 [German]DigiEver from Taiwan offers IP video surveillance based on Linux. Security researchers from TXOne discovered RCE vulnerabilities in DigiEver products back in July 2023. The provider does not provide updates because the devices have reached the end of support. Since December 2024, it has been observed that a botnet called Hail Cock has exploited one of these bugs, as the vulnerability is still open. Users must therefore react.
[German]DigiEver from Taiwan offers IP video surveillance based on Linux. Security researchers from TXOne discovered RCE vulnerabilities in DigiEver products back in July 2023. The provider does not provide updates because the devices have reached the end of support. Since December 2024, it has been observed that a botnet called Hail Cock has exploited one of these bugs, as the vulnerability is still open. Users must therefore react.
DigiEver IP video surveillance
DigiEver is a Taiwan-based company that offers IP video surveillance solutions.
There are solutions for recording video streams that are based on hardware and come with a Linux operating system.
Security researchers find vulnerabilities
Security researchers from the OT security specialist TXOne Networks found bugs in DigiEver video surveillance products back in July 2023. The RCE vulnerabilities were reported to TWCERT/CC, but DigiEver closed the relevant "case" in August 2023 on the grounds that the device had been out of date for five years. As a result, two CVE numbers were reserved for these bugs in mid-December 2023.
Unfortunately, this was not the end of the story, as in December 2024 it became known that a botnet called Hail Cock had exploited one of these bugs. This means that the vulnerability still exists.
Two vulnerabilities in DigiEver DVRs
In software versions of DigiEver DVRs (Digiever DS-2105 Pro 3.1.0.71-11), two remote code execution bugs were found after authentication. The vulnerabilities have been assigned the following CVE numbers:
- CVE-2023-52163, Digiever DS-2105 Pro 3.1.0.71-11 devices allow time_tzsetup.cgi command injection.
- CVE-2023-52164, Digiever DS-2105 Pro 3.1.0.71-11 devices allow arbitrary file reads via access_device.cgi.
To exploit both vulnerabilities, the attacker must be logged into the device and make a manipulated request.
Mirai botnet exploits the vulnerabilities
A Mirai botnet actively exploited these vulnerabilities at the end of 2024. It is not possible to determine exactly which models and versions of DigiEver devices are affected by these attacks.
Remedial measures against the vulnerabilities
As the vulnerabilities listed above can only be exploited after authentication, operators could implement the following workarounds:
- The device should not be connected to the Internet. A firewall or gateway can be used to protect the management interface of the device.
- The default username and password of the device should be changed.
In addition, txOne network products can detect the above vulnerabilities.
Details of the vulnerabilities
txOne has sent me some details of the vulnerabilities. For example, the DigiEver DVRs use a common code base for different devices. The vulnerabilities were found by the security researchers by analyzing the recovery image that was available on the website.
Upon further investigation, it appears that DigiEver implements a CGI gateway in /cgi-bin/cgi_main.cgi. All functions are mediated through this endpoint and various CGI scripts can be called through this endpoint.
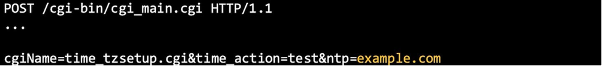 Figure 1: CVE-2023-52163, time_tzsetup.cgi command injection (TXOne Networks Inc.)
Figure 1: CVE-2023-52163, time_tzsetup.cgi command injection (TXOne Networks Inc.)
The flaws can be easily identified as text command injection and arbitrary file reading.
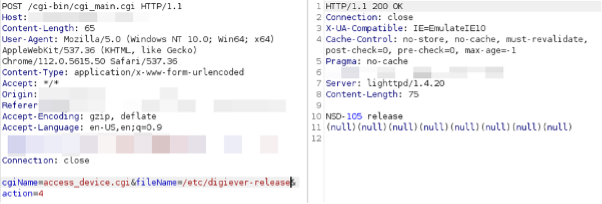
Figure 2: CVE-2023-52164, access_device.cgi Arbitrary file read (TXOne Networks Inc.).
Remediation against exploitation
txOne Networks Inc. provides the following Snort 3 rules to detect exploitation of both vulnerabilities.
Against CVE-2023-52163 (Command Injection):
alert tcp $EXTERNAL_NET any -> $HTTP_SERVERS $HTTP_PORTS (msg:"WEB-CGI Digiever DS-2105 Pro Command Injection"; flow:to_server,established; http_uri; content:"/cgi-bin/cgi_main.cgi"; http_client_body; content:"cgiName=time_tzsetup.cgi"; pcre:"/ntp=[0-9a-zA-Z\.\s]*[|`\;]/"; reference:cve,2023-52163; classtype:web-application-attack; sid:1000001; rev:1;).
Against CVE-2023-52164 (Arbitrary File Read):
alert tcp $EXTERNAL_NET any -> $HTTP_SERVERS $HTTP_PORTS (msg:"WEB-CGI Digiever DS-2105 Authenticated Arbitrary File Read"; flow:to_server,established; http_uri;content:"/cgi-bin/cgi_main.cgi"; http_client_body; content:"cgiName=access_device.cgi"; pcre:"/fileName=(\/|\w+\/\.\./)/"; reference:cve,2023-52164; classtype:web-application-attack; sid:1000002; rev:1;).
Disclosure timeline
With no other options available to the security researchers, they chose to responsibly disclose the two bugs in full after receiving the negative response from the manufacturer via TWCERT/CC. Here is the timeline:
- July 31, 2023: The bugs were reported to TWCERT/CC.
- August 1, 2023: DigiEver closes the case on the grounds that the device has been obsolete for five years.
- Mid-December 2023: CVE identifiers were reserved for the bugs.
- December 19, 2024: Public announcement by Akamai (see this article).
TXOne Networks provides IT security products that ensure the reliability and security of industrial control systems and operational technology environments through the OT Zero Trust methodology.



