[German]Short addendum to an old topic. Microsoft recently announced that NTLMv1 has been removed from Windows 11 24H2 and Windows Server 2024. This step had been announced by Microsoft for a long time. Here is another look at the topic with some information on what users should know.
[German]Short addendum to an old topic. Microsoft recently announced that NTLMv1 has been removed from Windows 11 24H2 and Windows Server 2024. This step had been announced by Microsoft for a long time. Here is another look at the topic with some information on what users should know.
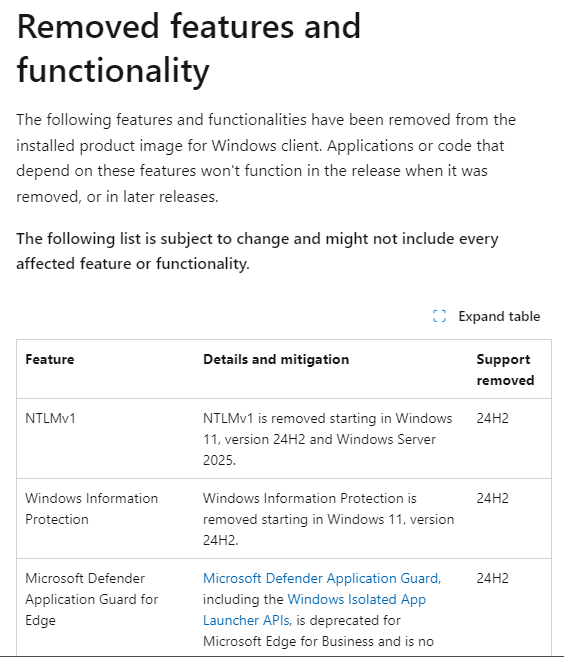
NTLMv1 has been removed
It was a very brief announcement that Microsoft published a few days ago on the support page for removed features. There you will find the note "NTLMv1 is removed starting in Windows 11, version 24H2 and Windows Server 2025."
This step came as no surprise, as Microsoft announced in early June 2024 that NTLM would be retired and removed in future Windows versions (Windows: NTLM and Driver Verifier GUI declared as deprecated).
All versions of NTLM, including LANMAN, NTLMv1 and NTLMv2, have not been in active functional development since then and are obsolete. The use of NTLM should continue to work in Windows Server 2025 and Windows 11 24H2. If necessary, the removed NTLMv1 support can be added again in this operating system via features and functions.
However, Microsoft writes that NTLM calls will be replaced by Negotiate calls. Negotiate attempts to authenticate with Kerberos and only uses NTLM if necessary.
Security reasons lead to the replacement of NTLM
NTLM is the abbreviation for Windows New Technology LAN Manager and comprises a collection of security protocols for authentication from Microsoft. Its origins date back to the 1990s, when NTLM was introduced as a proprietary protocol at Microsoft.
Thanks to reverse engineering, third-party products such as Samba, Squid, Mozilla Firefox, cURL, Opera and the Apache HTTP Server now also support this protocol. At the beginning of 2007, Microsoft published its specification under pressure from the United States and the European Union.
NTLM is no longer considered secure and should no longer be used if possible. Due to further security problems, NTLMv2 was developed and the earlier version was henceforth called NTLMv1. NTLMv2 is also known to have security problems.
Microsoft now uses Kerberos authentication as an alternative. If not already done, administrators will find instructions from Microsoft in this support article for NTLM auditing and for investigate how NTLM is being used. In this support article, Microsoft describes how a minimal NTLM version can be enforced via SMB.
Similar article:
Windows: NTLM and Driver Verifier GUI declared as deprecated
Microsoft rolls out Windows hardening against standard NTLM relay attacks
Microsoft has fixed the (PetitPotam) NTLM Relay Vulnerability (CVE-2022-26925) with Windows May 2022 Update