to a temporary PPD file, allowing attacker-controlled data to be injected into the resulting PPD.
- CVE-2024-47177 | cups-filters <= 2.0.1llows arbitrary command execution via the PPD parameter FoomaticRIPCommandLine.
There are said to be other bugs in CUPS. CUPS and in particular the cups-browsed daemon are available for most UNIX systems (GNU/Linux distributions, various BSD systems, ChromeOS, Solaris etc.).
How critical is it?
The vulnerabilities were given a CVS 3.1 score of 9.8, which is actually very critical. But the assessment of exploitability varies greatly. Simone Margaritelli writes that the cups-browsed daemon is activated by default in some cases.
Bleeping Computer states that this daemon is not activated by default. The colleagues quote this RedHat article with a statement on the above vulnerabilities.
All versions of Red Hat Enterprise Linux (RHEL) are affected by CVE-2024-47076, CVE-2024-47175, CVE-2024-47176 and CVE-2024-47177, but are not vulnerable in their default configurations.
Red Hat is therefore downgrading these vulnerabilities from Critical to Important. Administrators can remove the vulnerability relatively easily by removing the cups-browsed daemon with the following commands:
$ sudo systemctl stop cups-browsed $ sudo systemctl disable cups-browsed
and prevents a start. Red Hat and the Linux developers are currently working on patches to fix these problems. A discussion can also be found on reddit.com.
The discoverer of the vulnerabilities writes: If the system cannot be updated and you rely on this service for some reason, block all traffic to UDP port 631 and possibly all DNS SD traffic (good luck if you use zeroconf).
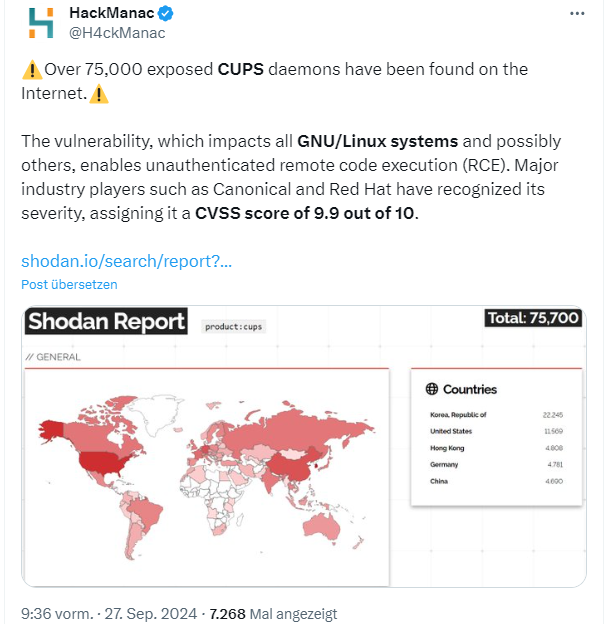
Many CUPS instances accessible on the internet
The following tweet uses figures from Shodan. This search engine finds over 75,000 unprotected CUPS daemons on the Internet that are potentially vulnerable to the Remote Code Execution (RCE) vulnerability.
Security researcher Marcus Hutchins writes on LinkedIn,
that he has revised his scanning technique for identifying vulnerable CUPS servers. Instead of relying on Shodan data, he has conducted his own internet-wide scan using a distributed network of servers.
The scanner sends a probe message to UDP port 631, which, if successfully received by a system running the cups-browsed daemon, causes the system to initiate an outbound connection to Hutchins' web servers.
Only unique IP addresses that reached his web server with valid CUPS requests were counted as potentially "vulnerable". This allowed him to discover drastically more exposed instances of CUPS. He writes of a total of 107,287 systems.